Specifications
- EC2 instance –> t2.micro
- OS –> Ubuntu 20.04LTS (Focal Fossa)
- Go Version –> go1.24.4 linux/amd64
- Sliver Version –> v1.5.43
- Mingw Version –> 12.2.0-14+
- Metasploit Version –> 6.4.71-dev-
Firts we need an AWS free if you dont have one search on google “AWS Free account”
and the firts resault will give you the link to create one.
1) Create a budget
We will be crating a daily budget for our account so IF we ever leave our sliver c2 (EC2) running we will get a alert on our mail to go and close it if we dont use it, so we avoid unwanted costs. As we are using t2.micro the free EC2 aws provides us we wont get any big costs so we will set our budget very low just to catch the instance from over running.
There are 2 ways, the “Zero Budget Cost” OR the “Custom budget” option I will be covering the “Custom budget” as the other is just two clicks.
First on the search-bar search for Budgets
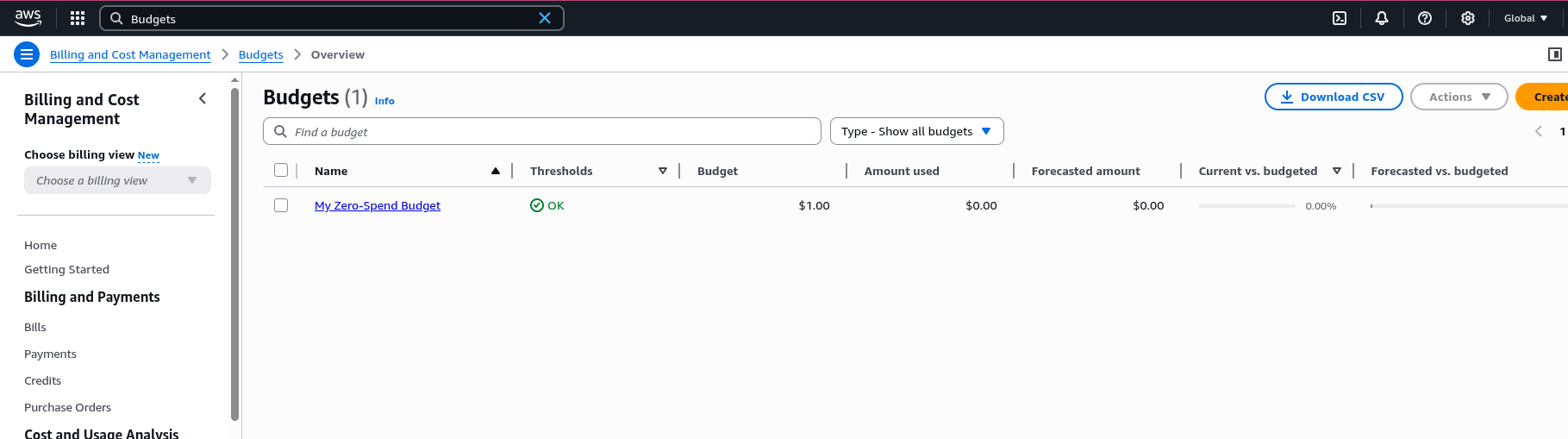
Then click on create a new budget, now the followoing, select “Customize (advanced)” then “Cost budget - Recommended” and click NEXT. Now we input a name like Sliver Budget set our Period to daily and set our budget to 0.10 this depends on your choise of budgeting for me 0.10 is a good number please adjust accordingly to your needs and how save you want to be. OR if you dont want to do the setup just select My Zero-Spend Budget that AWS offers.
2) EC2
Find a region that maches your needs and start and EC2 instance, give it a name, select Debian as the OS, double check it will use t2.micro.Create a Key pair and downlod the file. Now when selecting the security group if you want better OpSec create a security group with yout IP so you can only ssh and access that machine(for now) also allow https and http traffic into it(If you dont want to create a new custom security group just select MY IP)
Now on your machine do sudo chmod 400 <name of key>.pem
Wait for the instance to start and ssh into it using the key you have
1 | ssh -i "<NAME>.pem" admin@<Public IP> |
Go Installation
We need to to be able to install Sliver C2
1 | wget https://golang.org/dl/go1.24.4.linux-amd64.tar.gz |
1 | tar -xf go1.24.4.linux-amd64.tar.gz |
Move the Go binary directory to /usr/local/go:
1 | sudo mv go /usr/local/go |
Add the Go bin directory to your PATH environment variable:
1 | sudo echo 'export PATH=$PATH:/usr/local/go/bin' >> ~/.bashrc |
Reload your .bashrc file to apply changes:
1 | source ~/.bashrc |
Test if the install was succesfull
1 | go version |
Mingw Installation
We need Mingw as it enable shellcode/staged/DLL payloads
1 | sudo apt update |
1 | sudo apt install mingw-w64 |
Metasploit Installation
Metasploit is needed for some integrations for Sliver
Firts some dependencies to run the one liner rabbit7 gives us
1 | sudo apt install -y gnupg2 dirmngr apt-transport-https ca-certificates curl |
then
1 | curl https://raw.githubusercontent.com/rapid7/metasploit-omnibus/master/config/templates/metasploit-framework-wrappers/msfupdate.erb > msfinstall && chmod 755 msfinstall && ./msfinstall |
After the installation completes, open a terminal window and type the following to start msfconsole:
1 | msfconsole |
Source: https://docs.rapid7.com/metasploit/installing-the-metasploit-framework/
Sliver
Now that all that dependencies are installed it was time to download the sliver binaries.
Server:
1 | wget https://github.com/BishopFox/sliver/releases/download/v1.5.43/sliver-server_linux |
Client(for now local)
1 | wget https://github.com/BishopFox/sliver/releases/download/v1.5.43/sliver-client_linux |
And made the binaries executables.
1 | sudo chmod 755 sliver-server_linux |
1 | sudo chown admin:admin sliver-server_linux |
also wourd recommend not to use admin user for this and create another use that runs sliver but for now this does the job.
Next up the verification of these binaries was also necessary. Ideally, it should be done right after downloading binaries.
1 | wget https://raw.githubusercontent.com/BishopFox/sliver/master/server/assets/fs/sliver.asc |
You should see
1 | Good signature from "Sliver <sliver@bishopfox.com>" [unknown] |
Start the sliver server sliver-server_linux and type the following
1 | new-operator --name HelloWorld -l 127.0.0.1 |
Exit the server and now load the .cfg file into the sliver-agent
1 | ./sliver-client_linux import HelloWorld_127.0.0.1.cfg |
Now its a good time to setup a service that will run the sliver-server so we can connect to it
1 | sudo tee /etc/systemd/system/sliver-server.service <<EOF |
Reload the daemon and check the status
1 | sudo systemctl daemon-reload |
1 | sudo systemctl status sliver-server |
Now we can run the sliver agent and we are in
1 | ./sliver-client_linux |
You can stop here id you dont want a Load Balancer and CloudFront if your security group is setup well you can start http/https listeners and send your payloads to your target.
(tip ligolo-ng is a great tool to have for pivoting you can install it also on the EC2 and just expose the port that you will be running it from to the internet). If you want security BUT not the hustle of using a Load Balancer and CloudFront in your security groups allow http/https ports and the ligolo port to be exposed only to the machine IP you are pentesting.
Ligolo setup tutorial:
1. Create an Application Load Balancer (ALB)
- In the EC2 Console, navigate to Load Balancers → Create Load Balancer.
- Choose Application Load Balancer, give it a name, and select your VPC and subnets.
- Under Security Groups, attach (or create) one that allows HTTP/HTTPS from wherever your operators will connect.
2. Define a Target Group
- Still in the Load Balancer wizard, create a new Target Group of type “Instances.”
- Choose the same VPC, set the protocol (HTTP or HTTPS), and click Next.
- Select your Sliver server instance, click Include as pending, then Create target group.
3. Hook the Target Group into the ALB
- Back on the ALB page, under Listeners & routing, add (or edit) a listener on port 80 or 443.
- Point that listener to your newly created Target Group.
- Finish creating the Load Balancer.
4. Update the Sliver Instance’s Security Group
- In Security Groups, find the SG attached to your Sliver instance.
- Edit its inbound rules: add a Custom TCP rule on port 80 (or 443) with the source set to your ALB’s security group.
5. Create a CloudFront Distribution
- In the CloudFront Console, Create Distribution → Web.
- Set Origin Domain to your ALB’s DNS name.
- Restrict viewer protocol to HTTPS Only, and allow all HTTP methods.
- Choose an appropriate cache policy (e.g. “Caching Optimized”), then Create Distribution.
- Copy your new CloudFront domain name—this becomes your public C2 endpoint.
Disclaimer: When fronting Sliver C2 with an AWS Application Load Balancer or CloudFront, only HTTP and HTTPS listeners (ports 80/443) are supported end-to-end. Any other protocol (e.g. raw TCP for mTLS) or non-HTTP(S) port will be rejected or dropped by the proxy layer.
Debugging Tips
Verify Listener Configuration
- In the ALB/CloudFront console, ensure you have an HTTP (80) or HTTPS (443) listener pointing to your Sliver target group.
- If using HTTPS, confirm the certificate is correctly attached and not expired.
Check Security Groups
- ALB SG must allow inbound on 80/443 from your operator IPs.
- Backend instance SG must allow inbound from the ALB’s SG on the same port.
Target Group Health
- In EC2 → Target Groups, confirm your Sliver instance shows as healthy.
- If it’s unhealthy, examine the health-check path/protocol—Sliver C2 typically responds on
/favicon.icoor a custom HTTP path you’ve defined.
Test Connectivity
- From your workstation:
1 | curl -v http://<ALB-DNS>:80/ # HTTPS curl -v https://<ALB-DNS>:443/ --cacert /path/to/ca.pem |
A valid Sliver HTTP(S) listener will return a 200 OK or a small redirection payload.
5. Inspect Logs
* Enable ALB access logs in S3 to see if requests are reaching the load balancer.
* On the Ubuntu host, check journalctl -u sliver-server for any incoming connection or TLS errors.
6. Fallback to Direct Connect
* Temporarily open the instance’s security group to 0.0.0.0/0 on your chosen port and test sliver-client --server https://<EC2-IP>:<port>.