Slayer - HackSmarter Walkthrough
Welcome to my comprehensive walkthrough of the Slayer machine from HackSmarter! This penetration testing writeup demonstrates how to enumerate services, leverage RDP access, and escalate privileges through PowerShell history exploitation. Throughout this guide, I’ll be using tools like Nmap and NetExec to compromise this Windows target. Whether you’re preparing for the OSCP or just sharpening your pentesting skills, this walkthrough will provide valuable insights into real-world attack scenarios.
Initial Enumeration
Starting with an Nmap scan to identify open ports and running services:
1 | PORT STATE SERVICE REASON VERSION |
From the scan results, we can see several interesting ports:
- Port 135 (RPC)
- Port 445 (SMB)
- Port 3389 (RDP)
- Port 49670 (Unknown service)
The presence of port 3389 indicates that Remote Desktop Protocol is enabled, which presents an excellent opportunity for lateral movement if we have valid credentials.
RDP Access as tyler.ramsey
Verifying RDP Credentials
Before attempting to connect via RDP, let’s verify whether the credentials work using NetExec (formerly CrackMapExec). Note that this command may take some time to respond:
1 | nxc rdp 10.1.215.177 -u tyler.ramsey -p 'P@ssw0rd!' |
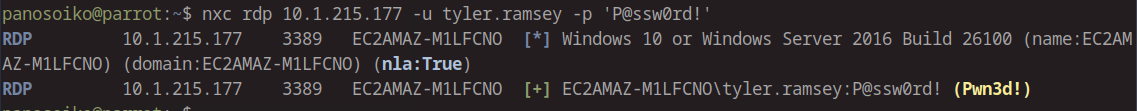
The verification confirms that we have valid RDP credentials for the user tyler.ramsey.
Establishing RDP Connection
Now let’s establish an RDP session using xfreerdp:
1 | xfreerdp /u:tyler.ramsey /p:'P@ssw0rd!' /v:10.1.215.177 /cert-ignore |
Once connected, we successfully gain access to the Windows desktop as tyler.ramsey.
Privilege Escalation via PowerShell History
Discovering Credentials in PowerShell History
After establishing the RDP session, open a PowerShell terminal. Here’s where things get interesting: simply press the UP arrow key to cycle through PowerShell command history. This technique reveals previously executed commands, and in this case, one of them contains the administrator password.
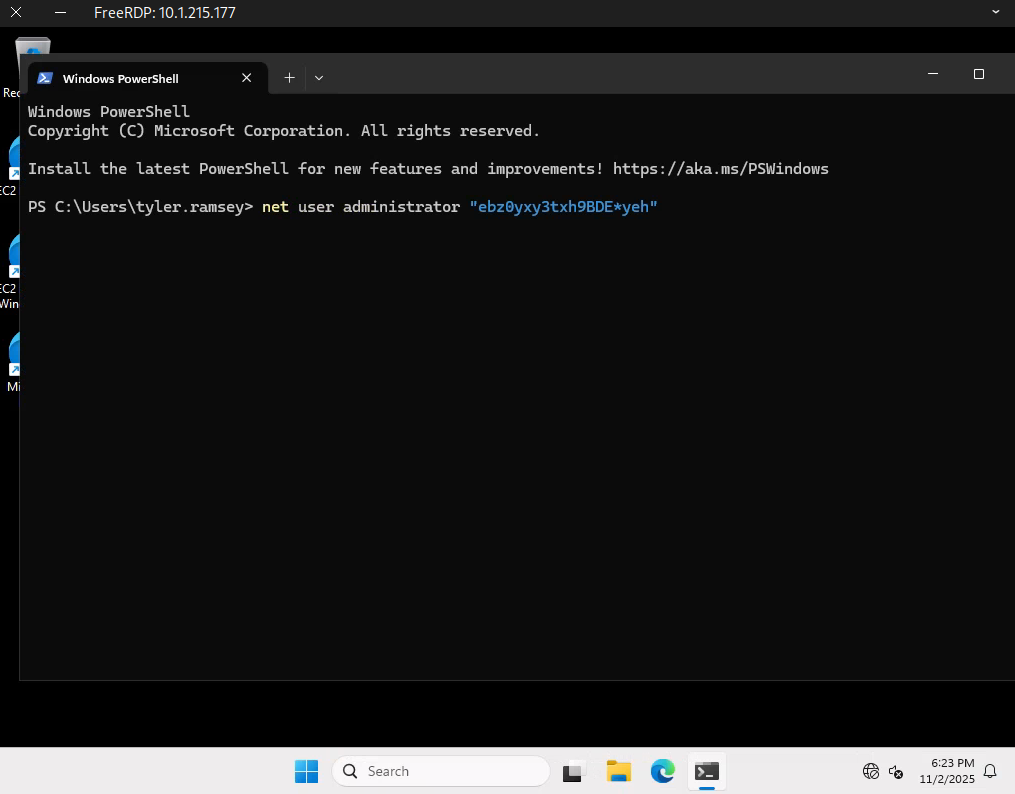
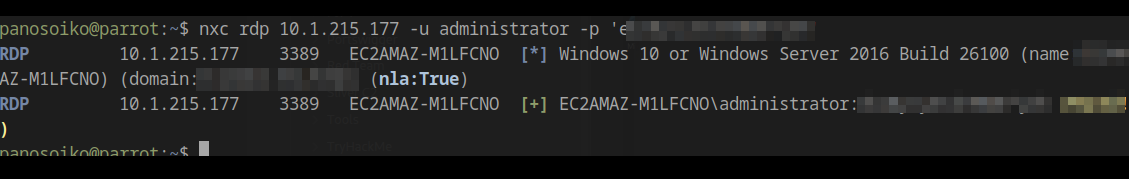
This appears to be an unintended privilege escalation path, as sensitive credentials should never be stored in PowerShell history. However, it’s a common real-world misconfiguration that pentesters frequently encounter during engagements.